Aviatrix offers a comprehensive cloud network platform that seamlessly integrates security, visibility, and automation features. The Aviatrix solution is an SDN (Software-Defined Networking) solution and, like most SDN solutions, comprises:
- Control Plane via the Aviatrix Controller
- Management Plane via Aviatrix CoPilot
- Distributed Data Plane via Aviatrix Gateways
The Aviatrix architecture involves these different planes interacting and communicating with one another through various protocols. Understanding these interactions and protocols is crucial for configuring and optimizing the Aviatrix environment effectively.
In this blog, we will delve into the communication protocols and interactions among the Aviatrix planes.
The diagram below illustrates the interactions between different planes.
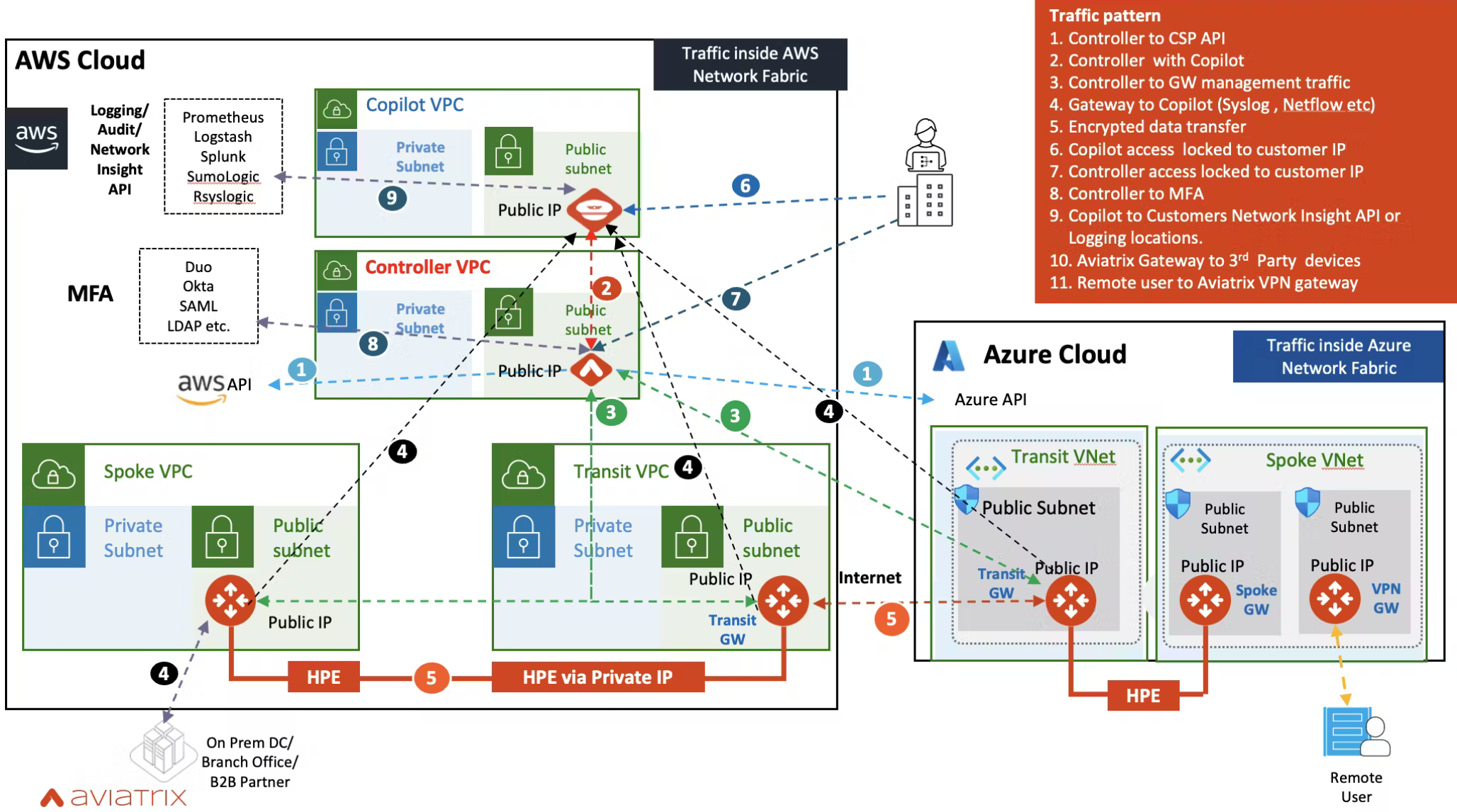
Below is the common list of protocols use in above communication.
