Compliance mandates often require encryption in transit as well as encryption at rest. Production web servers should be accessible only by HTTPS (TCP port 443). However, sometimes developers test their apps on HTTP initially but then forget to implement controls to secure it over HTTPS. This article shows how you can use Aviatrix CoPilot to see if a web server in your cloud environment is still running on HTTP.
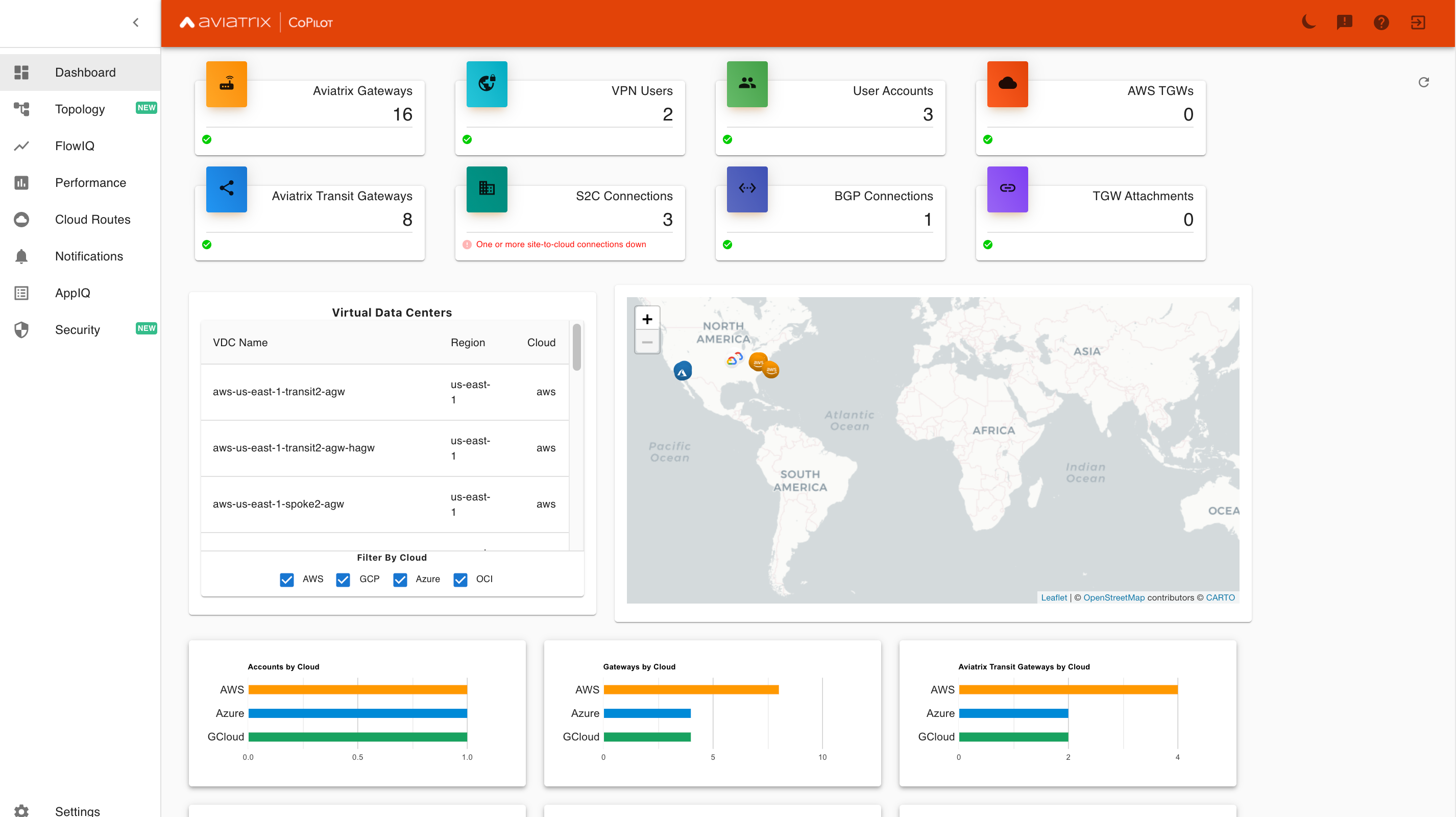
This is a CoPilot Dashboard view of a multi-cloud environment running in AWS, GCP, and Azure regions in North America.
