Active / Active HA
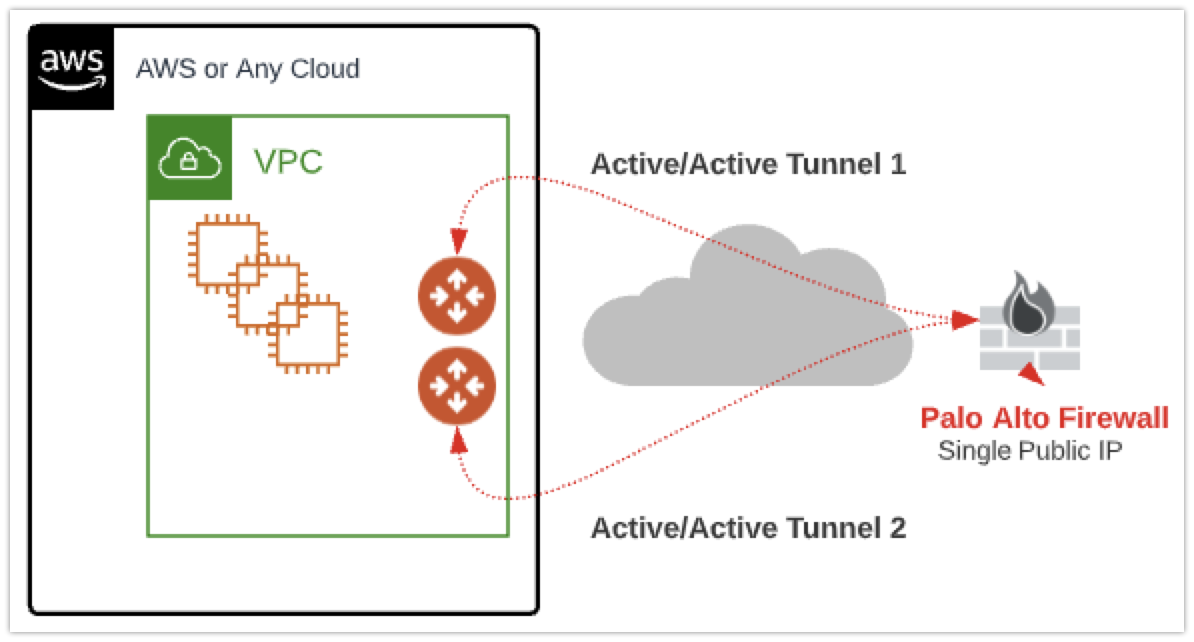
Aviatrix can allow for Site2Cloud gateways to support Active / Active HA mode where both tunnels are up and packets are routed to both gateways via their respective VPC route tables.
In this use case, we will build two Site2Cloud policy-based tunnels to a Palo Alto Networks firewall with a single public IP. With Active / Active HA enabled, both tunnels will show as up. We will then use Path Monitoring to dictate routing in the event of a down tunnel on the Palo Alto Networks firewall.
Topology
Aviatrix Cloud CIDR: 10.68.0.0/16
Aviatrix Primary Gateway Local IP: 10.68.105.117 (Enable ping in AWS Security Group / SG)
Aviatrix Primary Gateway Public IP: 54.x
Aviatrix HA Gateway Public IP: 24.x
Palo Alto CIDR: 10.239.0.0/16
Palo Alto Primary Tunnel Virtual IP: 10.239.10.10 (Set in Primary Tunnel Interface)
Palo Alto Public IP: 67.x
Steps to Configure
On Controller
To enable Gateway for High Availability Peering (Active / Active HA) on the desired gateway and create a policy-based Site2Cloud tunnel, follow these steps:
1. Log in to your Aviatrix Controller.
2. In the left navigation pane select SITE2CLOUD > Setup > + ADD NEW.
3. Select ENABLE HA.
4. Use the drop-down menu to select Primary and Backup Gateways.
5. In this case, the Palo Alto Networks gateway has a single public IP address. The Remote Gateway IP Address and the Remote Gateway IP Address (Backup) will have the same IP. Enter 67.x.x.x.
6. To enable Active Active HA, go to: Controller > SITE2CLOUD > (tunnel name) > Edit > Enable Active Active HA.
7. Follow the instructions on docs.aviatrix.com to configure the Primary Tunnel to the Palo Alto Networks firewall: https://docs.aviatrix.com/HowTos/S2C_GW_PAN.html
In AWS
Allow ping on the Primary Aviatrix Gateway's AWS SG from the Palo Alto Network gateway's local CIDR range (10.239.0.0/16).
| Note |
| You may also ping an EC2 behind the Aviatrix Gateway. |
On Palo Alto Networks Firewall
Once the primary tunnel is created per the documentation above, you need to create a second tunnel for the HA gateway and enable Path Monitoring on the Primary tunnel.
HA Tunnel Settings
1. Create an IKE Gateway for the HA gateway's public IP.
2. Create a tunnel interface for the HA tunnel (such as tunnel.4).
3. Create a Static Route in the Palo Alto Networks firewall's Virtual Server pointed to the Aviatrix CIDR via the HA tunnel's interface (such as 10.68.0.0/16 via tunnel.4).
4. Set the Metric to 11.
Edits to Primary Tunnel Settings
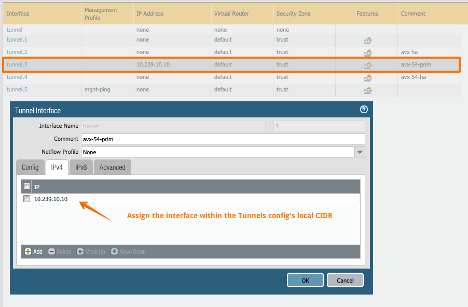
1. In the Interface column, double-click the name of the primary tunnel you created.
2. In the Tunnel Interface window, assign an IP to the Primary tunnel interface within the CIDR range of Site2Cloud's remote CIDR settings (such as 10.239.10.10).
3. Click OK.
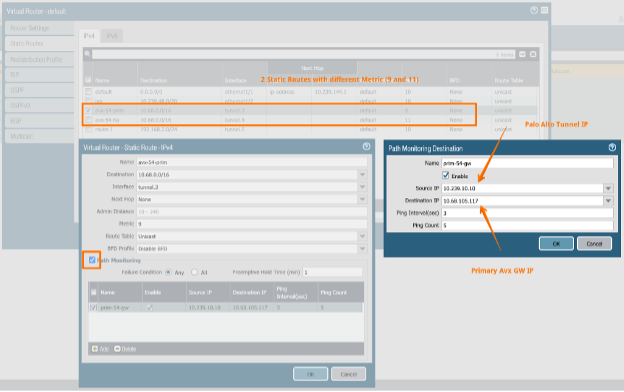
In the Virtual Router – default window, enable Path Monitoring on the Primary tunnel’s Static Route to trigger health checks (see screenshot below). The Palo Alto Networks firewall virtual IP will ping the Primary gateway’s IP address through the tunnel interface.
4. Double-click the Primary gateway.
5. In the Virtual Router – Statis Route IPvx window, select Path Monitoring. Click OK.
6. In the Path Monitoring Destination window, enter the Source IP for the virtual IP configured in the Primary Tunnel's IPv4 settings (such as 10.239.10.10).
7. Enter the Destination IP, which is the inside IP of the Aviatrix Gateway (such as 10.68.105.117).
8. Click OK.
9. Click OK to close the Virtual Router – Static Route window.
Conclusion
Failover takes about 20 seconds for the Palo Alto Networks firewall to adjust its routes to compensate for the primary tunnel being down. Failing back once the primary tunnel returns causes no lost pings.
