In this post, we will look at Panorama integration for the Aviatrix FireNet use case. Panorama is the Palo Alto Network's security management server. With the Panorama UI interface, one can manage and monitor traffic for multiple Palo Alto NGFWs
This document will cover the steps to configure and integrate Panorama with Aviatrix Solution
Steps for Configuring Panorama
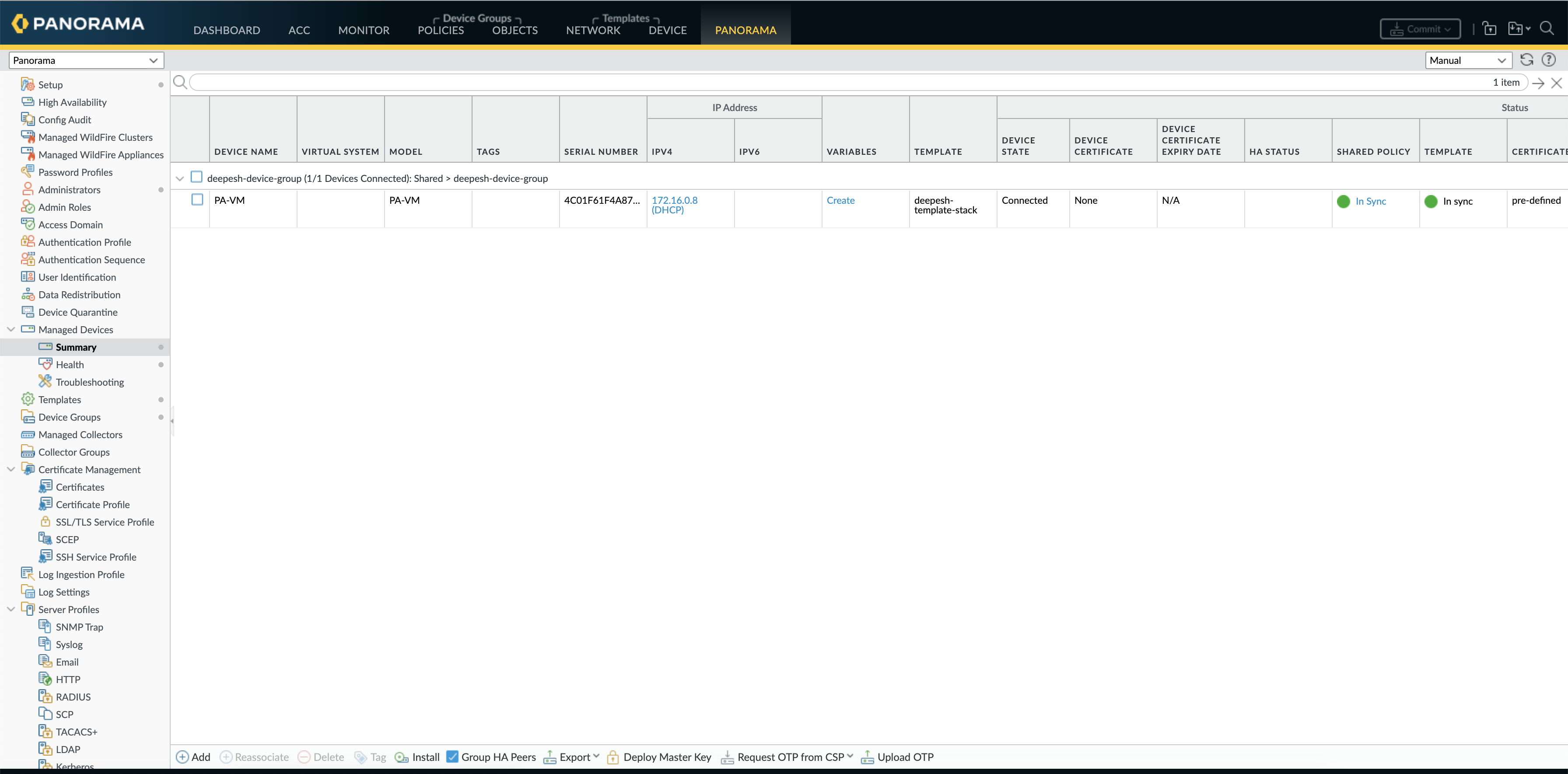
Step1 - Add the firewall to the panorama managed devices list
- Log into Panorama, select Panorama > Managed Devices, and click Add
- Enter the serial number of the firewall and click OK.
- Commit. For the Commit Type select Panorama, and click Commit again.
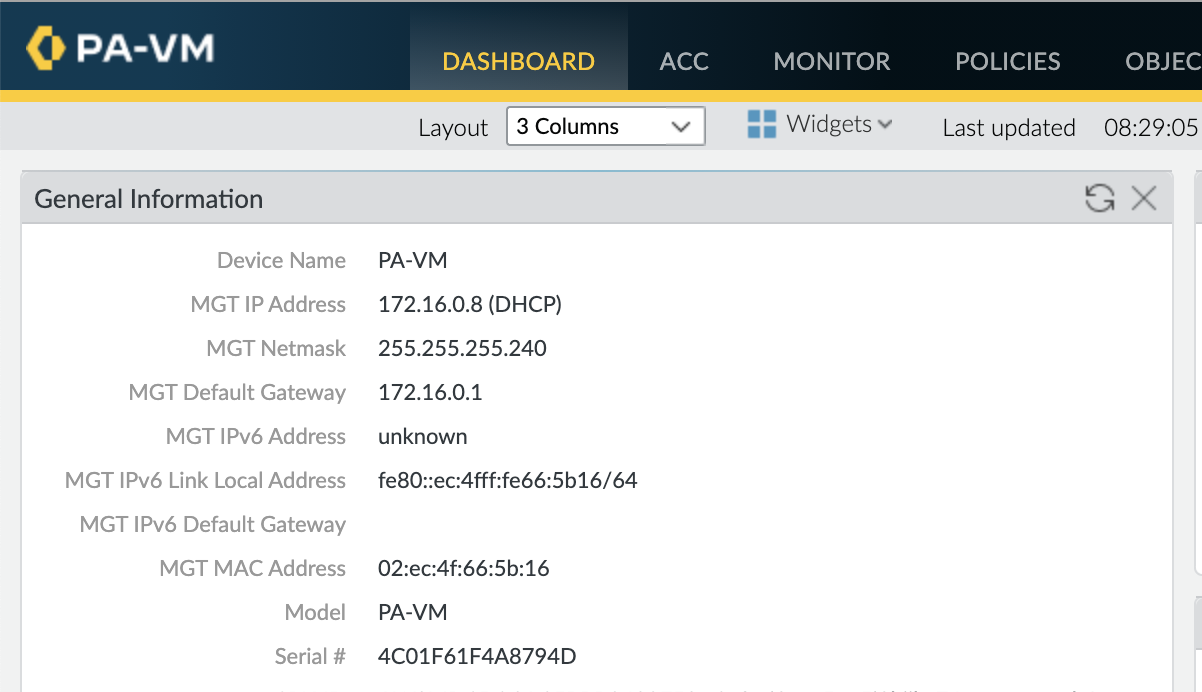
Serial Number can be found on the VM-Series dashboard as shown in the screenshot below
Step2 - Set up a connection from the firewall to Panorama
- Log in to the firewall, select Device > Setup, and edit the Panorama Settings.
- In the Panorama Servers fields, enter the IP addresses of the Panorama management server.
- Click OK and Commit.

