Problem Statement
As enterprises move their business-critical applications into the Cloud must provide extra protection and deep packet inspection following the defense-in-depth security model. This becomes extremely important for their public-facing workloads.
Some CDN service providers such as Akamai, Cloudflare, etc. have their own security mechanisms but there is also a need to provide an extra layer of protection via NGFW after traffic is landed in respective public cloud VPC/VNETs.
This document shows a real-world deployment we have done for a very large hospitality chain using Akamai as a CDN provider and Check Point CloudGuard for NGFW services.
Technical Requirements and Native Solution Challenge
- This global hospitality chain has a requirement to use Akamai Web App Protector with their GCP GKE Cluster.
- Additionally, security requires all traffic to pass through a Check Point NGFW.
Akamai WAP
- Akamai WAP behaves like a reverse proxy and forwards traffic to the destination after adding its value.
- The destination can be any Public IP.
- In GCP's case, that is typically a Load Balancer can be a Public IP.
- GCP firewall rules are then used to restrict source IPs to the Akamai ranges.
GCP GKE
- As a Google product, GKE uses native load balancers for Ingress.
- A Public HTTPS Load Balancer seems like a good solution and it's the one GCP recommends.
- In the GKE scenario, the Load Balancer targets the GKE Node VMs directly. There's no opportunity to insert an NGFW.
Aviatrix Intellgent Solution Details
Aviatrix provides an alternative; an easy, visible landing place for the GCP Load Balancer. GCP Load Balancers target VM backends, so we land a GCP Public TCP Load Balancer on a set of VMs running Nginx as a reverse proxy. Alternatively, we could have used the HTTPS Load Balancer and landed on the Aviatrix Spoke Gateways directly. In either case, the source IP of the traffic is changed to an Internal IP and routed to the GKE cluster.
Enabling firewall insertion in the Google Cloud Platform requires provisioning multiple NICs in multiple VPCs. This is fairly cumbersome to set up. Aviatrix enables intelligent, swift, and easy setup with Check Point and other firewall vendors without having to provision more than a handful of VPCs.
Topology
The diagram below shows a view of their POC deployment. Each Aviatrix Gateway collects Netflow, adding an additional level of visibility to the environment. I also helped them write the Terraform code. They enjoy enhanced security with features such as ThreatGuard.
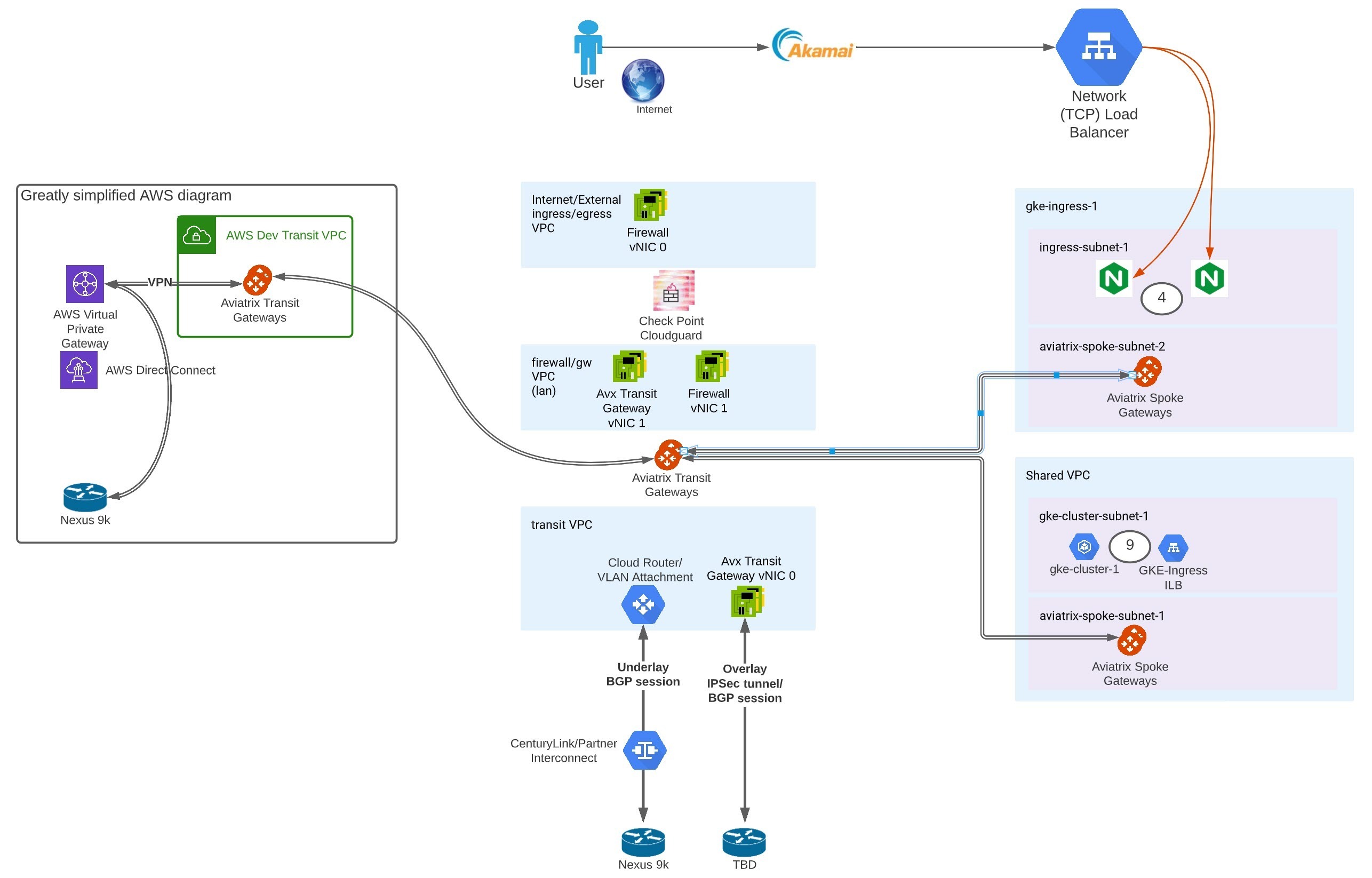
For more details please take a look here https://youtu.be/upxbqLrMIb4
Please reach out to schedule a demo and dig deep!