- Controller to CSP API (HTTPS over port 443)
- Controller to and from Copilot.
a. HTTPS over port 443 for API, UDP 5000 for Controller syslog’s to Co-Pilot. - Controller to and from Gateway (HTTPS over port 443)
- Gateway to Copilot (UDP 5000 for syslog, UDP 31283 for Flow data)
- Gateway to Gateway-Encrypted Data Transfer (UDP 500 for IKE, UDP 4500 for ESP)
- User to Copilot (HTTPS over port 443) for UI based management and orcehstration
- User to Controller (HTTPS over port 443) for management and orchestration
- Controller to MFA (HTTPS over port 443, in case of LDAP it is UDP port 389)
- Copilot to Customer logging servers or Network Insight API traffic to Prometheus etc.
a. Syslog by default on UDP port 5000 or customer configurable, Network Insight API traffic HTTPS over port 443 -
S2C traffic or Traffic to Native CSP Routing devices like AWS TGW, Azure RS etc.
a. Examples are: IPsec , GRE , or unencrypted BGPoLAN -
Remote User to Aviatrix VPN gateway ( OpenVPN UDP port 1194)
Misc Traffic and Flows
In addition of above flows there are some other which didn’t illustrate in above diagram.
- Aviatrix Controller, Copilot and Aviatrix Gateways need to access DNS servers on UDP port 53.
- Aviatrix Controller, Copilot and Aviatrix Gateways need to access NTP servers on UDP port 123.
- Aviatrix Controller need to access some sites for software download using HTTPS over port 443 etc. like release.aviatrix.com, license.aviatrix.com, diag.aviatrix.com etc.
- Aviatrix CoPilot need to access some sites for using HTTPS over port 443 etc. like copilot update server, geoip.elastic.co, artifacts.elastic.co and some other Aviatrix update and security sites.
Detailed information about external site access is provided at the following link:
Aviatrix-Products-Required-Access-for-External-Sites
For the migration of Aviatrix Old Copilot to New Copilot, the New Copilot needs to access the old Copilot on TCP port 9200.
https://docs.aviatrix.com/documentation/latest/copilot-platform-administration/copilot-migrate.html#open-required-ports-on-each-copilot-instance
Below is the detailed explanation of traffic patterns illustrated in above diagram.
1. Controller to CSP API
The Aviatrix Controller communicates with Cloud Service Provider (CSP) APIs to enable seamless integration and management across various cloud environments. The Aviatrix Controller primarily communicates with other components via HTTPS, leveraging RESTful APIs for secure and efficient communication.
- The Aviatrix Controller securely authenticates with the CSP using API keys, access tokens, or other CSP-specific authentication mechanisms.
- Secure communication channels (such as HTTPS with TLS) are established to ensure that data exchanged between the controller and the CSP APIs remains confidential and tamper-proof.
- The controller interacts with the CSP APIs to manage cloud resources such as virtual machines, networks, subnets, route tables, and security groups.
- These interactions allow the Aviatrix Controller to orchestrate the deployment and scaling of network resources and services within the cloud environment.
- The controller queries CSP APIs to gather real-time information and metrics about the network's performance, resource utilization, and health.
- This data is used to provide visibility into the cloud network's operational status and to detect and respond to issues proactively.
By effectively leveraging CSP APIs, the Aviatrix Controller simplifies the complexity of managing cloud networking environments, providing a centralized platform for automation, visibility, and control.
2. Controller with Copilot (Bi Directional)
The communication between the Aviatrix Controller and CoPilot is crucial for the overall functionality of the Aviatrix platform, ensuring seamless integration for management, monitoring, and troubleshooting. Below is some explanation of how these two components interact:
- The user initiates the orchestration process from the CoPilot interface. This may include creating new VPCs, deploying gateways, or setting up DCF rules etc.
