For any additional questions you have about this concept, check out our FAQ page.
The Azure Architecture
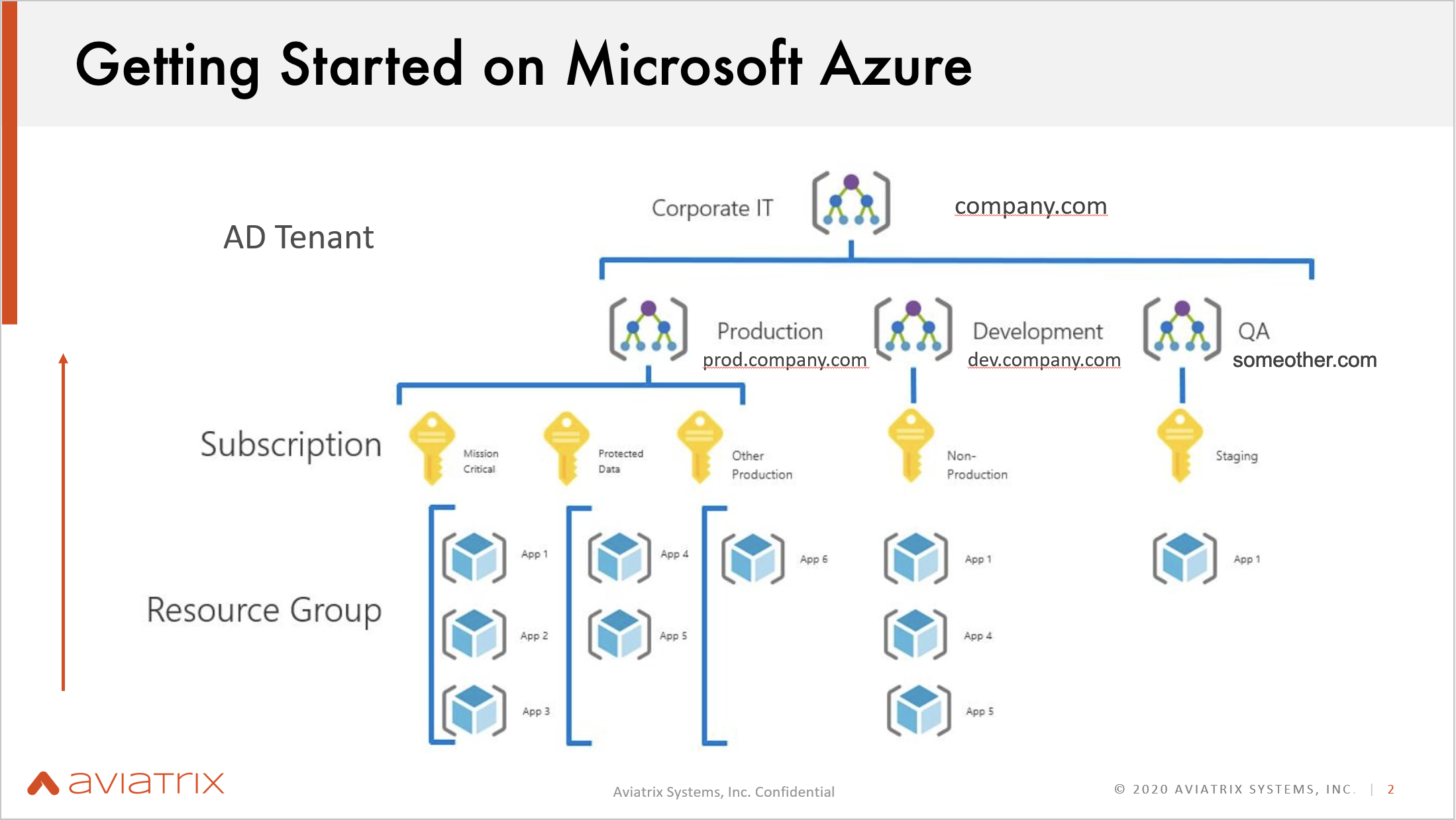
AD (Active Directory) Tenant
- This is a top-level domain that contains several subdomains.
Subscriptions
- These subscriptions are located in the subdomains.
- They allow users to access the services in Azure.
- A subscription is similar to an account in AWS.
Resource Groups
- Resource groups are located inside of the subscriptions.
- The resources are located inside of the resources groups, essentially as instances of the services.
- Some resources include Virtual Machines, Addresses, and Disks.
- There are no similar concepts to resource groups in AWS.