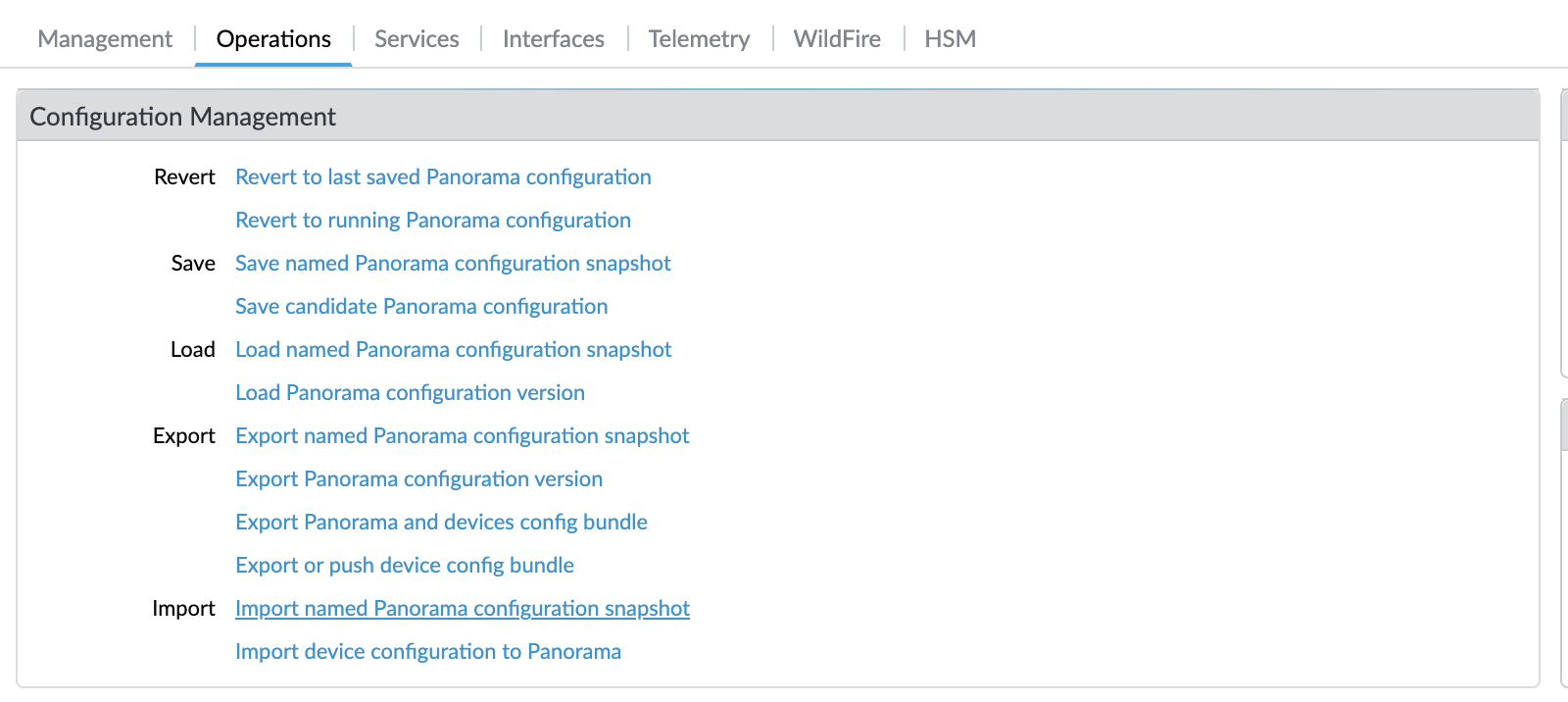
Step3 - Import the firewall configuration into Panorama
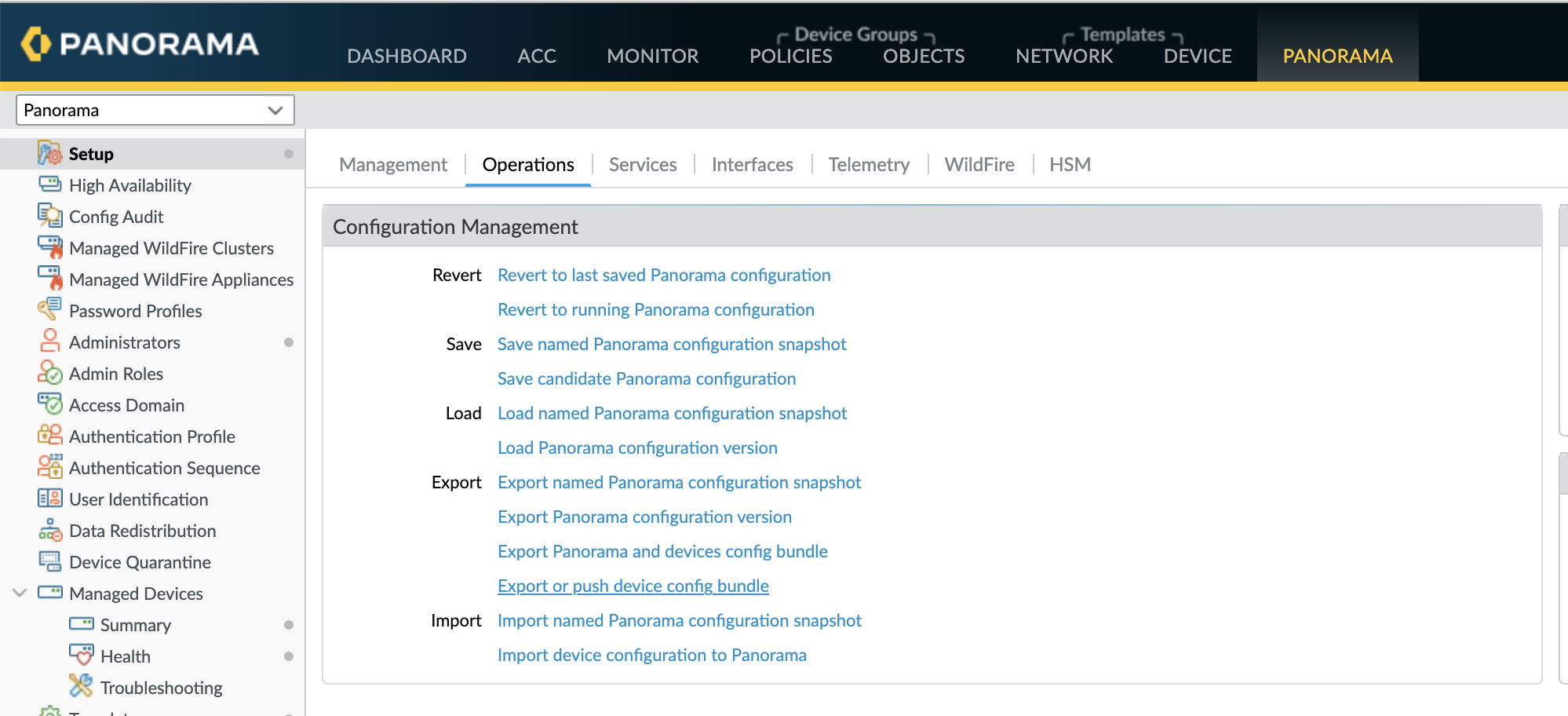
- From Panorama, select Panorama > Setup > Operations, click Import device configuration to Panorama, and select the Device.
- Panorama can’t import a configuration from a firewall that is assigned to an existing device group or template.
Step4 - Verify the configuration was imported properly
- Compare running and candidate config via Panorama > Config Audit > Go.
- If the configuration is good, click Commit and commit to type Panorama
Step5 - Push the device configuration bundle to the firewall
- This will remove all policies and objects from the local configuration.
- Go to Panorama > Setup > Operations and click 'Export or push device config bundle'.
- Select the Device from which you imported the configuration, click OK, and click Push & Commit.