- CoPilot translates the user inputs into a series of API calls directed to the Aviatrix Controller.
- These API calls are securely sent over HTTPS to maintain data integrity and confidentiality.
- The progress and status of these operations are monitored by the Controller, and ongoing status updates are communicated back to CoPilot.
- CoPilot displays these updates to the user, providing real-time feedback on the orchestration process.
- Once the orchestration tasks are completed, the Aviatrix Controller verifies the deployment to ensure everything is correctly configured and operational.
- The completed configurations, including the new VPCs, gateways, and firewall rules, are then synchronized with CoPilot.
- CoPilot updates its dashboards and user interfaces to reflect the newly orchestrated resources.
- The user can then visualize and manage these resources within CoPilot’s UI, ensuring that they are integrated into the broader network environment.
- CoPilot periodically requests data from the Aviatrix Controller to gather updated metrics and performance data. This includes information on traffic patterns, device health, and any anomalies detected in the network.
Alert and Event Management:
CoPilot can send specific queries to the Aviatrix Controller for detailed information when an alert or event is triggered. This helps in diagnosing issues and providing actionable insights.
By effectively leveraging CSP APIs, the Aviatrix Controller simplifies the complexity of managing cloud networking environments, providing a centralized platform for automation, visibility, and control.
3. Controller to Aviatrix Gateways
The Aviatrix Controller communicates with Aviatrix gateways for several reaseons, including deployment, configuration, monitoring, and management of the network infrastructure across various cloud environments. The communication involves the exchange of control and management data necessary for the functioning of the network setup facilitated by Aviatrix.
The primary protocol used for communication between the Aviatrix Controller and Aviatrix gateways is HTTPS (TCP port 443), which ensures secure communication through encryption.
4. Aviatrix Gateways to Copilot
Aviatrix Gateways send logs and flow data to Aviatrix CoPilot to enhance monitoring and management capabilities within single, multi or hybrid cloud networks. The types of data sent include syslog messages and NetFlow data, which provide detailed insights into network activity and performance.
Aviatrix Gateways communicate crucial logs and flow data to CoPilot using Syslog (UDP port 5000) and NetFlow (UDP port 31283).
5. Gateways to Gateways - Encrypted Data Transfer
Aviatrix do secure data transfer between gateways using IPSec.
IPsec is used to create secure Site-to-Site VPN tunnels between Aviatrix Gateways, ensuring encrypted communication across different network segments.
UDP port 500: Used for IKE (Internet Key Exchange) Phase 1, where the initial negotiation and establishment of the secure channel occur.
UDP port 4500: Used for ESP (Encapsulating Security Payload) traffic.
6. User to Copilot for Management and Orchestration
Used for secure access to the CoPilot user interface. All communications between users' browsers and the CoPilot server are encrypted using HTTPS.
Aviatrix CoPilot includes Network Insights APIs designed to facilitate detailed network monitoring, analytics, and troubleshooting. These APIs allow you to programmatically access various metrics and data from CoPilot.
All API requests to the CoPilot for Network Insights are made over HTTPS to ensure that the communication is encrypted and secure.
7. User to Controller for Management and Orchestration
Users access the Aviatrix Controller's management console via a web browser using HTTPS. This ensures that all user interactions with the controller are encrypted and secure. Resources such as Terraform, SDKs, and other automation tools may interact with the Aviatrix Controller for programmatic management, configuration, and monitoring.
Terraform requests to the Aviatrix Controller are made over HTTPS. This allows Terraform configurations to securely manage and automate network resources via the Aviatrix Controller. Any external tools or SDKs integrating with the Aviatrix Controller use the REST API, secured over HTTPS.
8. Controller to MFA, SAML Providers, LDAP
SAML (Security Assertion Markup Language) is commonly used for Single Sign-On (SSO) to authenticate users. The Aviatrix Controller supports integration with SAML providers for authentication. Initial traffic for SAML authentication runs on TCP port 443. The controller exposes this port to enable secure SAML authentication interactions.