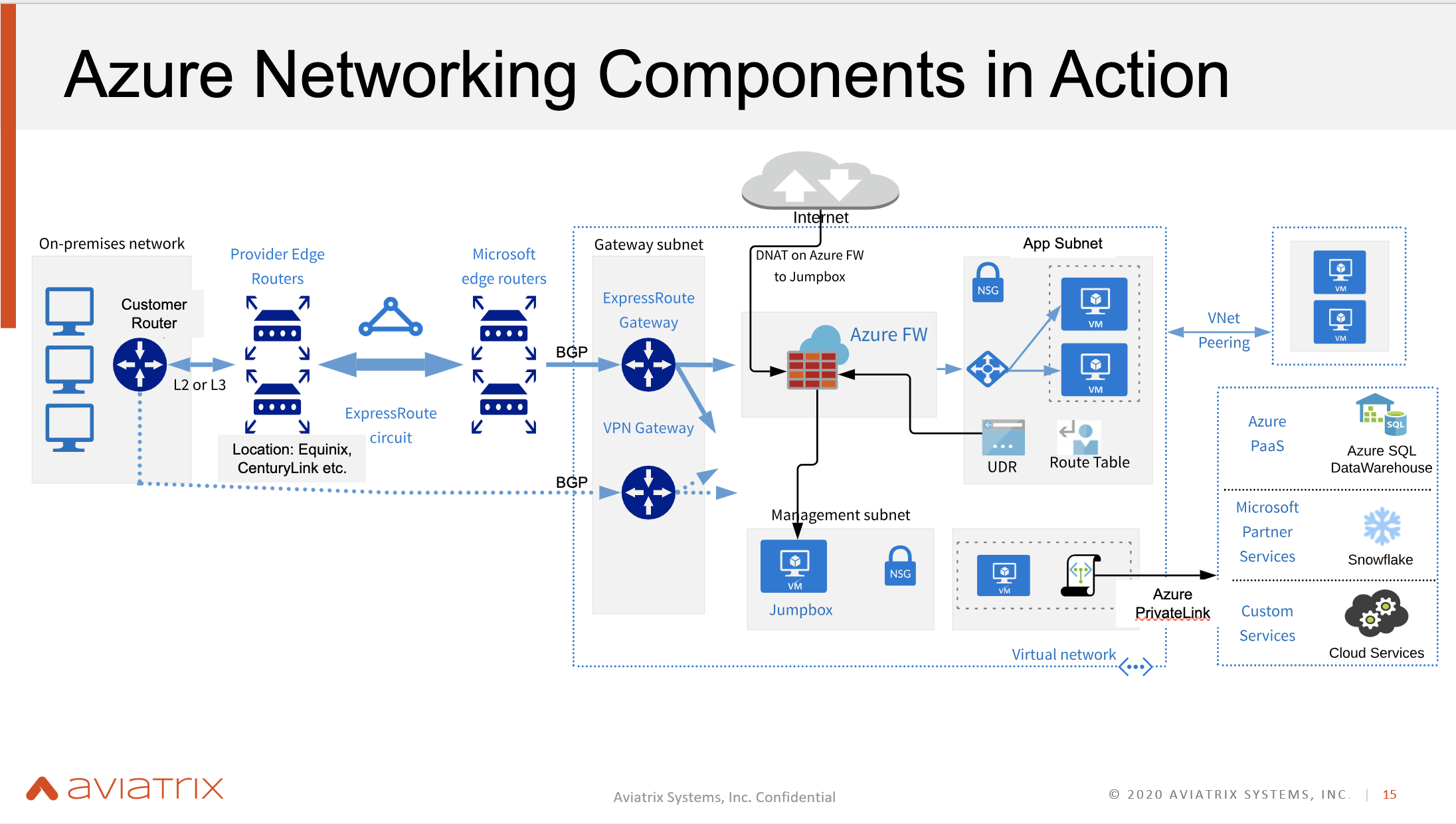
The Azure Networking Components
VNet
- This is the fundamental building block in Azure.
- It is similar to a VPC in AWS.
Availability Zone
- Essentially a Data Center located in a region.
Network Security Group
- A stateful firewall layer.
- Similar to an AWS Security Group
Public and Private IP Addresses
- In Azure, when users create VMs and specify a Public IP Address, it is automatically able to talk to the outside world.
- AWS requires an Internet Gateway in order to achieve this.
Virtual Network Gateway
There are two types of these in Azure.
VPN Gateway
- This connects on-prem to the VNet using the public internet.
- It must be deployed in a Gateway Subnet.
- A VPN Gateway is similar to the VGW in AWS.
- There is also a local network gateway which is the on-prem entity. This local network gateway is similar to the CGW in AWS.
Express Route Gateway
- This is popular amongst enterprises connecting their on-prem to the cloud.
- This is essentially a dedicated private line for connecting VNets to the Data Centers.
VNet Peering
- This is a native construct provided by Azure.
- However, it is not scalable.
Routing: UDR, BGP and System Routes
- User Defined Routes are static and user defined.
- System Routes are programmed routes that users can't see in the Azure portal.
Azure Load Balancer
- This is a L4 load balancer. Users can also use the Application Gateway for L7 load balancing.
Transit in Azure
Transit is essential in every cloud, and Aviatrix's solutions make transit easier. These transit solutions help greenfield and brownfield customers.
Azure also provides options for transit. It has three native options for inter and intra region transit.
ExpressRoute Edge Router
- This is a common solution but has a lot of limitations.
- It's default is Any to Any for all spokes, meaning that they can all communicate.
- There is also a lack of visibility and control.
- This feature is not officially documented.
- It is a shared resource.
Network Virtual Appliance (NVA)
- Customers usually deploy a firewall or third part appliance in the NVA and use it as a transit solution.
- This solution isn't easily scalable and requires a lot of manual work.
- There is limited visibility and control.
- The management of the static routes is challenging for enterprises.
VNet Peering
- This is Microsoft's preferred option. However, even this solution is difficult to use.
- Users have to create 1-to-1 mapping.
- This solution also doesn't scale and the VNet peering needs to be broken to add components.
Azure Virtual WAN
This is Microsoft's proposed solution for the limitations of the native transit solutions. The Azure Virtual WAN has some drawbacks, however.
- This solution is not Multi-Cloud friendly.
- Users must buy all the features in order to use this solution.
- The hub location doesn't support third party devices.
- Troubleshooting and visibility are limited.
- There is no way to control the routing policy.
- There is a 200 BGP route limit from Azure to on-prem.
For more information, watch the video above.