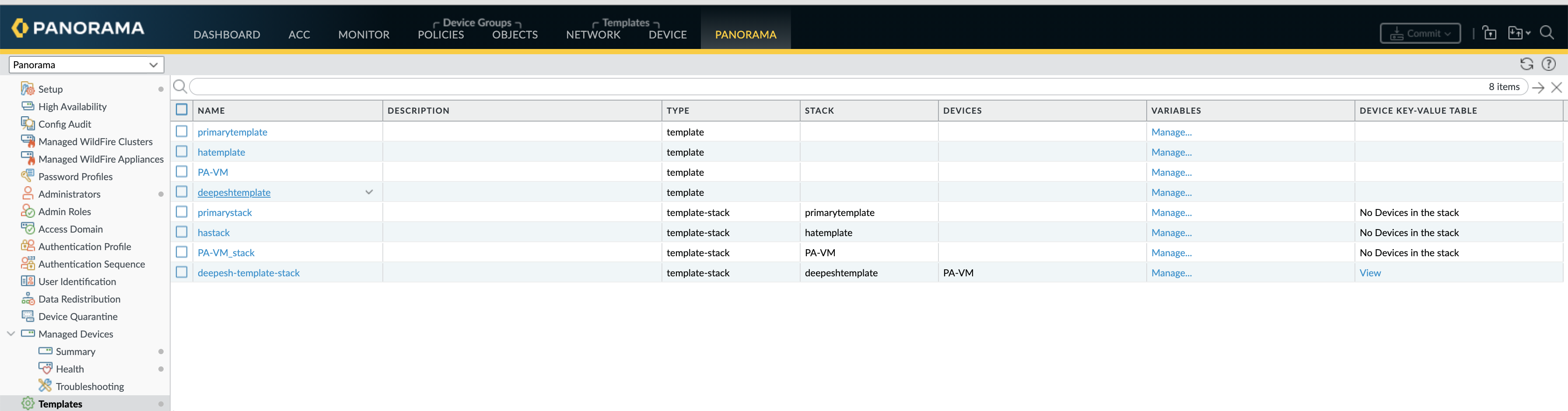
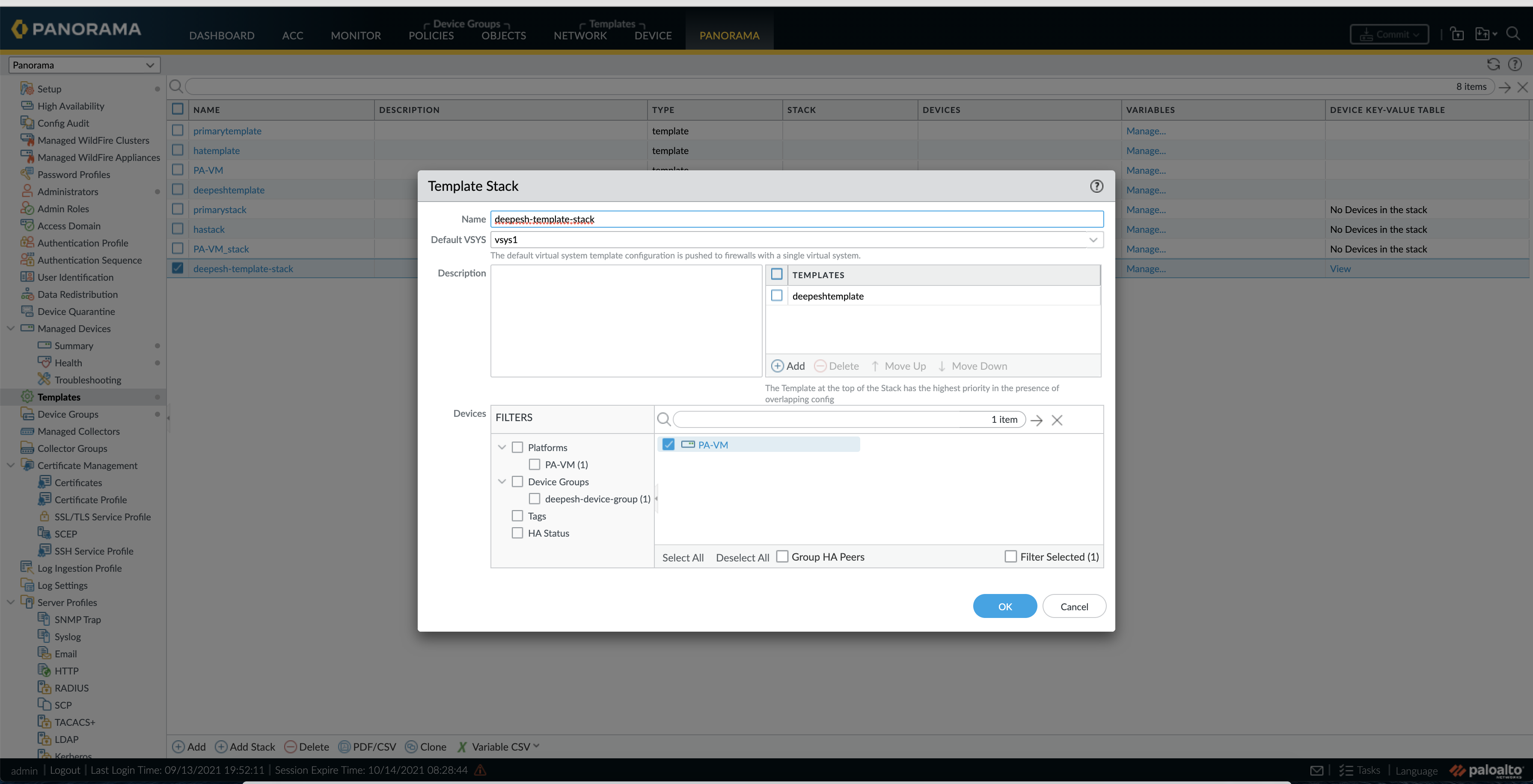
Step6 - Create Templates, Template Stack & Device Groups
Template and template stacks are used to configure network properties, such as interfaces, zones, and route tables. This is the one that we need to monitor and update through
- Panorama –> Templates-->Add (for template)
- Panorama --> Tamplates--> AddStack (for template stack)
Create Template
-
You should create a template for each firewall group: One for the FireNet primary gateway and one for FireNet backup gateway.
Configure Template
-
Add interfaces (ethernet1/1, ethernet1/2), zones (LAN, WAN), and Virtual Routers (route tables).
-
Do not name the route table as “default” since this may conflict with the firewall’s default route table.
-
Please refer to the step 7 and 10 of https://docs.aviatrix.com/HowTos/config_paloaltoVM.html
Create Template Stack
-
A Template stack is a bundle to bound templates with managed devices.
