Aviatrix customers have many options for enabling secure egress from their cloud environments:
- Aviatrix own secure egress with FQDN filtering (link)
- Egress through a firewall (Palo Alto, Checkpoint, Fortinet) (link)
- Any other 3rd party tool
The instructions below show you how to configure the 3rd scenario, with zscaler as the external tool:
- The IPSec tunnel to ZScaler needs to be established from Transit VPC GW:
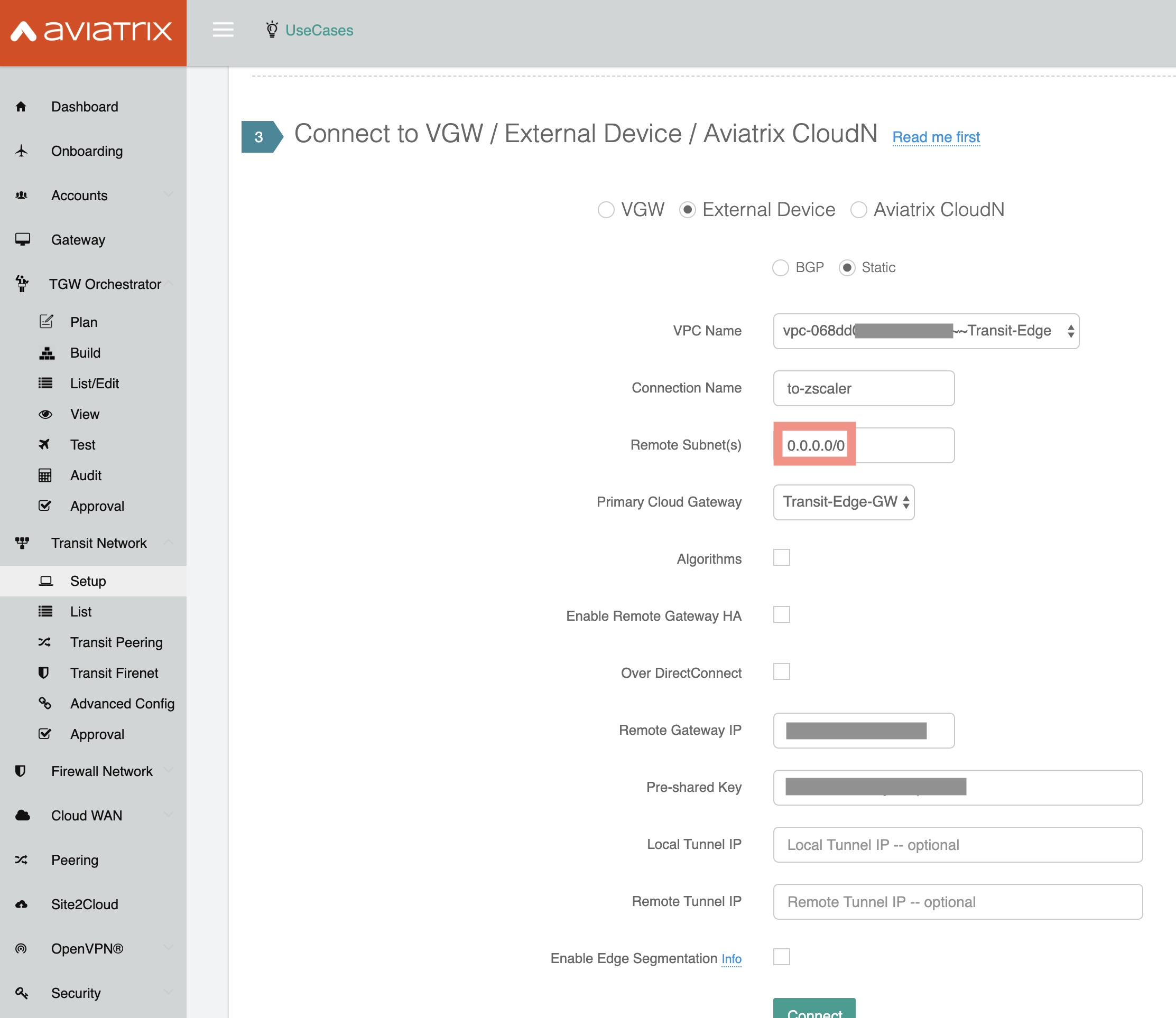
- Transit Network > 3. Connect to VGW / External Device / CloudN
- Option External Device > Static
- Remote Subnet is 0.0.0.0/0
- You can select the Pre-shared key, but it’s a good idea to let the controller define the Local and Remote Tunnel IP
- When building the tunnel from the remote end (ZScaler) to the Transit VPC GW, you will need to input the following:
- Remote subnets - the CIDRs of the VPCs connected to the AWS TGW (in the domains that are connecting to ZScaler) and the Transit VPC CIDR
- Pre-shared key
- Local and Remote Tunnel IP
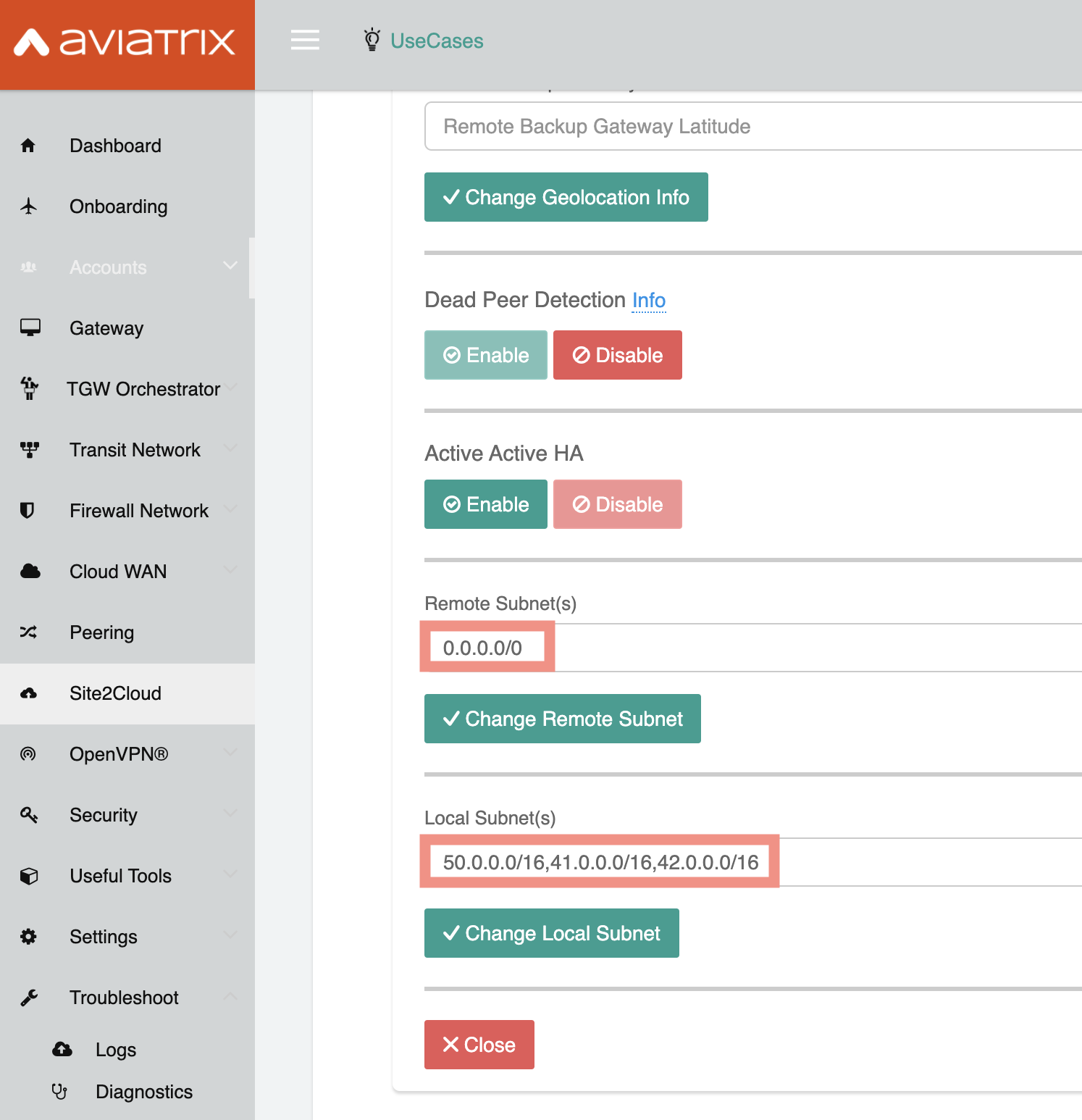
- (If the controller generated the b. or c. you need to download the configuration file from Site2Cloud menu: select the created tunnel, select Generic Vendor and download the configuration file, which will have these details. Make sure to not mix up what is remote and what is local. The imported file will be naming IPs from the perspective of ZScaler - these will be local attributes)
- In Site2Cloud, in the details of the tunnel, update “Local subnets” to include CIDRs of all the VPCs that should be connecting to ZScaler.