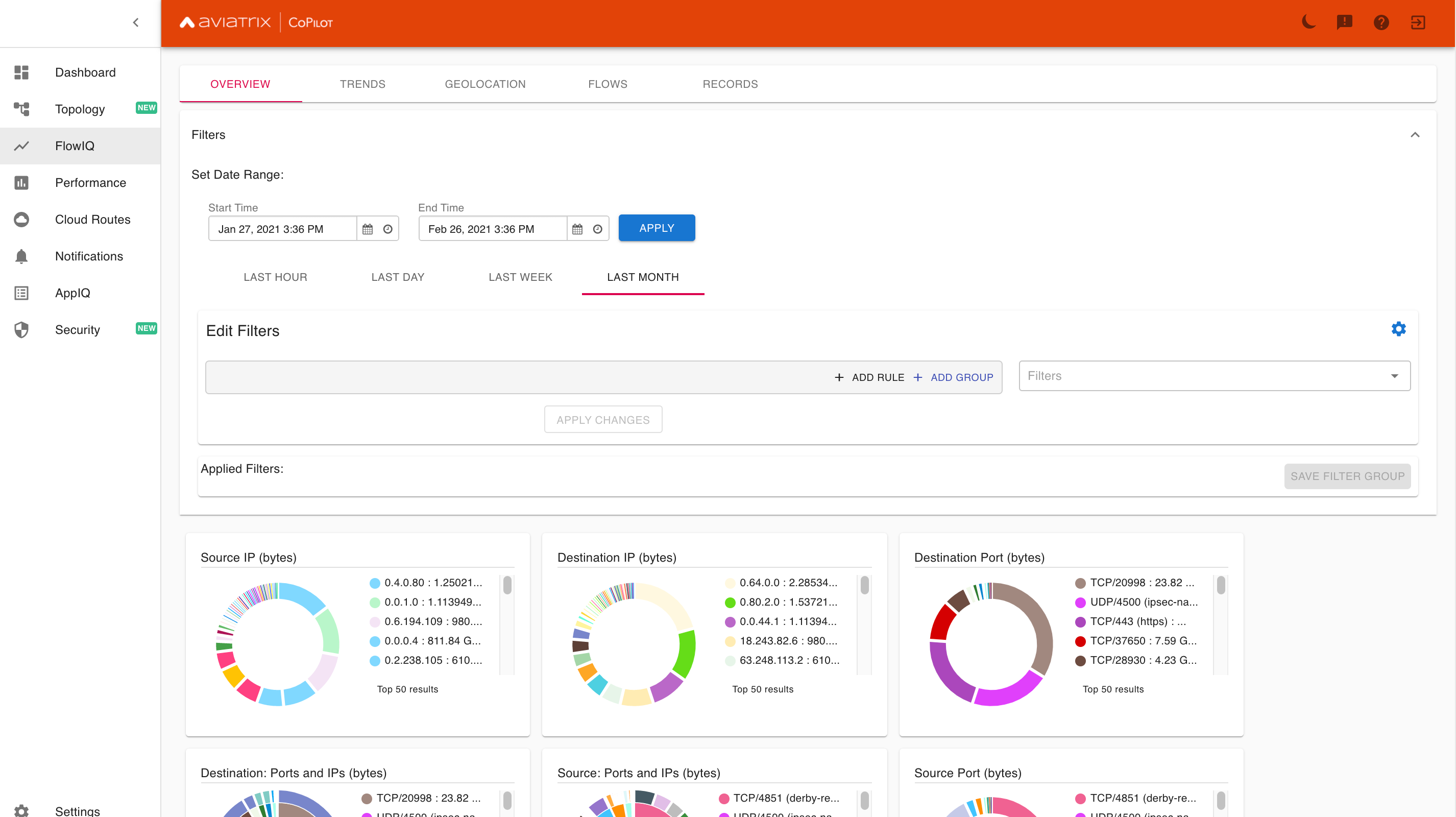
CoPilot FlowIQ allows you to slice and dice data based on NetFlow records. This view of FlowIQ shows top-talkers from the past month.