-
When creating, select template(s) and devices. Create one template stack for the primary FireNet gateway, another for the backup FireNet gateway. Remember the template stack name. Commit and push
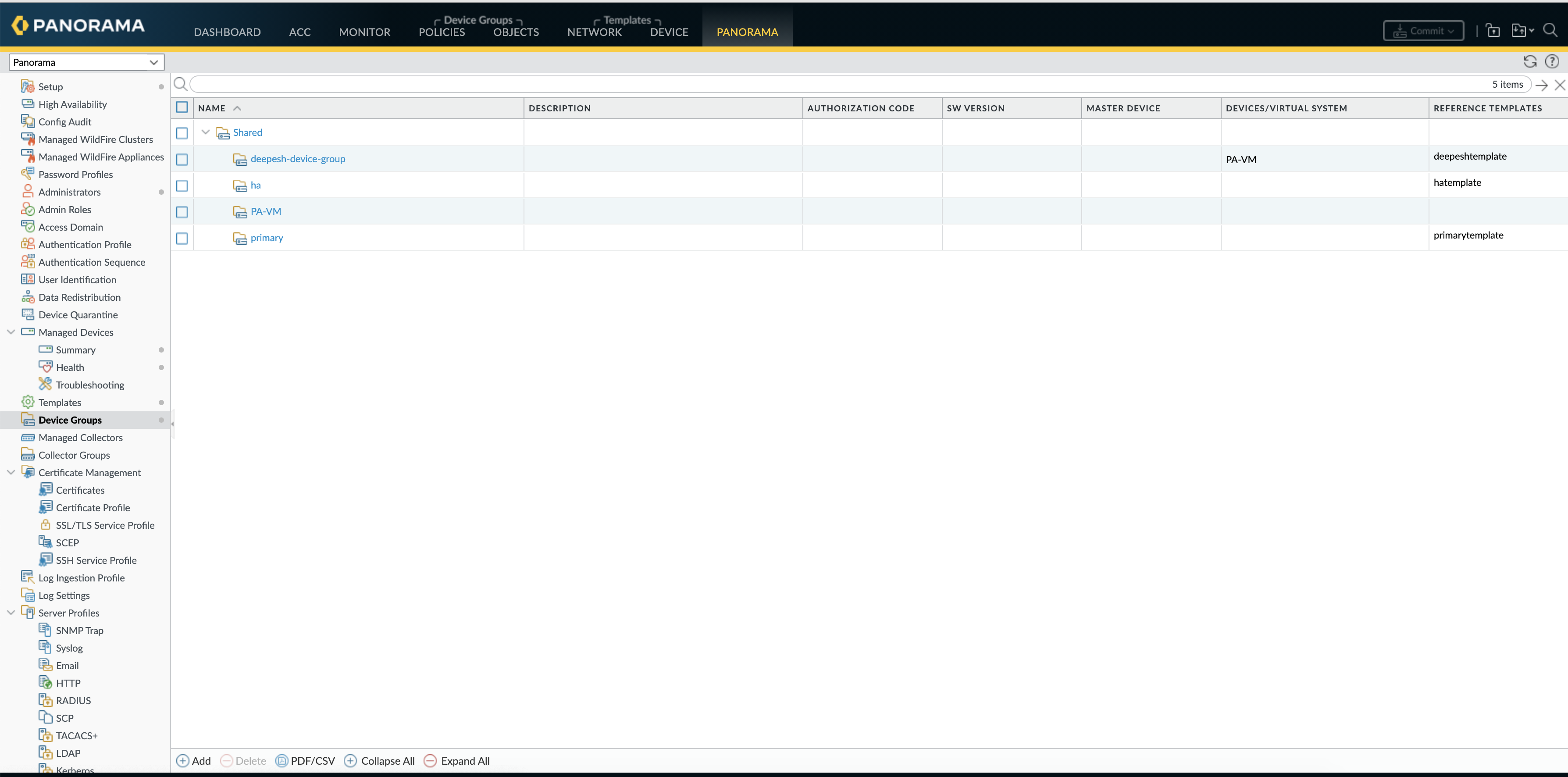
Create Device Group
A Device Group is used to manage all the firewall policies.
Go to Panorama –> Device Groups, click “Add” to create a new device group
Go to Panorama –> Template, select the desired template stack and check the firewall from the device list.
Go to Panorama –> Device Group, select the desired group and check the firewall from the device list.
Commit and push.
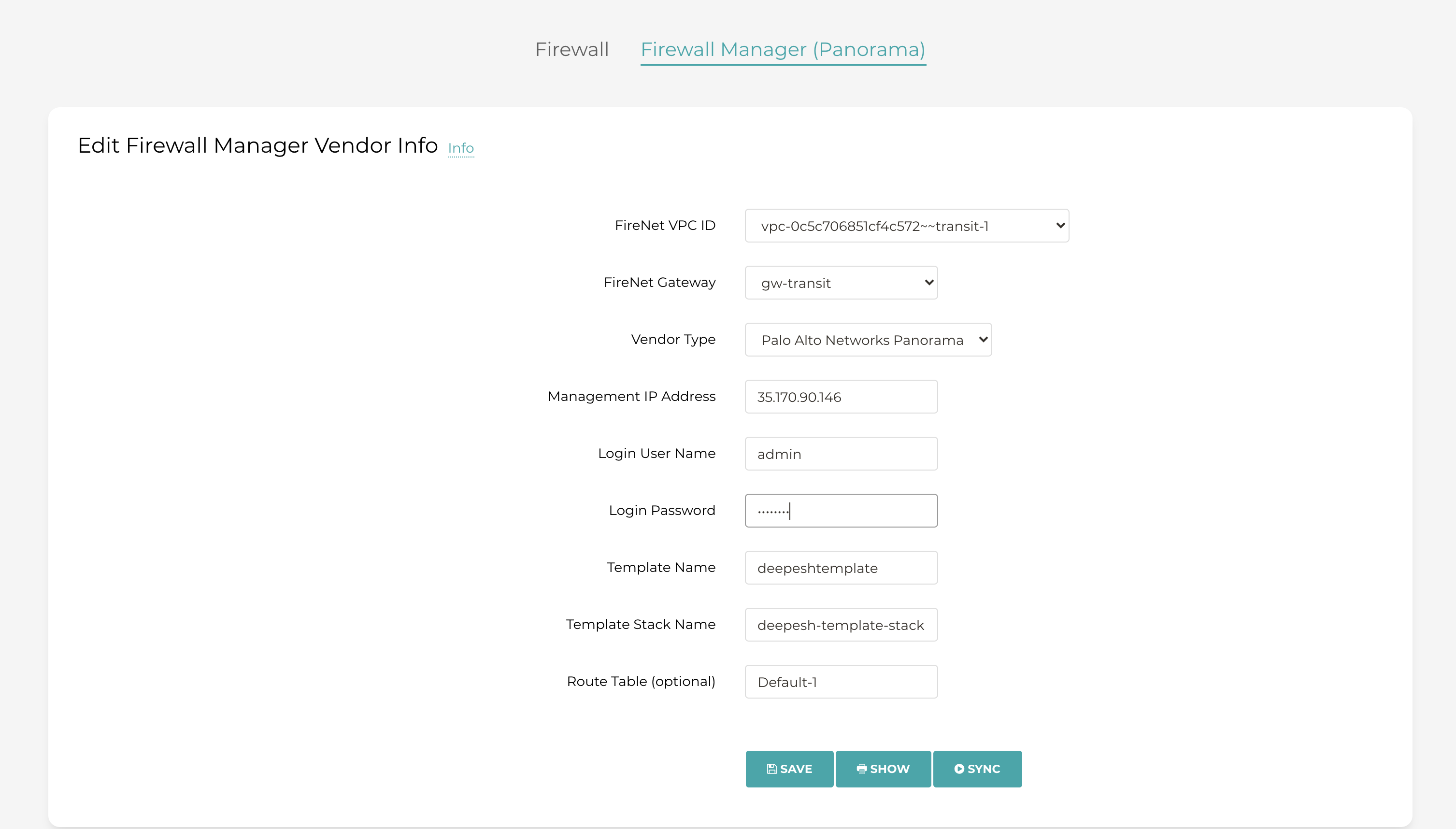
Step7 - Integrate Panorama with Aviatrix Controller
Go to the Aviatrix Controller->Firewall Network->Vendor Integration->Firewall Manager (Panorama), fill out all the required information and save. After this step, the Panorama and PAN firewalls are attached to the controller.
The controller pushes RFC 1918 routes to the template stack, and if the template stack is attached to the FW the same routes will be pushed to the end device as well.
