Aviatrix Hybrid Cloud Network Landing Zone provides a best practice based, consistent, and fully automated network solution for landing hybrid cloud connections from Data Centers, Colocation facilities, and more to the public cloud. Aviatrix Hybrid Cloud Network Landing Zone complements native CSP transit solutions such as AWS Transit Gateway, Azure Virtual WAN, Google NCC etc. to provide critical traffic engineering, Netflow, packet captures, visibility, and troubleshooting capabilities required by network engineers and operators.
In addition, the Aviatrix Hybrid Cloud Network data plane proves to be much more cost effective especially for landing connections used to move large quantity of data. See the Cost Optimized Hybrid Cloud Section for details.
Key Benefits
- Deep visibility into traffic flows such as Netflow
- Advance troubleshooting capabilities in cloud such as packet capture
- High scale routing to overcome native route limits
- Multicloud architecture that works in every cloud
- Best Practices based architecture validated by CSP Networking SMEs
- Capabilities including line-rate Encryption, SDWAN & Firewall integration
High Level Architecture
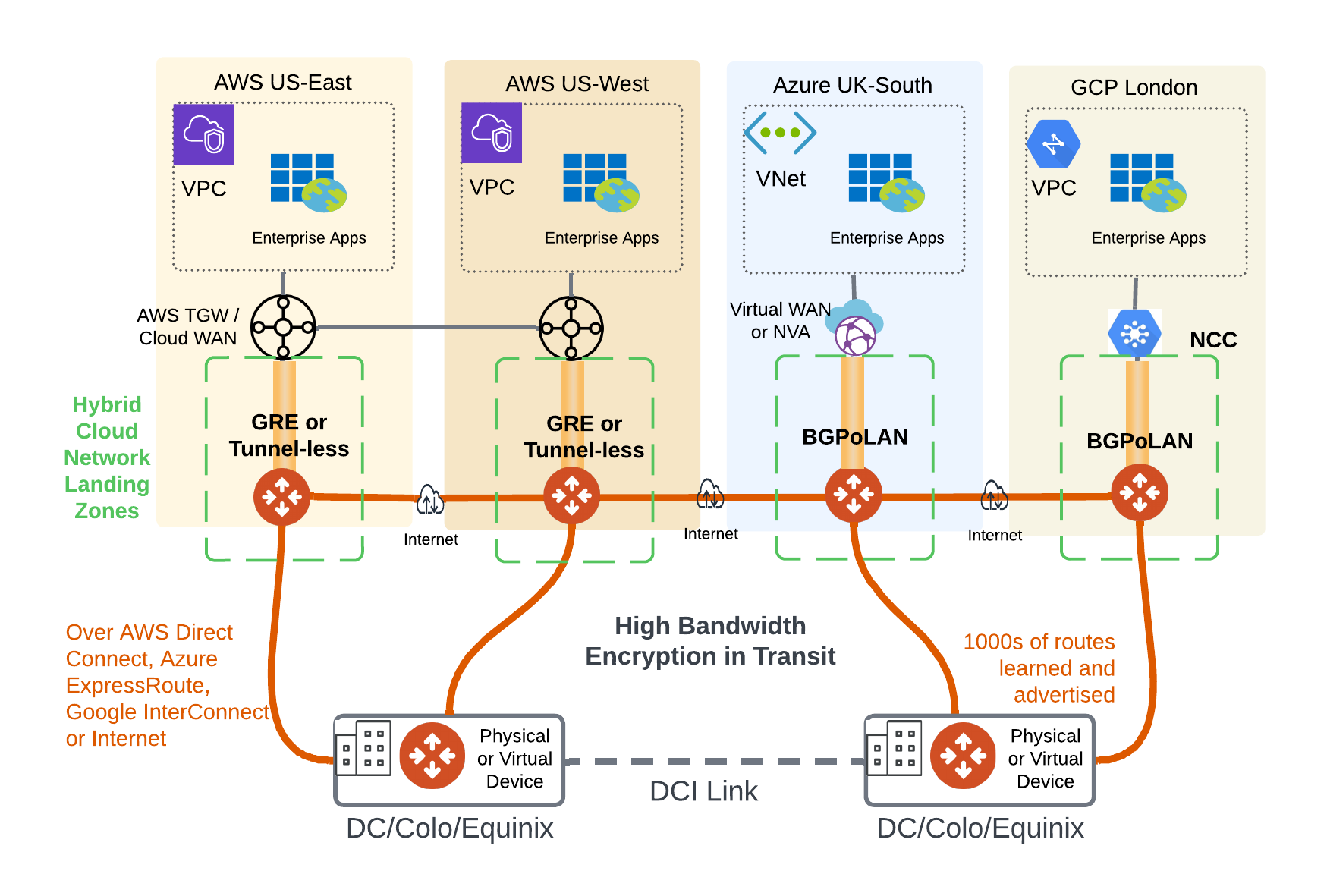
Figure 1: High Level Architecture
Why is this needed?
