As a former Head of Network Engineering at a global financial, I have witnessed the transformative power of cloud networks. The ability to scale resources dynamically, enhance collaboration, and increase operational efficiency has made cloud networks a cornerstone of modern business infrastructure.
We’re now moving into another exciting era of cloud networking whereby the security and cost control of cloud networks is paramount - given the sensitive data and critical applications moving to cloud, and the need to lower cloud cost and spend more strategically. Balancing these factors is key to maximize the benefits of the cloud while minimizing risks and maintaining financial sustainability.
In this blog, I will delve into the mindset of a CIO/CTO and explore strategies to ensure a secure cloud network and cost control measures. Whilst some of the strategies mentioned below may seem obvious, the innovative and disruptive solutions from companies like Aviatrix may not feel so to everyone and therefore I am going to highlight how these are emerging as most impactful and best in class.

- Design a Secure Network Architecture: The foundation of a secure cloud network lies in its architecture. It is crucial to adopt a defence-in-depth approach, implementing multiple layers of security controls.
Segmenting the network into distinct security zones with appropriate access controls helps mitigate the impact / blast radius of a potential breach.
Network encryption is vital for protecting data in transit within cloud networks. Implementing secure communication protocols, such as Transport Layer Security (TLS) and Secure Shell (SSH), ensures that data exchanged between network end points remains confidential and tamper-proof. Encryption should be implemented not only for external communication but also for internal network traffic to mitigate risks posed by insider threats.
For more information on how to architect a secure cloud network with Aviatrix, use this link: https://aviatrix.com/wp-content/uploads/2021/01/Ebook-The-Network-Architects-Guide-Multi-Cloud-Networking-210104.pdf
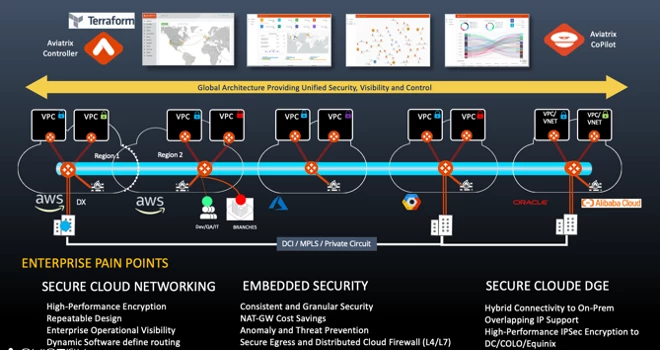
- Implement firewalls and intrusion detection and prevention systems (IDPS). The most impactful practice is Aviatrix’s Distributed Cloud Firewall (DCF). Aviatrix has redefined cloud network security by distributing inspection and policy enforcement directly along the path of application traffic.
The Distributed Cloud Firewall is far more impactful exactly for its ability to detect and prevent malicious traffic from the multiple cloud internet entry / exit points and for dropping this traffic as close to the source as possible. For a more in-depth read, click this link: https://aviatrix.com/distributed-cloud-firewall/
Some highlights of Aviatrix’s Distributed Cloud Firewall:
- Aviatrix’s Distributed Cloud Firewall: This comprehensive solution secures both internal (East-West) and external (North-South) traffic, covering various aspects of network security. It equips organizations with the necessary tools to adopt a zero-trust network architecture across their cloud footprint.
- Aviatrix Distributed Cloud Firewall for Egress: This solution enforces security policies, prevents unauthorized access, and defends against threats aimed at outgoing traffic. It seamlessly integrates with existing architectures, offering an easy way to get started, save money, and enhance security.
- Aviatrix NAT Gateway: A simple, cost-effective feature (of Distributed Cloud Firewall for Egress) that centralizes outbound NAT management and provides visibility into all Egress traffic flows.
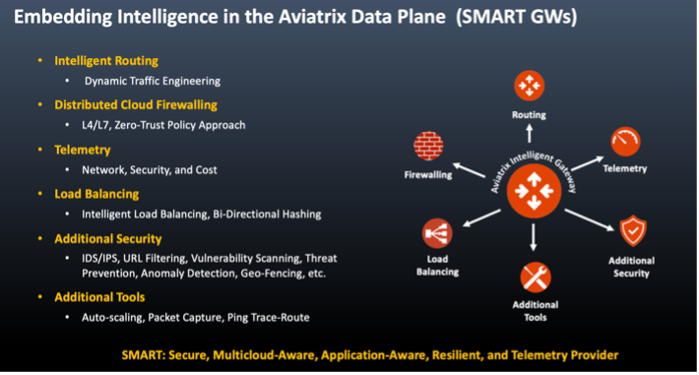
Important to note is that it is no longer considered best practice to steer traffic to a centralised cloud firewall – this was a lift and shift approach inspired from the on-prem datacentre world which quickly became ineffective in the public cloud.