The controller communicates to panorama via API
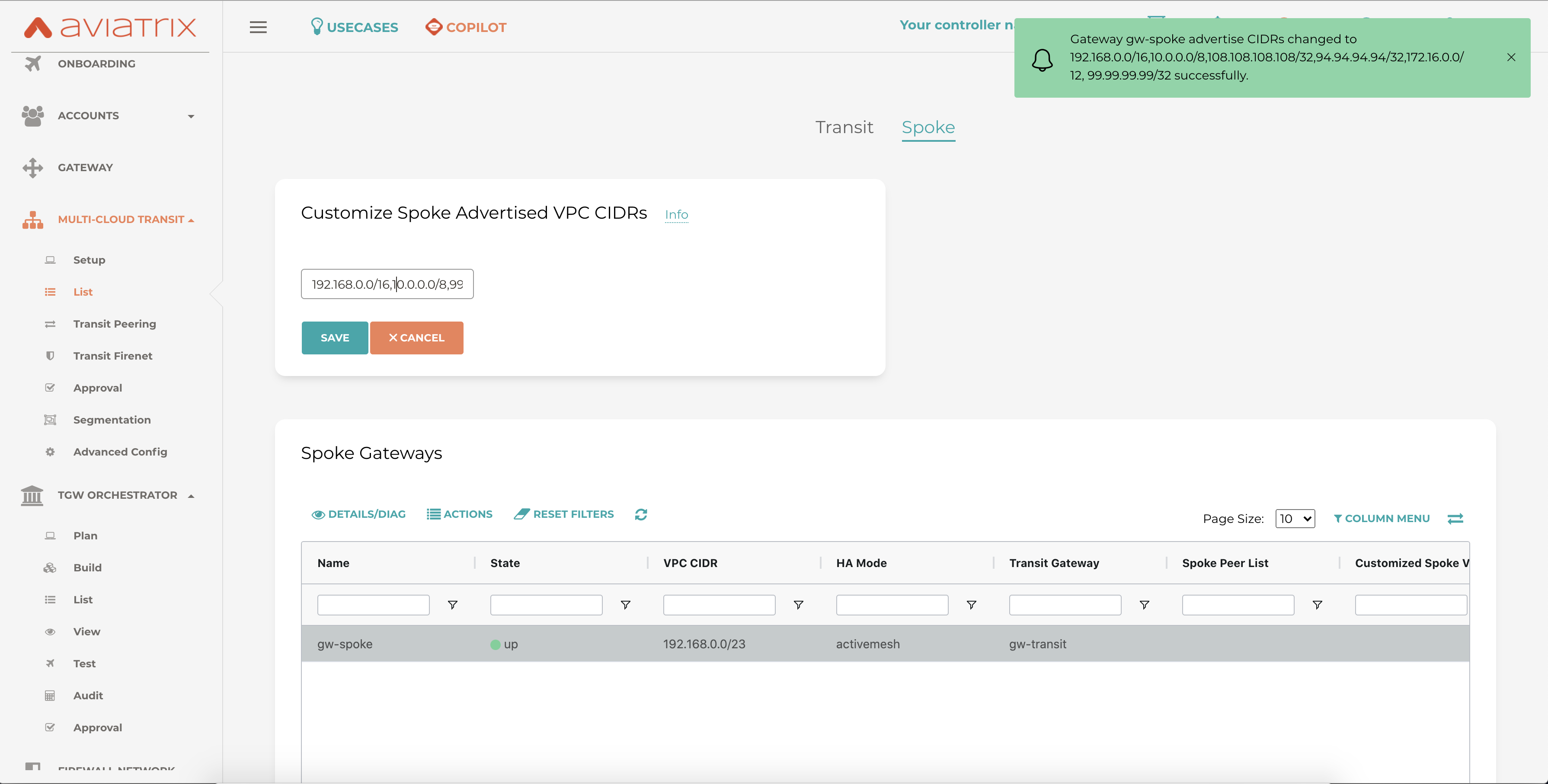
Adding new routes
In a case where new routes/prefixes are learned either from on-prem or from spoke to the transit firenet GW then the controller will automatically push those routes to Panorama and those will be pushed to the end device.
This can be done via controller UI or via Terraform.
Example
