We work with many of our customers who are either in the process of building their hybrid deployment or are looking for ways to optimize their connectivity. When it comes to connecting on-prem resources to the public cloud, there are generally two options available. One common approach is using IPsec site2site VPNs over the public internet. But as cloud deployments mature and more mission-critical traffic flows between on-prem and cloud, the latency and throughput expectations increase, demanding more dedicated connectivity with better SLA and quality than public internet.
In AWS, AWS Direct Connect (Dx) offers enterprises an option to connect their on-premises resources to their AWS environment over a private, dedicated circuit that’s isolated from the public internet and offers a more predictable performance.
What is a VIF?
Once the Dx connection is set up by the provider, in order to bridge the Dx connection into VPCs, users need to use a Virtual Interface (VIF). A VIF is a logical interface that glues the connection from the cloud network to the Dx connection. Generally, Dx connections can be owned by the end-user, or it can be hosted by someone else for you. This can be another provider or someone in your organization who owns the dedicated fiber connection. In the case of the latter, this would be called a hosted VIF. Once a VIF is created on the owner’s account, the user needs to accept and setup the connection for their environment using the AWS console.
How does VIF connect to other constructs?
After VIF is created on the owner’s account, a VIF connection request will appear under the direct connect service. See the screenshot below:
At this point, the VIF is ready to be accepted. When you hit “Accept Virtual Interface”, you will be presented with two options for connecting the VIF to your cloud environment. See screenshot below:
As shown above, there are two ways to attach your VIF, Virtual Private Gateway (VGW) or Direct Connect Gateways (DxGW). It's important to note that once you select a connection type and accept the connection, you can’t modify it. For example, if you chose to connect your VIF to Direct Connect Gateway, then you can’t go back and change that to Virtual Private Gateway. A new VIF needs to be created, which can be time-consuming to coordinate.
Let’s look at these options and their differences:
Connecting to Virtual Private Gateway :
Connecting VIF direct to a VGW will limit to a single VGW in the same region as the connection. The advantage is that you will be able to connect to this VGW using IPSec/BGP and propagate routes from on-prem further using any routing device that supports these protocols. You can also attach the VGW directly to a VPC, which is very limiting in the architectural sense.
Connecting to Direct Connect Gateway :
For more flexibility, you can connect the VIF to a DxGW. You can then associate this DxGW with VGWs that are in different regions. This will allow you some flexibility to split and share the VIF across different VPCs and regions. The drawback is that the VGW that’s behind the DxGW can only be connected to a single VPC. In this mode, VGW can’t be used to further advertise on-prem routes to another IPSec/BGP neighbor to create connectivity with multiple VPCs. Another limitation here is that DxGW is not transitive, meaning you can’t route traffic between VPCs in this fashion
Ideal Architecture
Our desired architecture has the flexibility to connect our on-prem resources to the cloud using a design that supports the dynamicity we need in the cloud. Most critically, if we are terminating a dedicated connection from on-premises to the cloud, we need to be able to use that connection to connect to any of our resources in different VPCs, regions and cloud on-demand. This provides us with the flexibility and agility that we need to operate in the cloud
How Aviatrix Transit Integration with Dx Works
Aviatrix cloud controller allows users to create and manage hybrid and multi-cloud connectivity using Aviatrix AVX Transit Service.
Using a simple point-and-click workflow user can connect an Aviatrix transit gateway with a VGW that’s hanging off the VIF. Once the connection is established, the Aviatrix controller manages both control and data plane aspect of the network to ensure end-2-end network correctness.