By adding a filter of Destination Port is equal to 80, you can hone in on all traffic in the past month on TCP port 80 (HTTP).
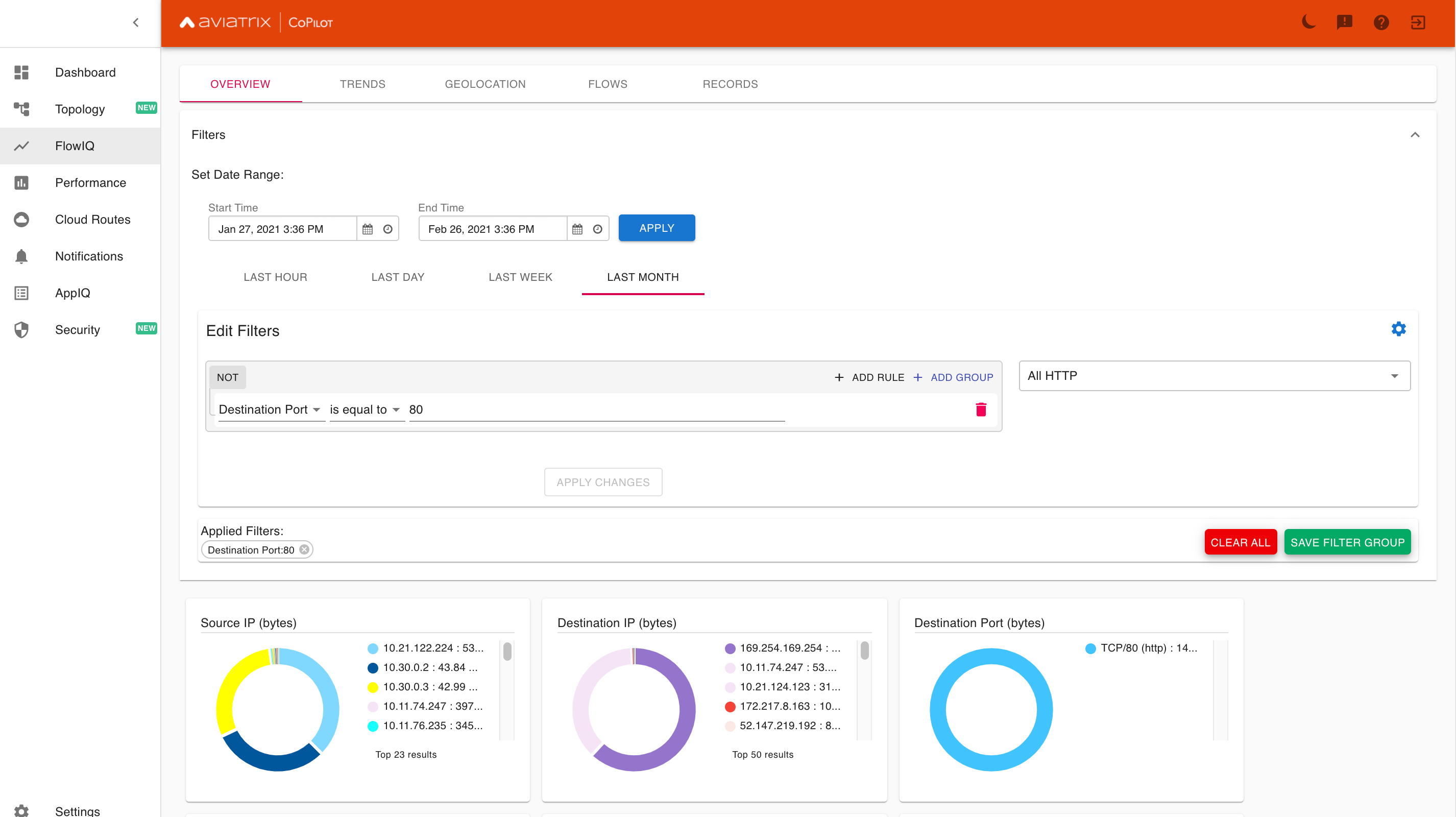
However, as you can see from the Destination IP (bytes) pane, the list includes many hosts that are outside of your concern. For example, when you run a sudo apt-get update or sudo yum update to get patches, those commands run over HTTP, not HTTPS. We need a way to filter on traffic local (not external) to the cloud network. Fortunately, NetFlow provides us field to do so. It is called Flow Locality and it needs to be set to private.