Enterprises build Landing Zones in public cloud with a focus on applications and in-cloud infrastructure which often does not address the operational requirements of the teams managing hybrid cloud network connectivity. The Hybrid Cloud Network Landing Zone addresses these challenges while also providing a clean delineation between cloud and network teams.
Network teams have existing visibility, troubleshooting capabilities, route scaling, and traffic engineering options when connecting on-premises environments (DC, Colo, Branch etc.) to the cloud. However, most of these facilities are either completely missing or very basic on the cloud side. In the absence of these required tools and visibility, even the basic connectivity issues become complicated to solve impacting uptime, increasing MTTR and impacting SLAs.
The Hybrid Cloud Network Landing Zone architecture by Aviatrix provides network teams a peering architecture in the cloud that gives them advance capabilities in the cloud, overcome CSP limitations, enhance CSP capabilities and peer seamlessly with other cloud entities such as AWS Transit Gateway, Azure Virtual WAN, Google NCC, OCI DRG etc. With this architecture, network teams can own both ends of the hybrid cloud connection and provide an excellent experience to application teams and business.
What are the business benefits?
What are the technical advantages?
How does it work?
As shown in Figure 1, Aviatrix Transit (the round orange icons), are multi services routing and security devices that form the data plane pushing the packets. It seamlessly work with any other network device such as CSP Transits, router, sdwan or a security device such as a firewall to build a robust, scalable and secure overlay based backbone over the hybrid cloud on-ramp, csp backbone or internet.
Here are the simple steps that can be performed via Terraform or UI
- Deploy Aviatrix Transit in a standalone cloud network such as a VPC/VNet or VCN.
- Aviatrix Transit automatically builds tunnel-less BGP, or multiple high performance GRE / IPSec connections to existing CSP Transit such as AWS Transit Gateway, Virtual WAN, Google NCC, OCI DRG etc.
- Aviatrix Transit can connect to any external device such as a router or a firewall over VPN or Direct Connect
- Optionally, Aviatrix Edge (virtual or physical) can be deployed at an on-premises location such as an Equinix Colo or a DC to provide high performance line-rate encryption and high routing scale·
- For ex, this capability overcomes native AWS Transit Gateway limit of 200 routes from cloud to on-prem and 100 routes per Direct Connect from on-prem to cloud.
I am moving a lot of data between on-prem and cloud, how does this solution optimizes for cost?