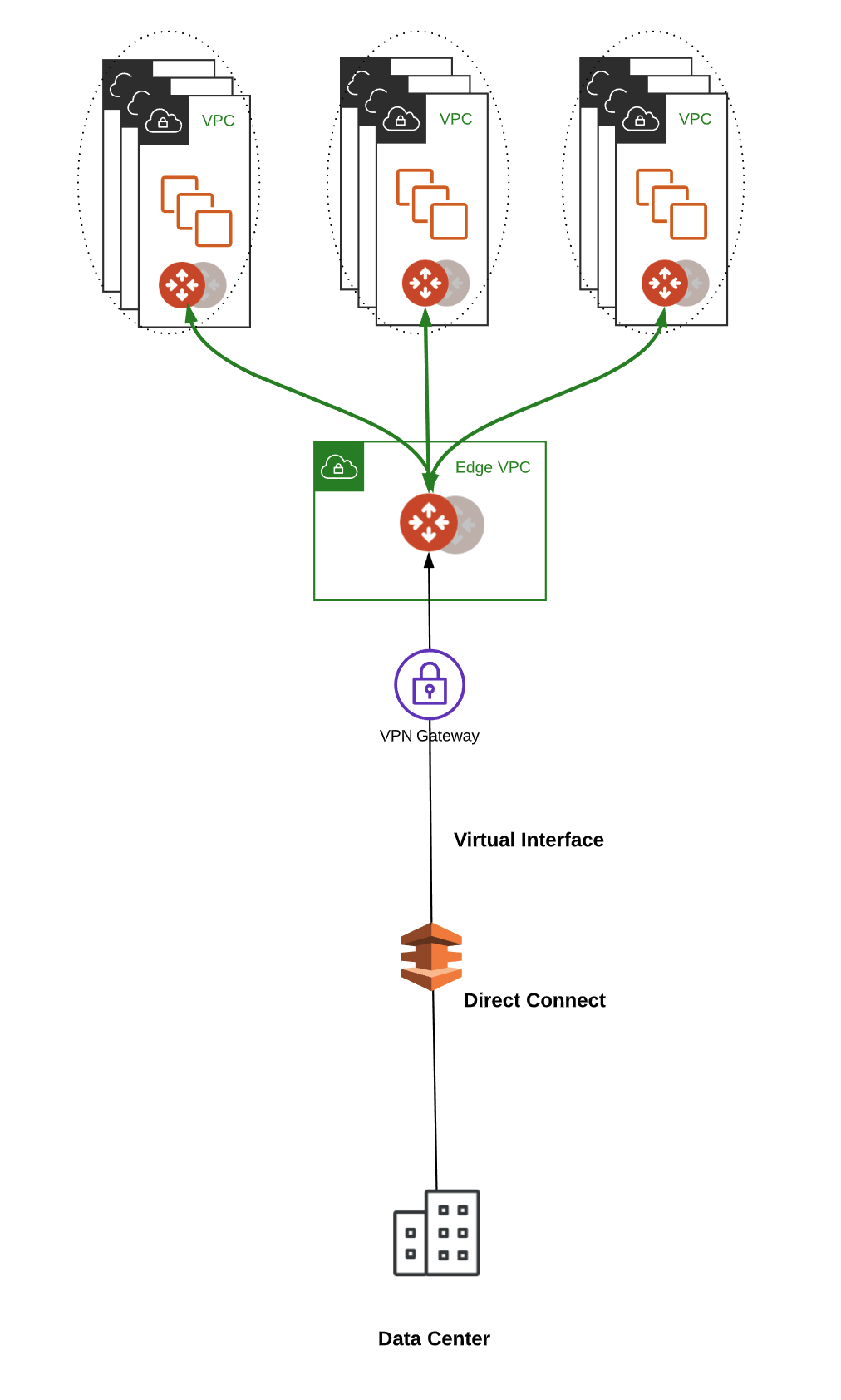
Aviatrix global transit is able to connect to this VGW, learn the on-prem routes as stated above, and ensure full propagation and connectivity across cloud networks in different regions or different clouds. Aviatrix transit gateways provide a flexible, secure, and highly available data path between all of the VPCs and on-premises.
