Network segmentation is a highly effective strategy to limit the impact of network intrusion. This article delves into ways to simplify network segmentation and how Aviatrix Network Security Domains, along with AWS Transit Gateway (TGW), provide a solution for secure network traffic in multi-VPC environments.
Cloud Network Segmentation: why and how?
First, let’s look at why network segmentation is vital to network security. In the traditional data center networks, segmentation was primarily done via a DMZ or perimeter which had firewall devices. The issue here was that once a bad actor got into the network, they gained wide reach throughout the “private” network.
Segmentation approaches called for partitions of numerous smaller networks, reducing the reachability for intruders, minimizing the damage they could do. This type of segmentation involves developing and enforcing a set of rules to manage the traffic between segments. The best practice was to find a manageable level to which you could segment your network. Go too fine-grained, it’ll be near impossible to manage; go too coarse, and your blast radius may be too large for one or more segments. Beyond the practical considerations, the best practices include looking at grouping networks by their sensitivity level; for example, production networks vs. test networks are of different levels, usually due to live customer data being in the production systems.
Up until the concept of domains was introduced by AWS at reinvent 2018, network segmentation in AWS was mainly achieved by using Accounts, VPCs, Security Groups, and Access Control Lists (ACLs). Whereas most cloud engineers have found ACLs to be impractical to manage, Security Groups are used widely to provide instance-level security within a VPC. At a VPC level, peering and transit hubs have implemented connectivity but with inconsistent approaches to segmentation. As the number of VPC networks and cloud security concerns has grown with the mass adoption of public clouds, the routing between VPCs has become increasingly complex and a bigger and bigger problem that needs a solution. There simply has not existed an easy way to group VPCs together.
AWS Transit Gateway (TGW) route domains is a concept which simplifies the segmentation of groups of VPCs and VPNs. It is a centralized approach to achieving network segmentation, reducing unauthorized lateral movement.
Benefits of Aviatrix Security Domains
Aviatrix Security Domains was introduced in conjunction with AWS Transit Gateway (TGW) to solve the problem of VPC level segmentation. Security Domains are an instantiation of the AWS Transit Gateway (TGW) route domain concept. It turns a concept into an object, ideal for network segmentation. A Security Domain is an AVX controller-enforced network of member VPCs attached to the same route table. Member VPCs have connectivity to each other. VPCs outside of the domain cannot connect. This dramatically simplifies the approach to securing large VPC environments. As a centralized system, the AVX Controller spans multi-region,multi-cloud, and on-prem environments.
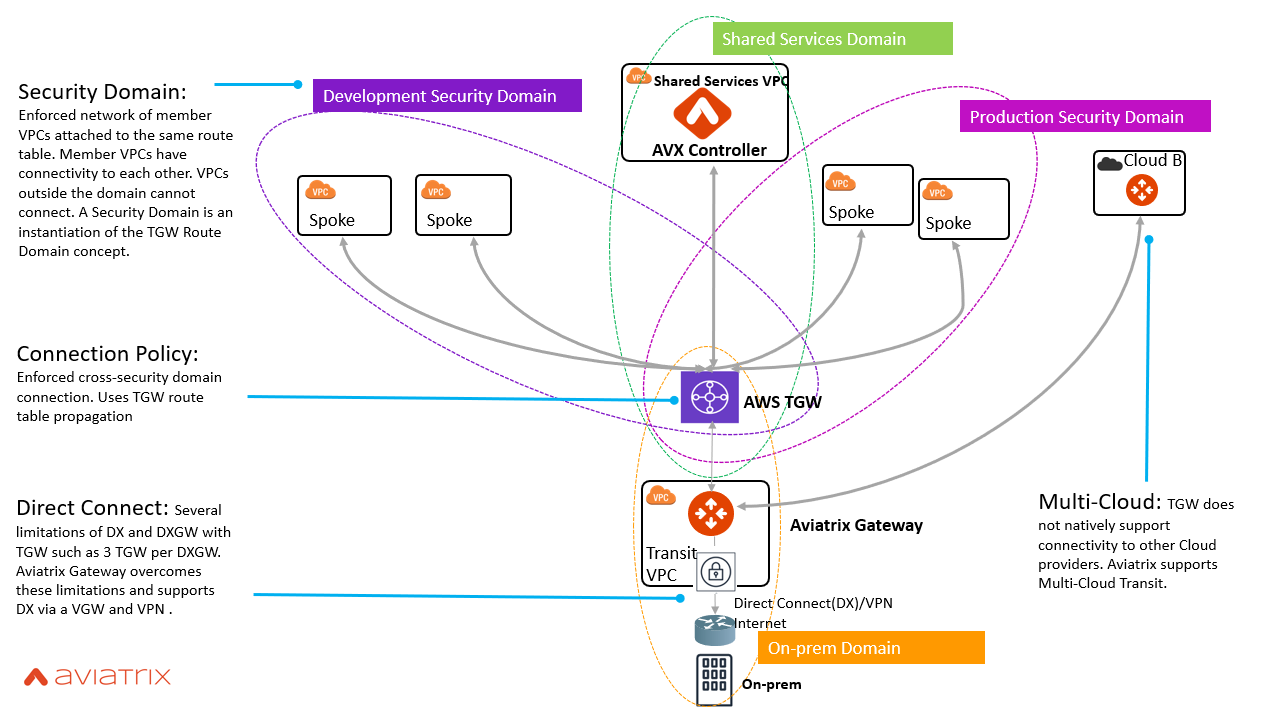
Along with Security Domains, we’ve introduced Connection Policies.
Connection Policies are AVX controller-enforced cross-Security Domain connectivity. Again leveraging the innovation of AWS, this uses AWS Transit Gateway (TGW) route table propagation. Now Cloud and Security teams can have a common framework, with visibility and control of what is connected and why. Connection Policies are human-readable and, again, centrally deployed. Audit and compliance reporting at the VPC level are now more readily available. Lastly, defining VPC level security with a few centralized rules is far simpler to conceptualize and far easier to implement.
Leading us to the Zero Trust Cloud Architecture
Combining Security Domains, Connection Policies, and AWS Transit Gateway (TGW) produces a simple yet robust architecture for security and compliance of VPC networks. A Zero Trust Cloud Architecture helps to:
- Ensure the VPC network meets security best practices=
- Limit lateral movement during a breach
- Minimize blast radius due to misconfigurations
- Avoid delays due to tedious, manual configuration
Summing it up
Aviatrix believes that Security Domains and Connection Policies for network segmentation are essential keys to securing cloud-based environments.
Click here to download and print this 2-page PDF Transit Gateway and Zero Trust Architecture quick reference guide.