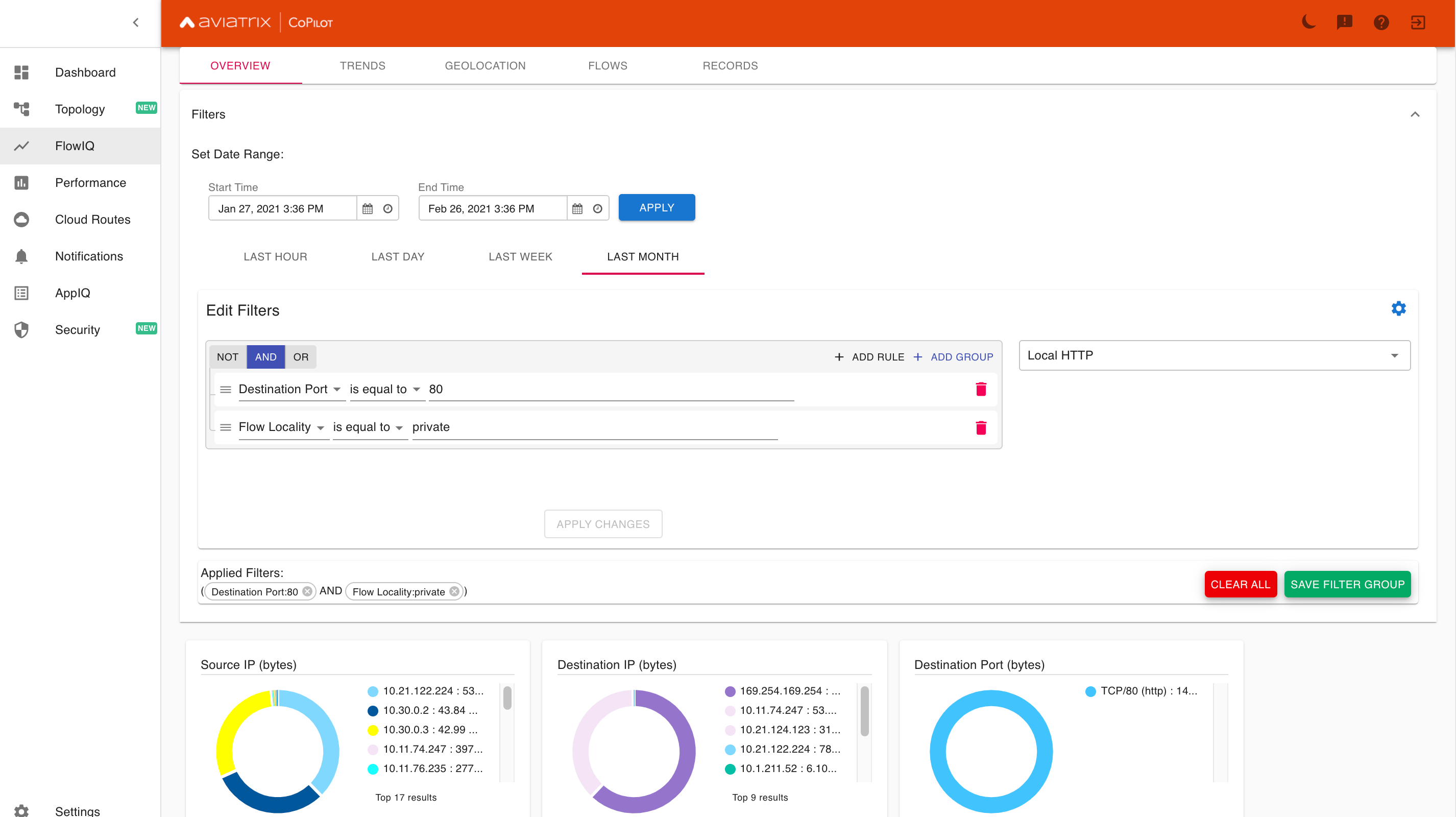
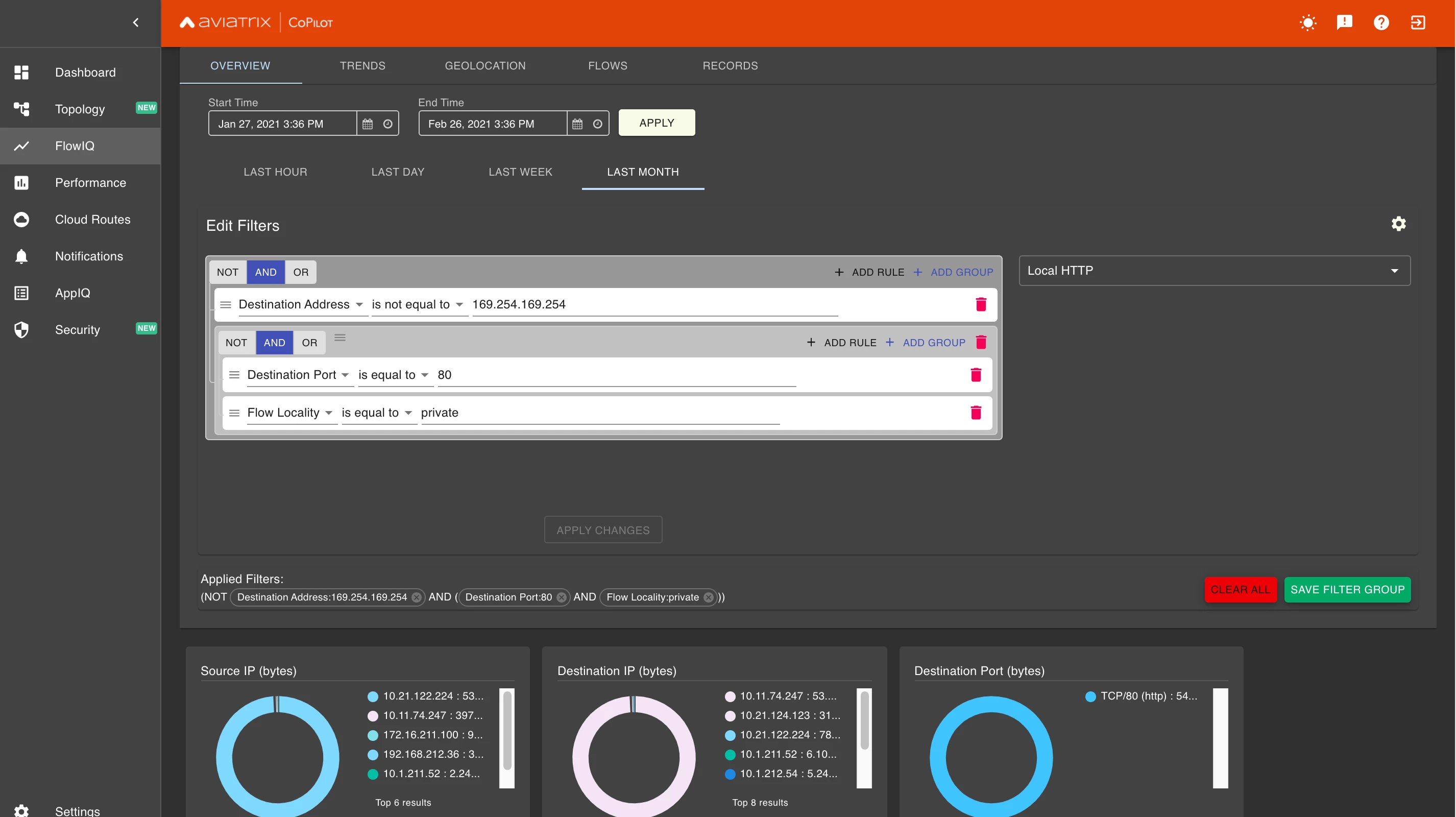
Notice that the Destination IP (bytes) pane includes an entry for 169.254.169.254. This is the result of an AWS EC2 instance running curl http://169.254.169.254/latest/meta-data/. We can filter further by excluding that private IP.