Lets take an example of data being migrated from on-prem to an AWS region. A typical setup would include packets to move from Direct Connect (DX) --> Direct Connect Gateway (DXGW) --> AWS Transit Gateway (TGW) --> Workload VPC. Although DX and DXGW won’t charge for any ingress data, TGW does charges $0.02 per GB. This means just a 2 Gbps sustained utilization per month on a typical 10 Gbps DX circuit, you will end up moving 657 TB of data resulting in $13,140 due for just data processing at transit (657000 * $0.02),
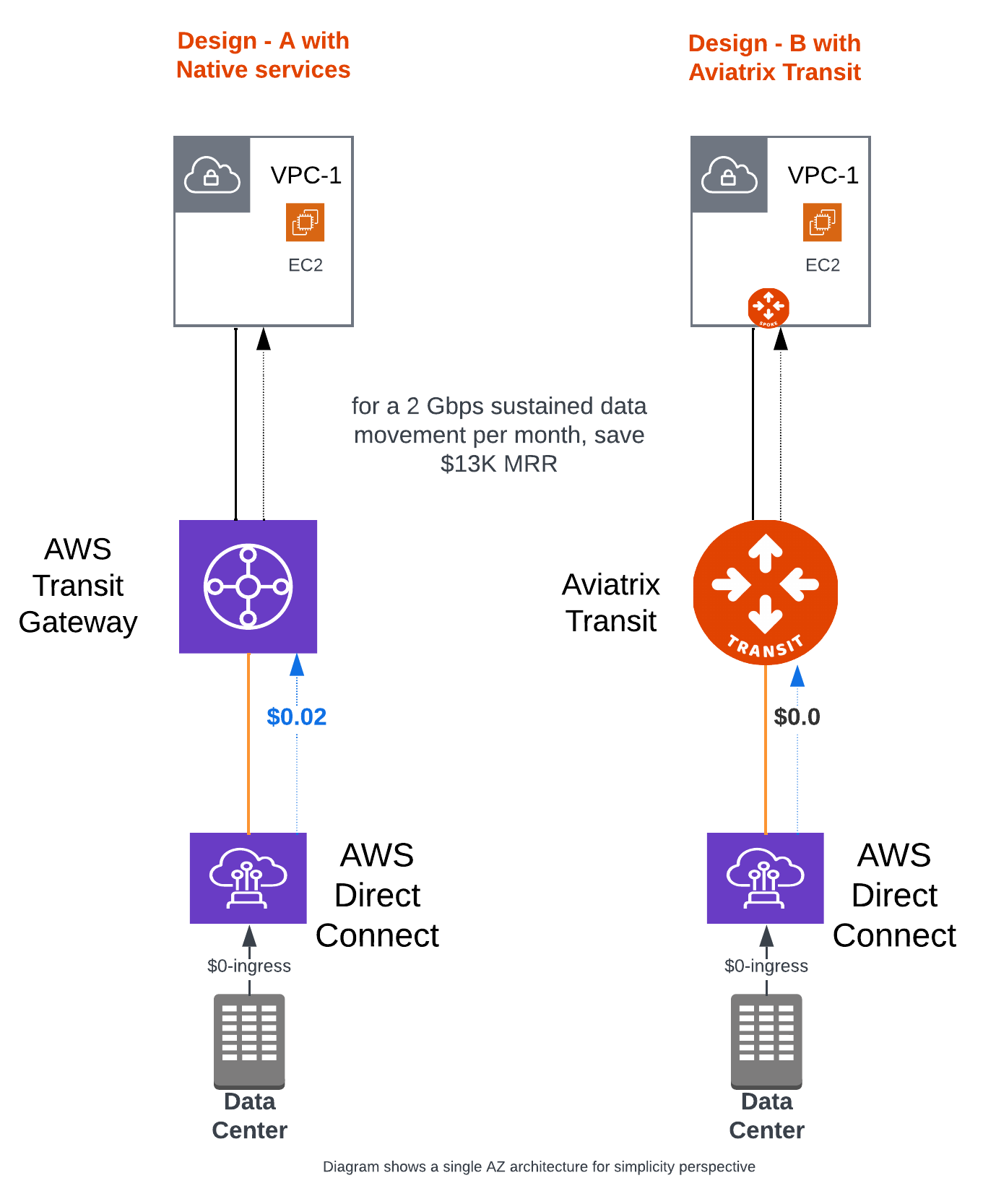
Figure 2: Data processing charges across transit options
Similar savings apply to Azure Virtual WAN and Google NCC. In addition, traffic pattern that use NextGen Firewalls in the path provide significant additional savings. Please contact the author specific requirements.
What is Aviatrix High Performance Line-Rate Encryption?
Limited encrypted thruput with cloud native end-to-end encryption
Upto 100 Gbps encrypted thruput with Aviatrix end-to-end encryption
Figure 3: Technical overview of high performance encrypted connectivity
Could you provide an example of how Aviatrix overcomes route limitations?
Figure 4: How Aviatrix overcomes native route limits
In a brownfield deployment, what is the expected downtime to switch to this architecture?
How does it integrate with SDWAN in the cloud and in Data Center?
I have Colocation with Equinix/Megaport, does it work there?
Can I see Technical Deep Dives and demos?
How is the solution priced?
How can I get started today?
- Request a demo > https://aviatrix.com/schedule-demo/
- Get ACE Certified > https://aviatrix.com/ace/
- Learn more > www.aviatrix.com