Why is that? Simply put, in cloud, internet exit and entry points are everywhere, therefore the confidence in a centralised firewall to detect and drop all the malicious traffic that is coming to you from anywhere and everywhere cannot be assured.
- Continuous Monitoring and Intrusion Detection: Cloud network security requires continuous monitoring to detect and respond to potential threats promptly. Employing network monitoring tools together with security information and event management (SIEM) systems enables real-time visibility into network activities. Intrusion detection systems (IDS) and intrusion prevention systems (IPS) should be deployed to identify and mitigate malicious activities, such as unauthorized access attempts or network anomalies.
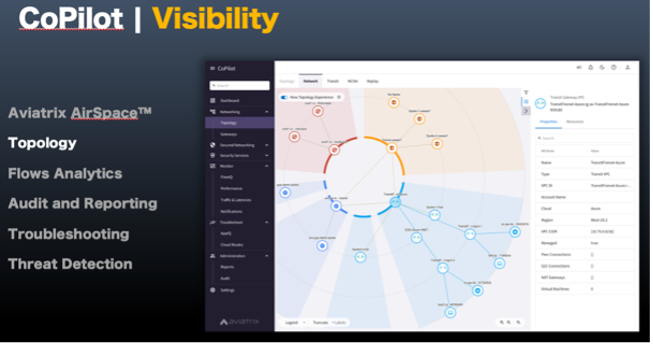
Aviatrix CoPilot is a single console to continuously monitoring and manage Aviatrix Secure Cloud Network. Some key attributes include - Real Time Monitoring and Alerts
- Dynamic Topology Map
- CostIQ and FlowIQ, Notifications
- ThreatIQ
- Distributed Cloud Firewall
- Segmentation
- GeoBlocking
- Egress Control and Auditing
For a detailed CoPilot overview, please click on the following link:
https://docs.aviatrix.com/copilot/latest/aviatrix-overview/copilot-features.html
- Implementing Robust Identity and Access Management (IAM): Identity and access management plays a pivotal role in securing cloud networks. A robust IAM system should be in place to ensure that only authorized individuals can access network resources. Implementing strong authentication mechanisms, such as continuous multi-factor authentication and strong password policies, reduces the risk of unauthorized access. Regularly reviewing and revoking access privileges for former employees or contractors helps maintain a secure network environment.
- Regular Network Vulnerability Assessments and Penetration Testing: Conducting regular vulnerability assessments and penetration testing is crucial for identifying and remediating network vulnerabilities. Collaborating with cybersecurity experts to perform comprehensive assessments helps uncover potential weaknesses in the network infrastructure. The findings from these assessments should be addressed promptly to strengthen network security and prevent potential breaches.
- Disaster Recovery and Business Continuity Planning: Secure cloud network operations should include robust disaster recovery (DR) and business continuity (BC) planning. Developing and regularly testing DR and BC plans ensure that network services can be restored swiftly in case of disruptions or disasters. This includes data backup and replication strategies, failover mechanisms, and comprehensive incident response plans to minimize the impact of security incidents.
In summary, and needless-to-say, prioritizing cloud network security not only safeguards sensitive data but also ensures uninterrupted business operations, instils customer confidence, and positions organizations for success.
The challenge for organisations is to improve network security whilst lowering cost and for some of the strategies mentioned, Aviatrix has redefined cloud network security by distributing inspection and policy enforcement directly along the path of application traffic.
Aviatrix’s Distributed Cloud Firewall not only delivers improved cloud security but is also a significantly lower cost solution when compared to cloud service provider (CSP) alternatives and centralised 3rd party firewalls.
But securing cloud networks can be complex and an ongoing endeavour that requires a comprehensive approach. By focusing on a robust secure network architecture, using distributed cloud firewalling, implementing robust IAM practices, employing network layer encryption, continuously monitoring for intrusions, conducting regular vulnerability assessments, and establishing robust DR and BC plans, CTOs can not only enhance the security posture of cloud networks but can reduce the challenge and risk to achieve.