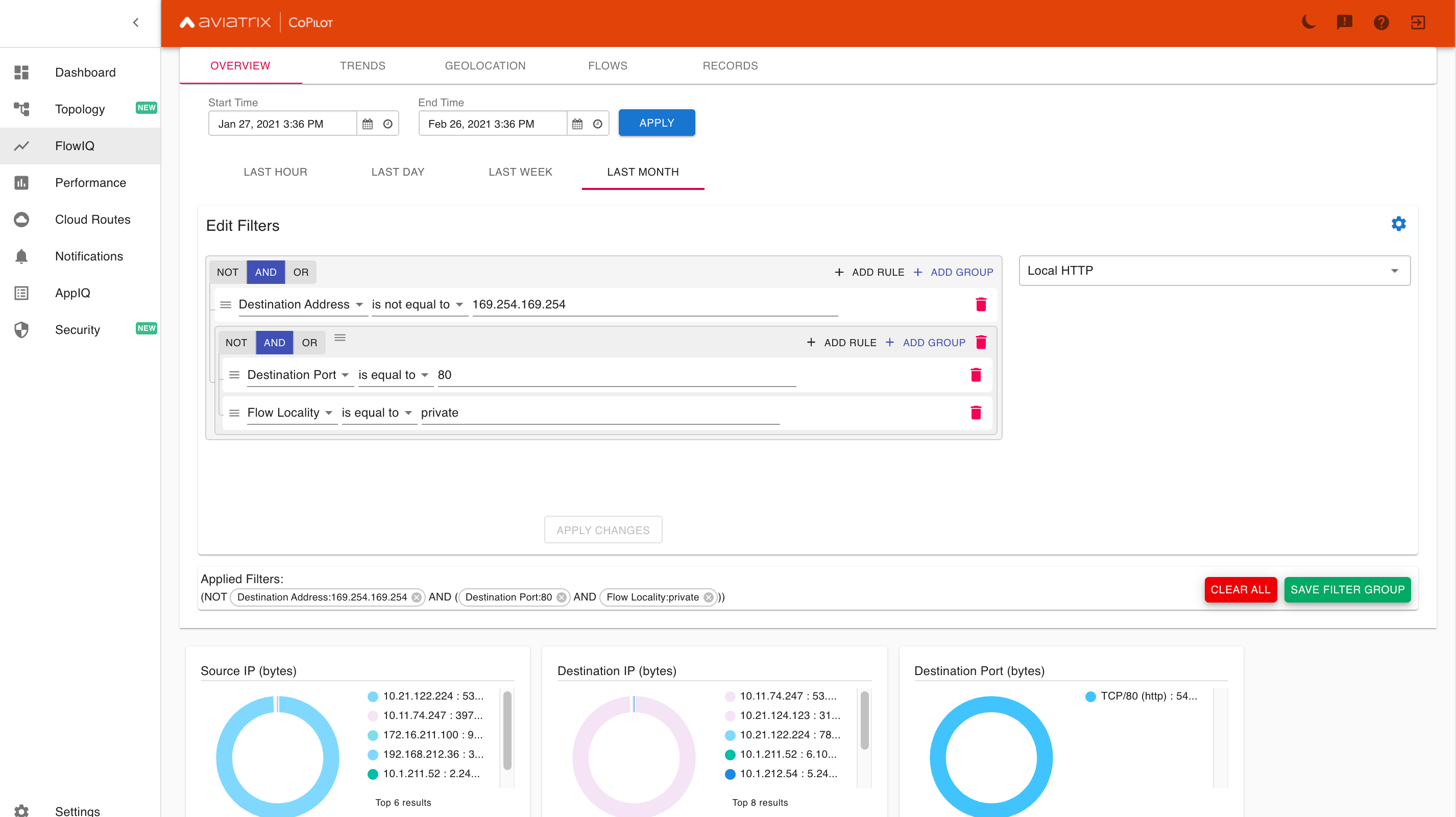
Now we have a definitive list of all local web servers in our environment that are running on TCP port 80 instead of 443. We can take this evidence to the developers and ask them to secure their apps.
View the same output above in Dark Mode by toggling the Crescent/Sun button in the top-right corner.