In this example, we are advertising custom CIDRs from spoke to transit and want the traffic to be inspected.
To add/edit CIDRs :
Multi-Cloud Transit --> List --> Spoke --> Select the GW ---> Actions --> Custom Advertised CIDR--> Add the CIDR
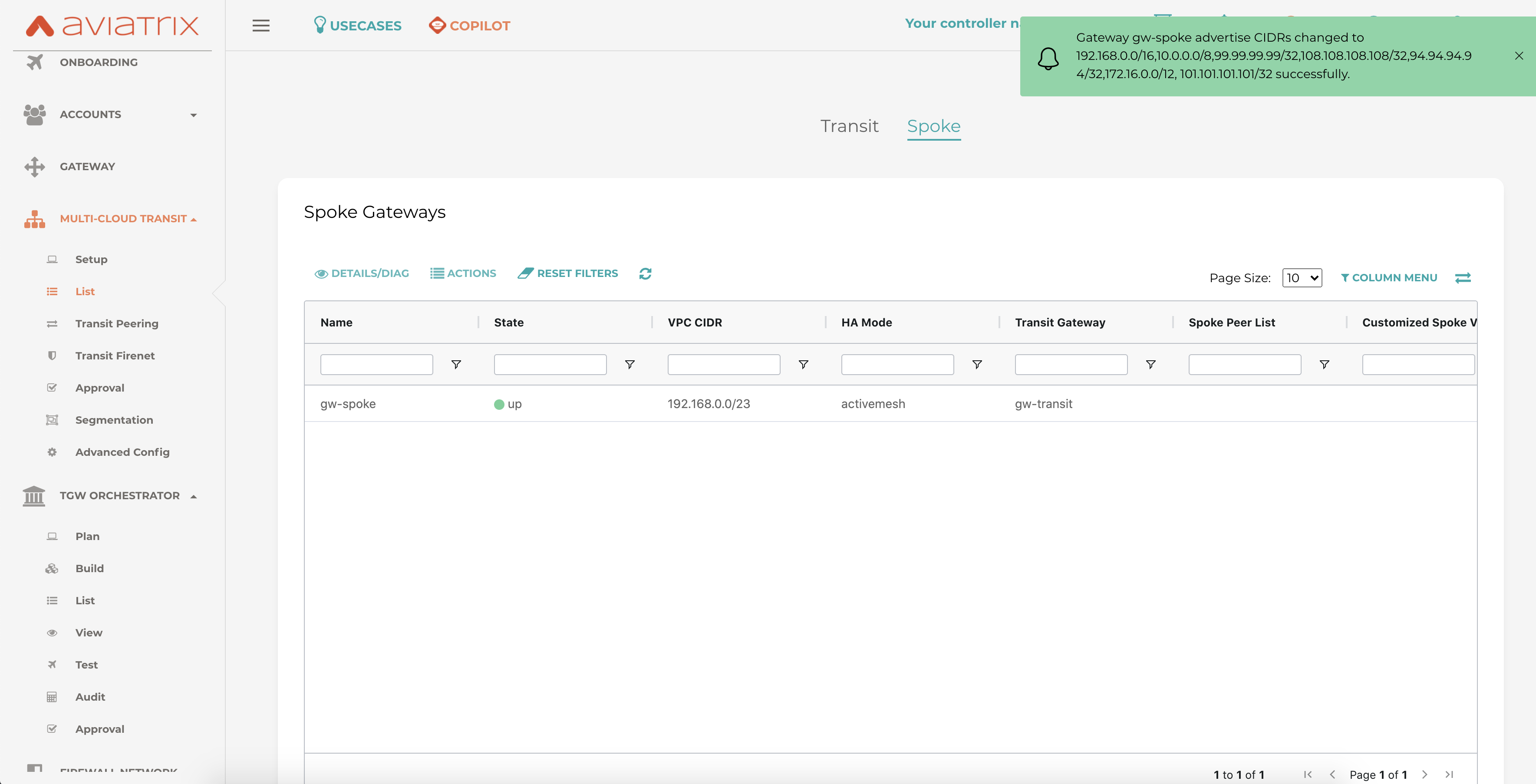
The example below shows the message that pops up on the controller after CIDR has been added successfully
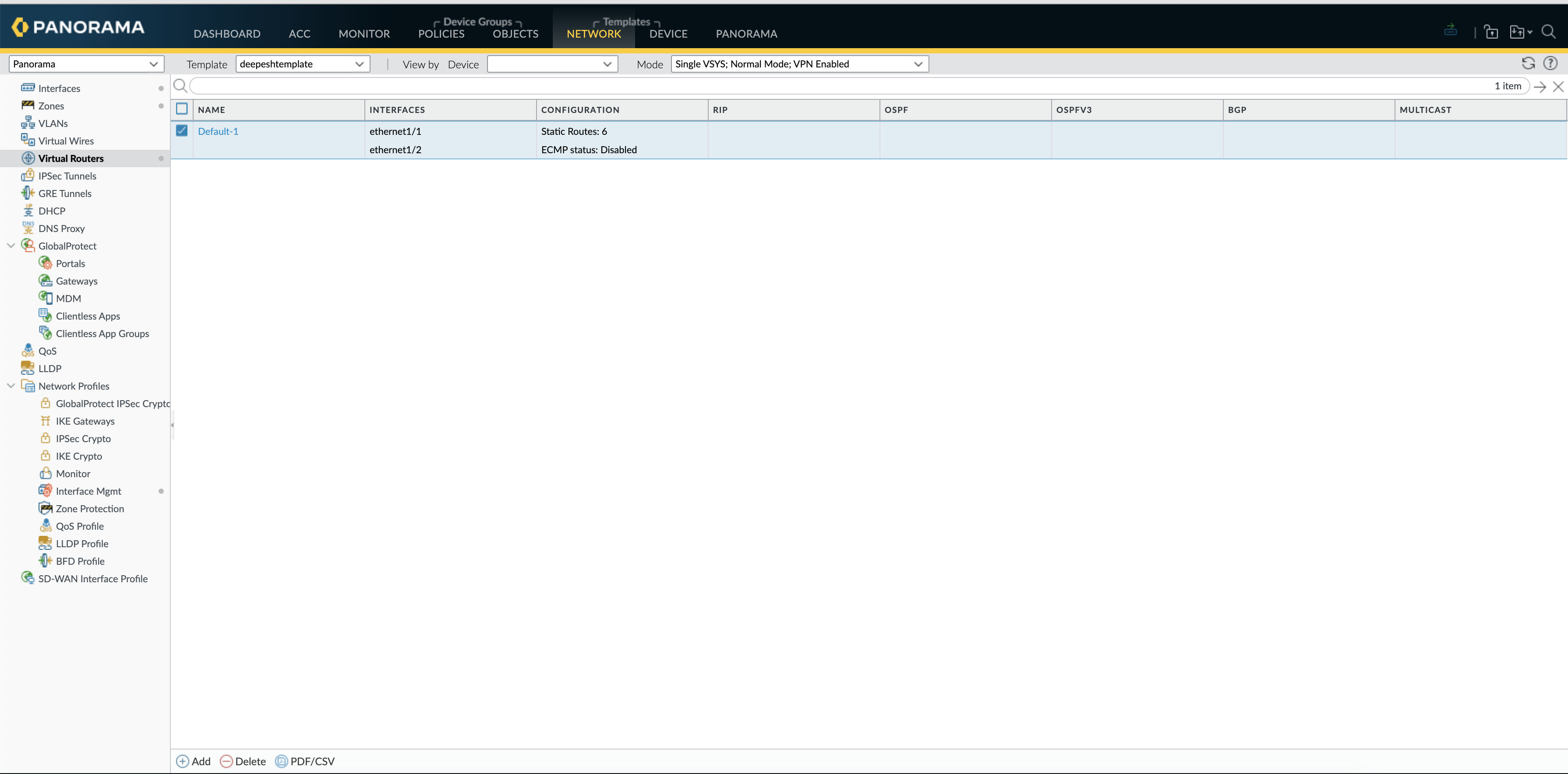
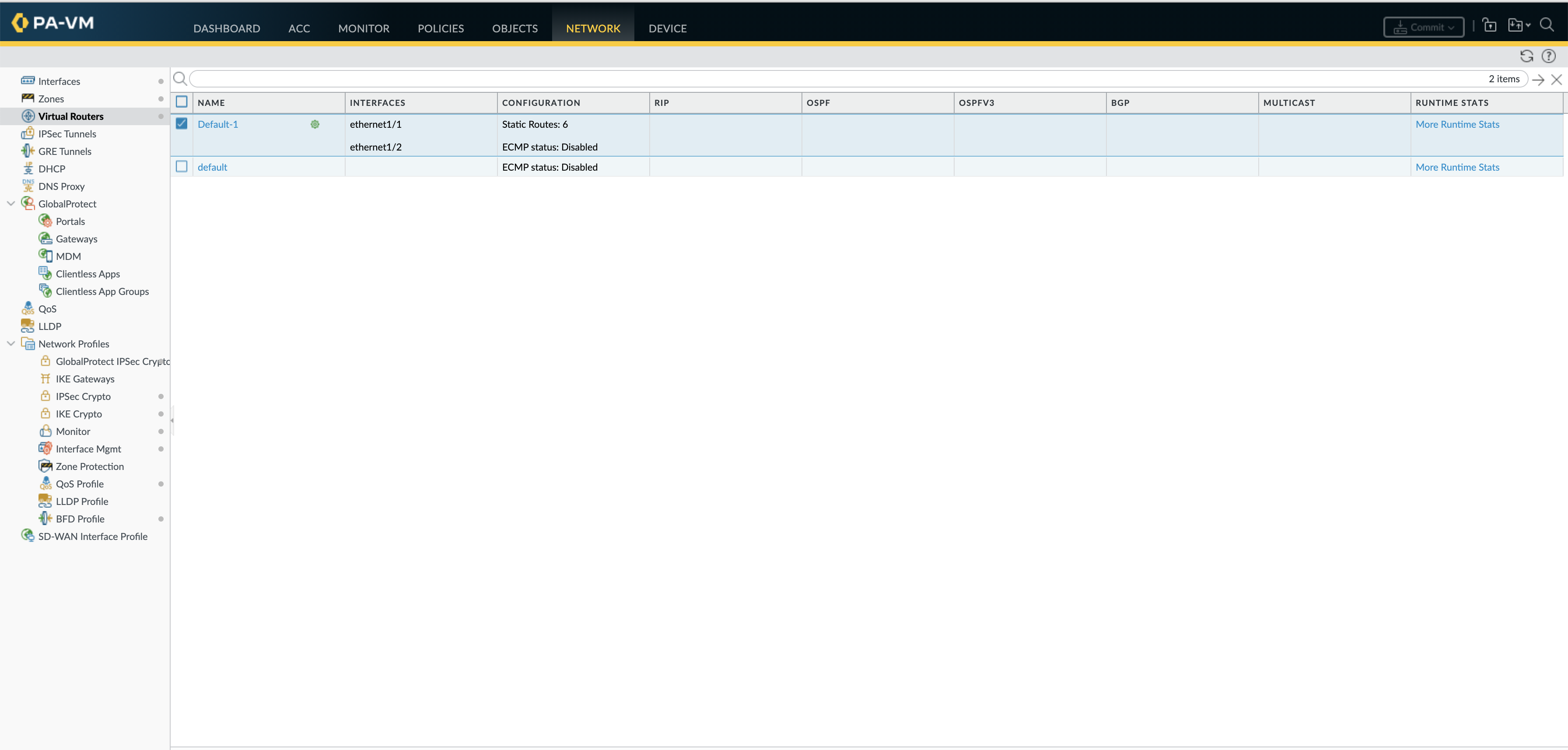
