Aviatrix provides the industry’s first enterprise-class, fully embedded, secure egress solution that is purpose-built for cloud. This solution brief discusses the key features of Aviatrix Secure Egress, and how it can improve your overall security posture and lower security spending compared to existing solutions.
Cloud is the new ground zero for hackers
As more business-critical workloads move to cloud, hackers are taking notice. According to a recent report1 , cloud exploitation grew by 95% in 2022, representing a 3x increase in attacks specifically for cloud. Similarly, Venafi reported2 that 81% of companies experienced a cloud security incident in 2022. Cloud applications can no longer afford to be under-protected, especially against new attacks specifically designed to infiltrate critical cloud systems.
You can’t protect what you can’t see
Unlike a traditional data center, public clouds are designed to give an application quick and easy access to the Internet anywhere it is deployed. This makes cloud applications notoriously challenging to protect. Adding to this difficulty is the fact that cloud applications can be deployed in hours or even minutes, making it hard for security teams to keep up. Yet, without a secure egress solution, your cloud applications can talk to malicious endpoints or even steal your data, and you would never know it.
The downside of virtual firewalls in the cloud
Even though virtual firewalls provide the features needed for deep egress protection, they were never designed for public cloud. They are still point solutions optimized for the data center. Security teams relying on virtual firewalls must deal with the big sticker price, single points of failure, and a lack of agility, all issues that slow down cloud adoption. These delays can frustrate application owners, who look for more straightforward solutions to give Internet access to their quickly growing lines of business.
The Virtual DMZ in theory
The diagram below depicts a standard virtual DMZ architecture for processing outbound traffic. The typical design pattern relies on static routes to force outbound traffic from assigned app groups (or business units) into the virtual DMZ. Multiple virtual DMZs can be built depending on availability zone, region, or data classification. Known or trusted traffic can egress after inspection, while malicious or untrusted traffic is blocked and identified for further remediation. For threat identification to be as effective as possible, the firewall must inspect application-level data.
Forcing application traffic to be in line with the firewall is a straightforward affair in the data center, where Internet egress is concentrated into a single point – the corporate DMZ. In public cloud, however, Internet access is just one click away from any application, making the implementation of a virtual DMZ a complex, expensive, and cumbersome endeavor. To achieve the ideal outcome, security teams must constantly worry about correct routing across the network to force traffic from all lines of business through the firewall. Sometimes this requires an invasive redesign of the existing architecture so formally isolated network segments become inter-connected.

The Virtual DMZ in practice
While this design works great in theory, it often fails in practice. Why? Because in public cloud, it is difficult or impractical to force Internet access into a consolidated point. New applications are constantly deployed in cloud, and many can bypass the virtual DMZ for a whole host of reasons: loose governance, oversight, human error, and so forth.
In other scenarios, cloud security teams must yield default Internet access to DevOps teams or customers who require more agility, flexibility, or self-governance than the virtual DMZ can provide. This weakens or breaks the overall design. The diagram below depicts a more realistic scenario in public cloud, where the virtual DMZ is not the only available path to the Internet, thereby enabling malicious activity in the network.
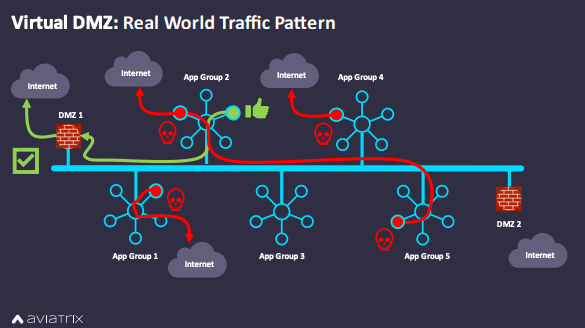
In the case of App Group 1, a NAT gateway provides default Internet access, so an infected VM is performing data exfiltration to a public endpoint, evading detection. In App Group 4, a DevOps team has opened default Internet access to a VM for software updates, allowing a malicious bot to phone home to a dark proxy on the Internet.
In the last example, a hacker has compromised a VM in App Group 5 and a VM in App Group 2 using stolen credentials and has formed a tunnel between them, allowing lateral movement through the network to gain Internet access. The hacker is using trusted protocols, like SSH, RDP or HTTP, to slip through security rules and form the tunnel. The VM in App Group 2 has access to the Internet simply due to human error: an incorrectly configured route on the NIC. The hacker plans to use this outbound connection to form another tunnel and install ransomware on this VM.
A closer look at cloud-native solutions
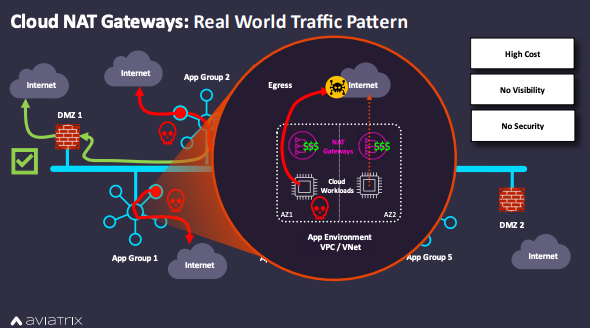
Cloud-native solutions like NAT gateways give DevOps teams the speed and agility they need, as they are simple to manage and quick to deploy. This makes them popular for agile applications and non-production workloads. However, this simplicity comes at a double cost - NAT Gateways are expensive on the meter, yet provide no inspection at the application layer, where the most dangerous threats are lurking.
Many security teams leave these solutions in place because they cannot find a better solution to meet growing business demands. Or perhaps it is because central IT does not control the NAT gateway. You can see in the diagram below just how easy it is for a compromised VM to connect to a malicious endpoint on the Internet because the NAT Gateway cannot examine the traffic or perform threat analysis. Outbound connections to the Internet can be just as dangerous as inbound connections. Experienced hackers know how to create tunnels using this method to pass data into and out of the infected machine.
What is the ideal solution? The ideal solution for secure egress in cloud needs to provide enterprise-class security and threat detection with a simple-todeploy, manage, and scale solution that enables agile frameworks. It should also embed security into the entire network by default without disrupting or impacting your existing architecture. Finally, this solution should reduce security spending, improve security posture, and make monthly costs more predictable.
Aviatrix Secure Egress: Embedded protection, purpose-built for Cloud
Aviatrix Secure Egress was built for the cloud. It was designed from the ground up as a cloud service in AWS, Azure, GCP, or Oracle. It embeds deep application visibility, geo-blocking, and industry-leading threat detection throughout your entire cloud network, creating a distributed perimeter around all your lines of business. Aviatrix Secure Egress is an agile solution that leverages automation and cloud-native orchestration to enable rapid deployment, be it at global scale, a single region, or just one application at a time. As a one-to-one replacement for NAT Gateways or virtual firewalls (or both), it can be deployed at a far lower cost and features fixed monthly billing. The solution is managed centrally through Aviatrix CoPilot, which provides deep insights into existing and emerging threats in a single pane of glass, leading to higher mean time to detection (MTTD) and mean time to resolution (MTTR). Most importantly, Aviatrix Secure Egress protects your cloud applications where it matters most – anywhere and everywhere they face the Internet in cloud. This gives security teams and application owners the complete protection and peace of mind required to build and scale business-critical apps in the cloud.