The Aviatrix Controller can authenticate users against an LDAP server (e.g., Active Directory).
Aviatrix uses port 389 for connections to an LDAP server.
9. Copilot with Customer Logging Servers and Network Insight APIs
Aviatrix CoPilot can forward logs to customer-specified logging servers for further analysis and storageAviatrix CoPilot can forward logs to customer-specified logging servers for further analysis and storage e.g Splunk, Elastic Stack(ELK, Logstash etc and it cas use customer defined TCP or UDP port numbers.
Aviatrix CoPilot provides various APIs to access network insights for monitoring and operational purposes.
API is using standard HTTP (TCP on Port 443).
10. S2C traffic or Traffic to Native CSP Routing devices like AWS TGW, Azure RS etc. ( IPsec , GRE , or Unencrypted BGPoLAN)
Aviatrix Gateway can connect to other devices outside your network, such as:
- Devices on the edge of a customer's network.
- Devices native to cloud service providers like AWS TGW, Azure RS, AWS Cloud WAN, and more.
- Devices from third-party vendors in public clouds, such as SDWAN devices.
Connectivity to those device can be using.
- IPSec with UDP port 500 is used for IKE (Internet Key Exchange) Phase 1, where the initial negotiation and establishment of the secure channel occur. UDP port 4500 is used for ESP (Encapsulating Security Payload) traffic.
- GRE uses IP Protocol 47.
- BGP over LAN (BGPoLAN) uses BGP as the routing protocol over TCP port 179.
11. Remote User to Aviatrix VPN gateway ( OpenVPN UDP port 1194)
Aviatrix provides a robust remote user VPN solution based on the OpenVPN® protocol. This solution is tailored for seamless and secure access to cloud networks.
Network Communication Details for Aviatrix Edge:
Aviatrix Edge Gateways are deployed in the on-prem colo or data center location. From the traffic flow and communication point of view they act and behave very similar to Aviatrix Spoke gateway. Therefore their ports and protocol requirements are very similar too.
Following diagram shows and Aviatrix Edge deployed in the on-prem location. It is connected with AVIATRIX transit using AWS Direct Connect. It has established communication with Aviatrix Control and Management plane.
Following diagram shows Aviatrix Edge communication ports and protocols without Direct Connect Design and behind a 3rd party WAN router.
WAN Interface (eth0)
The network interface facilitates connectivity to other Aviatrix Gateways, necessitating a default gateway and Layer 3 reachability to interact with other Aviatrix Gateway Private or Public IPs. This interface is specifically designated for secure encrypted data transfers, notably detailed in the context of IPsec encryption, and operates through UDP ports 500 and 4500.
Management Interface (eth2)
Mandates a default gateway, DNS access, and Internet connectivity for seamless communication:
The Aviatrix Controller necessitates connectivity via TCP port 443 for secure data transmission.
Interaction with the Aviatrix Copilot for syslog entails UDP port 5000, while UDP port 31283 is designated for flow data transmission.
Activities such as Aviatrix software downloads are facilitated through HTTPS on TCP port 443 to ensure a secure and reliable transfer of data.
Summary
Aviatrix uses standard ports and protocols for communication, overlay construction, and traffic flows. This approach is aligned with the networking set forth by IRTF, IEEE, IETF and RFC Editor. Aviatrix do not rely on propriety networking protocol or headers. This approach offers customers flexibility to integrate and extend cloud networks, unlike CSPs that rely on proprietary techniques for traffic routing, security policies and flow visibility.
This post emphasizes the use of standard port choices to prevent vendor or CSP lock-ins, adding significant value to the solution. This approach ensures Aviatrix remains standard and consistent across cloud and hybrid cloud environments, facilitating easy migration and movement of data and applications in and out of cloud networks.
Aviatrix is dedicated to offering customers options by ensuring their product functions along with other vendors whether are in the public cloud, or part of on-premises solutions. This approach gives Aviatrix advantages over cloud-native design. It allows Aviatrix to deliver simplicity, security, and cost-effectiveness extremely difficult to achieve with CSP networking solutions.