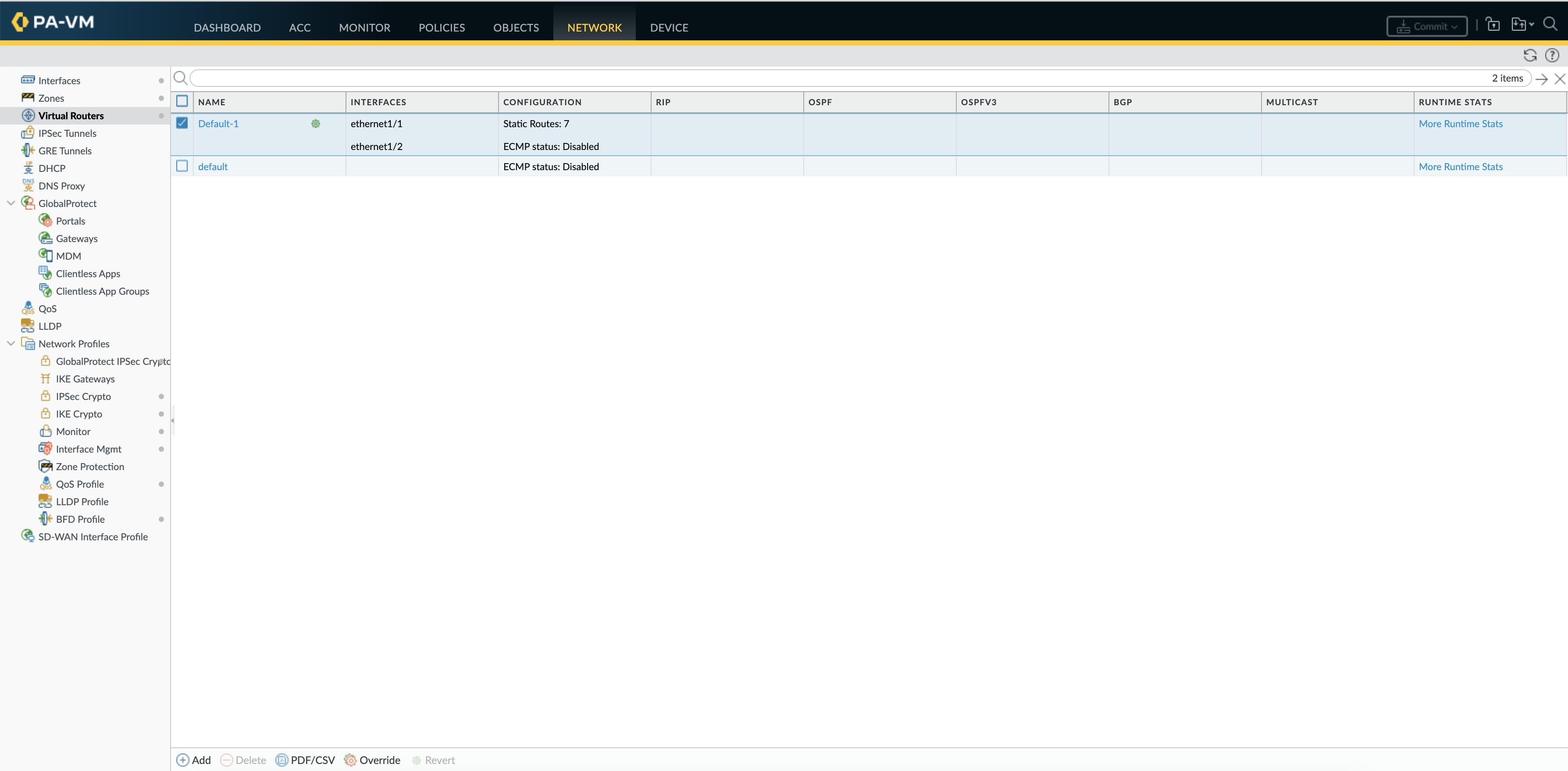
Before new routes were added, as shown in the screenshot below there are 6 static routes in the VR, both on Panorama and the FW.
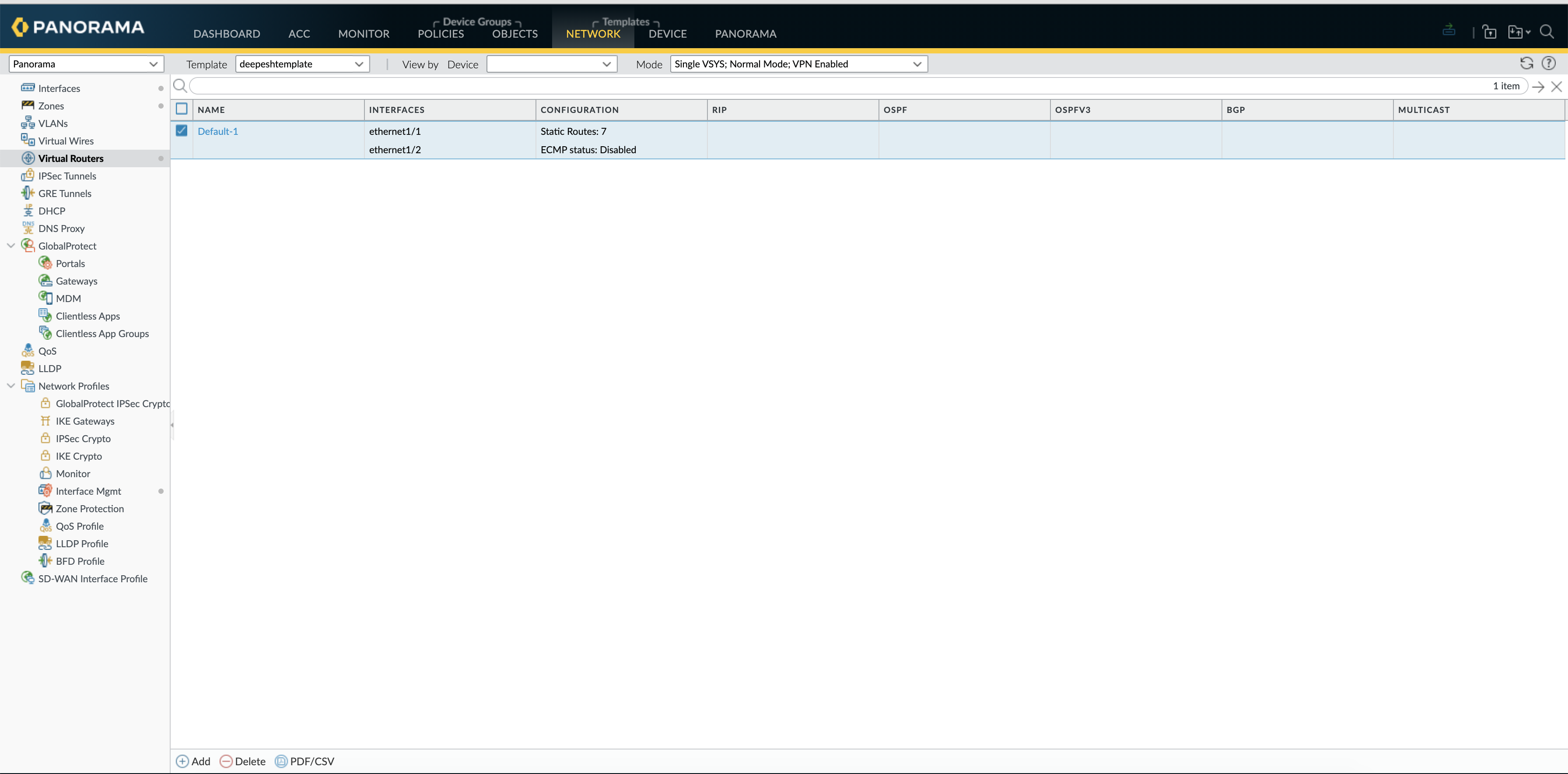
on Panorama:
On FW:
New routes are advertised via Spoke, by adding a new CIDR this can be done under Multi-Cloud Transit --> List --> Spoke --> Select the GW ---> Actions --> Custom Advertised CIDR--> Add the CIDR
