Edge Segmentation is essentially the Security Domain extended from Aviatrix Transit GW (AVX-TR-GW) to AWS-TGW
Edge Segmentation allows you to specify the "Edge Connection" on Aviatrix Transit GW and then which AWS-TGW Security Domain the "Edge Connection" can communicate with.
The drawback of AWS-TGW based Edge Segmentation is that it requires AWS-TGW to be present in the network, hence it only works in cases where customer is only present in AWS.
The best approach is to use global and policy-driven, multi-cloud network segmentation that works in any cloud and not just AWS.
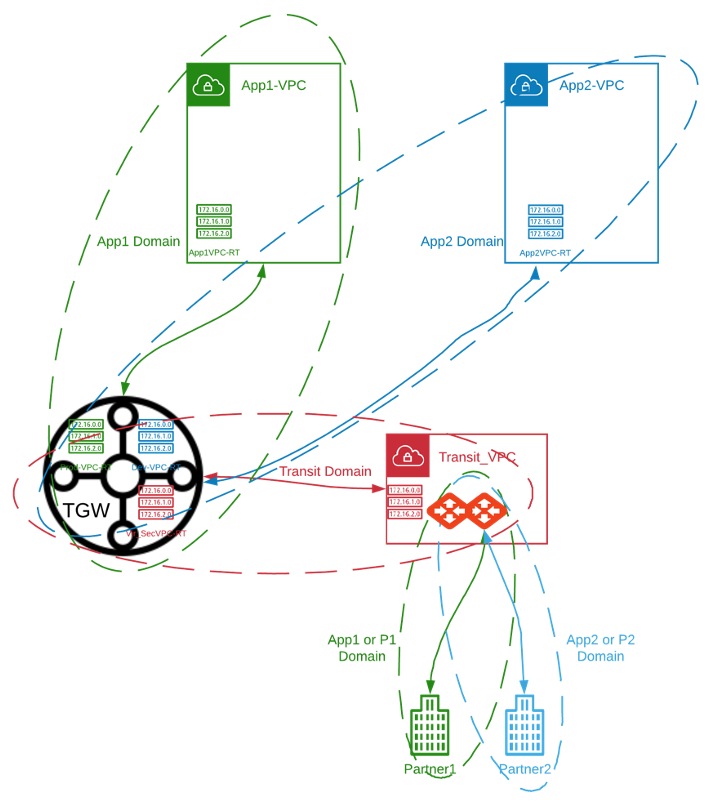
Customer Use-Case and Topology
- Partner1 builds IPSec tunnels with Aviatrix Transit GW (AVX-TR-GW)
- Partner2 builds IPSec tunnels with Aviatrix Transit GW (AVX-TR-GW)
- Partner1 should only be allowed to access App1-VPC attached to AWS-TGW
- Partner2 should only be allowed to access App2-VPC attached to AWS-TGW
This can be allowed via AWS-TGW Connection Policy control in Aviatrix Controller.
One can use the same VPC domain or create a new domain for each partner.
How to Enable Edge Segmentation?
To enable Edge Segmentation, go to Aviatrix Transit Network -> Setup -> Step 3, Connect to VGW/External Device/CloudN, to select the option “Enable Edge Segmentation”.
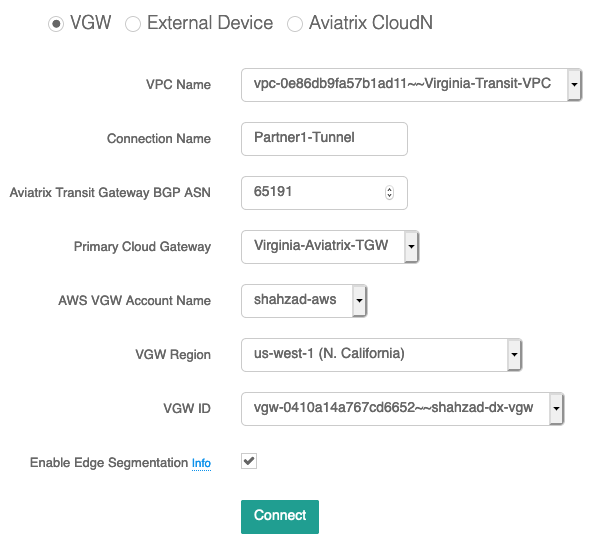
Note: The option "Enable Edge Segmentation" is moved to the Gateway List section starting from Aviatrix version 6.2
Where to view Edge Segmentation Security Domain?
When you enable the Edge Segmentation, the screen will not show any domain there. In the background, the Aviatrix Controller creates a corresponding Security Domain, but it shows in the AWS-TGW Orchestration area.
Go to AWS-TGW Orchestrator --> Plan --> Security Domain --> Select TGW. Now you will see the edge domain as shown in the following diagram
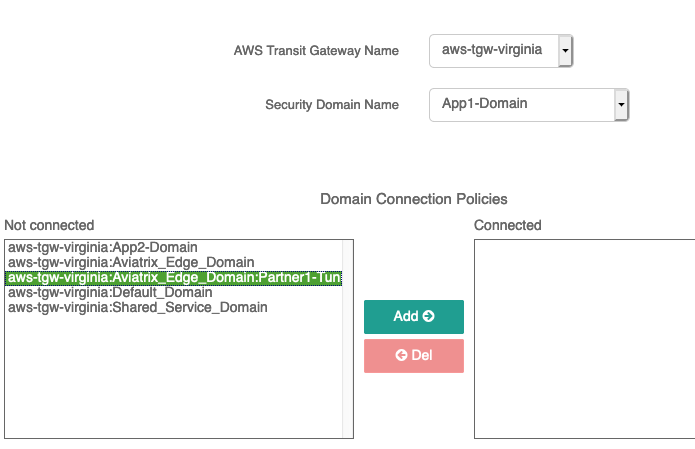
Now first connect App1-Domain to Aviatrix_Edge_Domain.
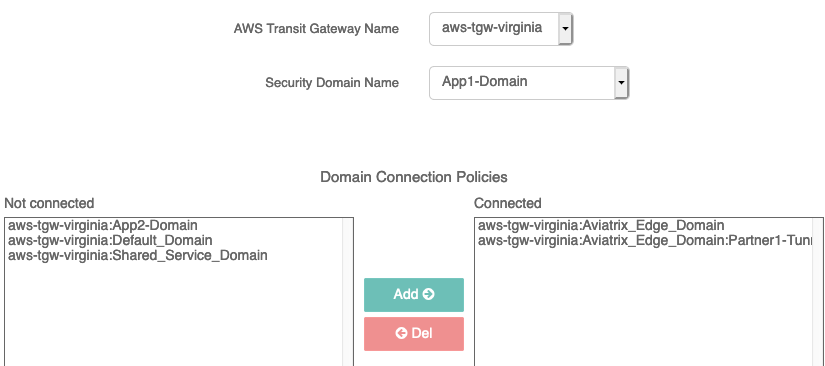
And then connect App1-Domain to Aviatrix_Edge_Domain: Partner1-Tunnel
To build the connection policy.
More info: https://docs.aviatrix.com/HowTos/tgw_faq.html#what-is-edge-segmentation