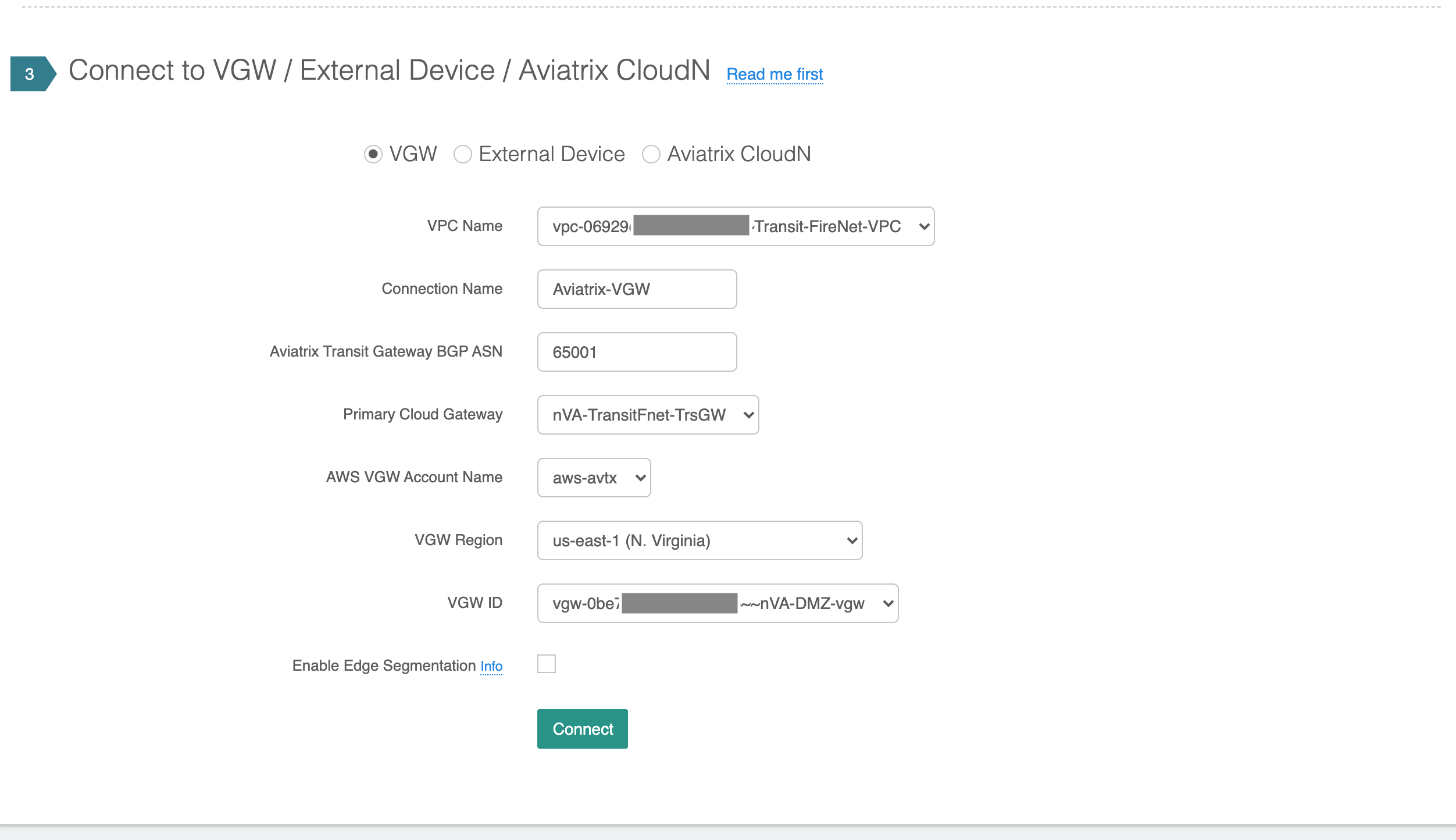
To do that, in the last step above, chose “Virtual Private Gateway (VGW), and then choose the VGW that is to be connected to an Aviatrix transit gateway. Once the VIF is connected to a VGW, and VGW is connected to Aviatrix transit gateway, Aviatrix transit network will learn about the on-premises routes and automatically propagate them throughout the rest of the transit network. At this point, your hybrid cloud is set up and connected end to end.
Some of the advantages of using Aviatrix Transit :
-
Global Transit Service allows connecting to any regions or any cloud
-
Global network segmentation for secure connections
-
Automatic route propagations in the VPCs based on the connection policy
-
Rest API and Terraform support
-
Custom firewall rules for fine-grained traffic control
-
Flexible usecase coverage.
-
Repeatable design across regions and clouds