As shown in the example below one more prefix is added
The Same is reflected on the Panorama, now the total static routes are 7
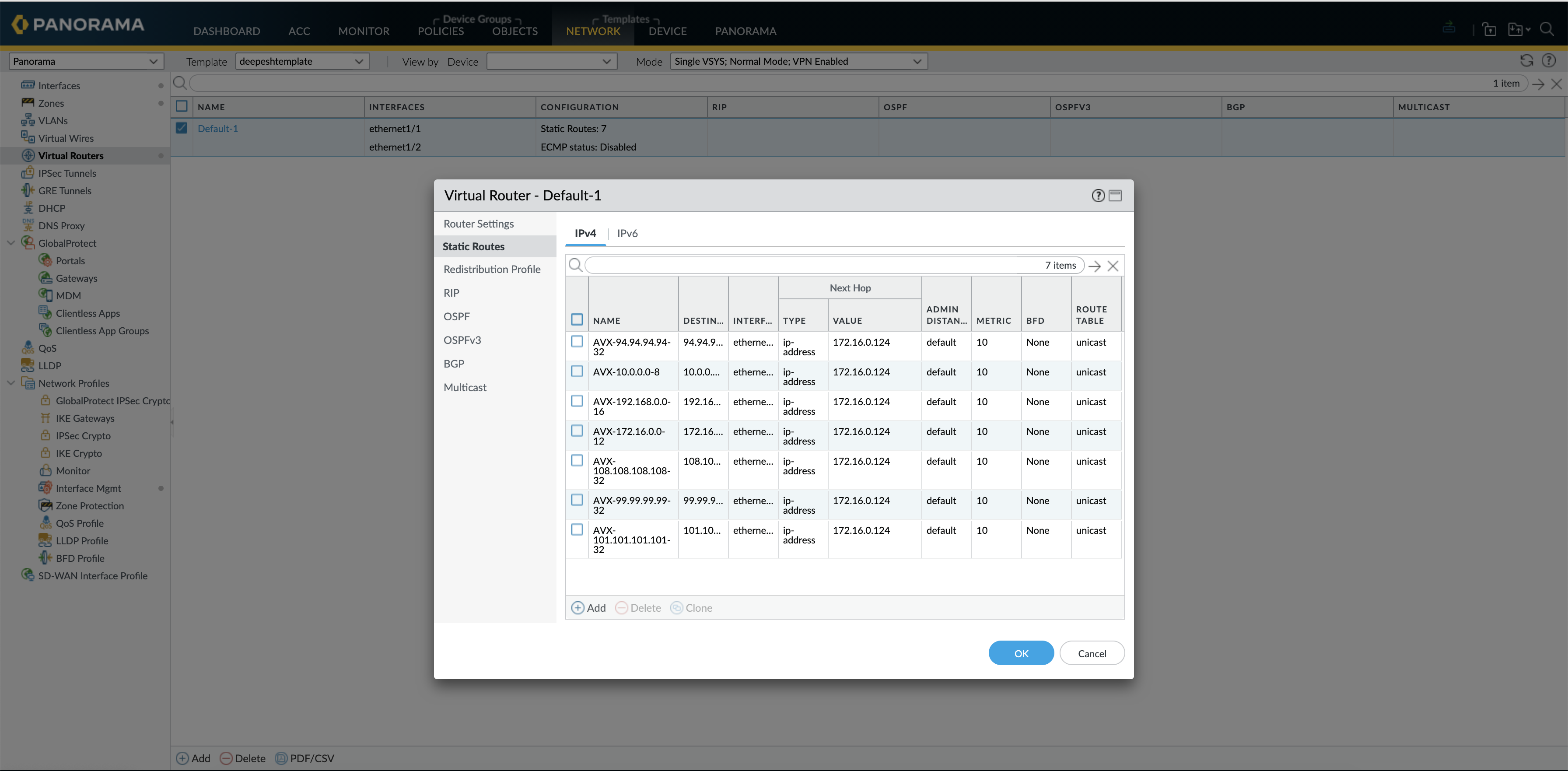
On the FW as well we see a total of 7 static routes
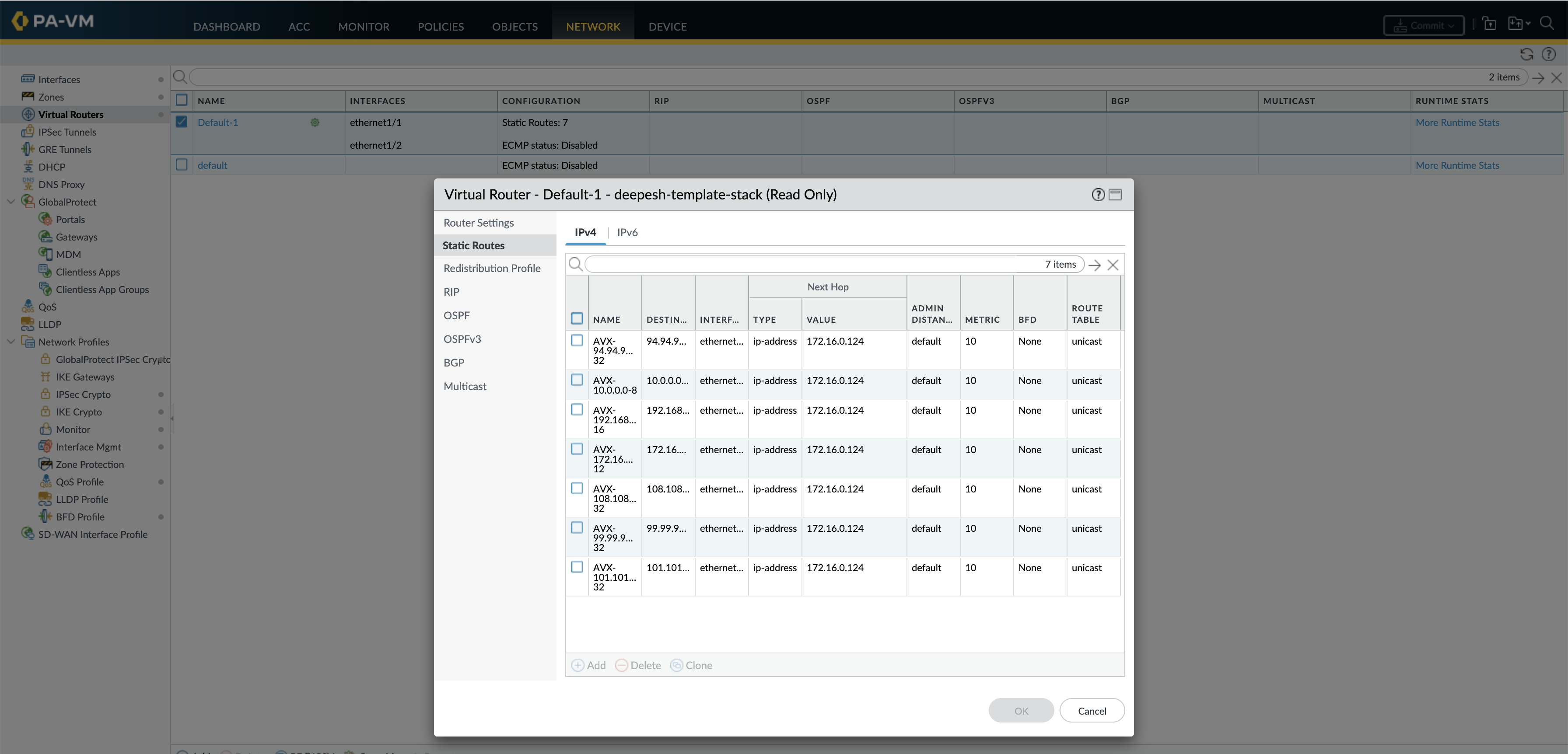
Verification if Routes are getting pushed from Panorama to FW
Under Managed Devices--> Summary --> Policy and Template column it should show as in sync