Introduction
As the workloads and applications grow in the cloud, enterprises have the need to segment the workload based on its type for compliance, regulations, and security reasons.
It is challenging to create segmentation for workload in the cloud. Even if a business is only present in single cloud, there is no policy driven option to create security segmentation provided by the cloud providers. Businesses are forced to use layer 4 stateful firewall constructs such as security groups, network security groups (NSG) or route tables such as static routes or user defined route (UDR) to manually create security boundaries.
For instance, by default, it is not possible to deploy and realize security segments for VPCs that are attached to AWS-TGW. Similarly, in case of Microsoft Azure virtual WAN (vWAN), when VNets are attached, by default it is all or none communication between them.
Aviatrix Policy Driven Multi-Cloud Network Segmentation
Aviatrix has introduced Multi-Cloud Network Segmentation feature with release 6.0 to cater and solve the challenge of segmenting the workload based on the traffic and application profile in policy-driven manner. The policy is intent based that is realized by Aviatrix centralized controller and pushed to distributed data plane (Aviatrix Transit and Spoke Gateways).
These policies directly plug into the robust, global, highly available and active/active, multi-cloud transit. This allows enterprises to realize consistent security postures.
Cloud and On-Prem Agnostic
Aviatrix Multi-Cloud Network Segmentation is cloud agnostic. It is applicable to single cloud as well as repeatable across multiple clouds. Regardless if an enterprise is present in single cloud or multiple clouds (such as Azure, AWS, GCP or OCI), these policies seamlessly works across accounts, subscriptions and projects.
It is also applicable to traffic coming from various on-prem resources such as data center, branches, sd-wan edges or extranets.
Quick and Easy Implementation
The implementation is simple, easy to follow and quick. First step is to create the "Security Segment" using "Aviatrix Security Domain" and then apply "Security Policy" using "Aviatrix Connection Policy" concepts.
Global Security Domain
One can think "Security Domain" as coloring, taging or labeling the workload. This coloring is connection and traffic agnostic. Enterprise can color all sort of workloads such as
- Workload/Traffic in the cloud
- Traffic that is coming from or going towards on-prem locations, such as Data Center, Branches or Partner sites.
- Traffic traversing over peering connections
Following topology shows a large media outlet deployed various types of workloads in AWS VPC. There are Green, Blue and White workloads, while SS represent "Shared Service" VPC.
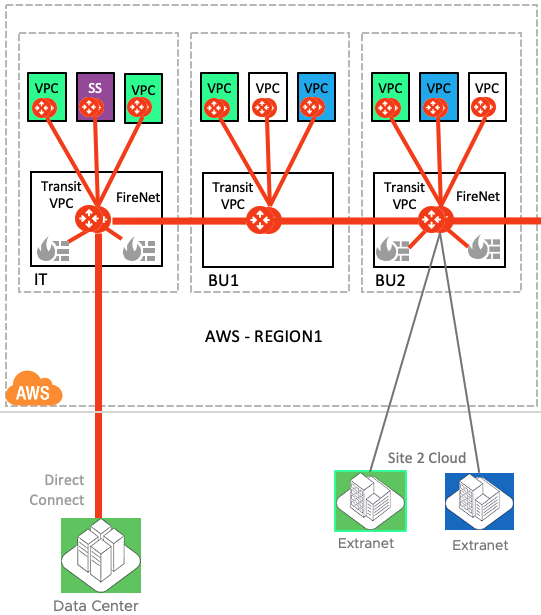
The connection going back to Data Center is part of green traffic while green and blue connections are part of various partners connecting in the cloud but requires access to only their respective VPCs.
Note: There are multiple Aviatrix transits connected in the same AWS Region1. This type of setup is not possible if this enterprise were using AWS-TGW. As AWS-TGW limitation does not allow itself to connect to other AWS-TGWs in the same region.
Global Security Policy
The security policy and segmentation is enforced using the concept of global "Connection Policy". A single UI click or terraform is all one need to realize the security policy. Like security domain, the connection policy is applicable to single cloud, single or multiple regions or multiple clouds / multi-region.
Multi-Cloud Network Segmentation in Action
Following topology shows Multi-Cloud Network Segmentation implementation in a scenario where this enterprise is present in three different clouds, AWS, GCP and Azure.
- Enterprises created Green, Blue and Purple security domains (segments) to tag different types of workloads (could be Prod or Dev workloads for example)
- The Purple color represents the shared service workload
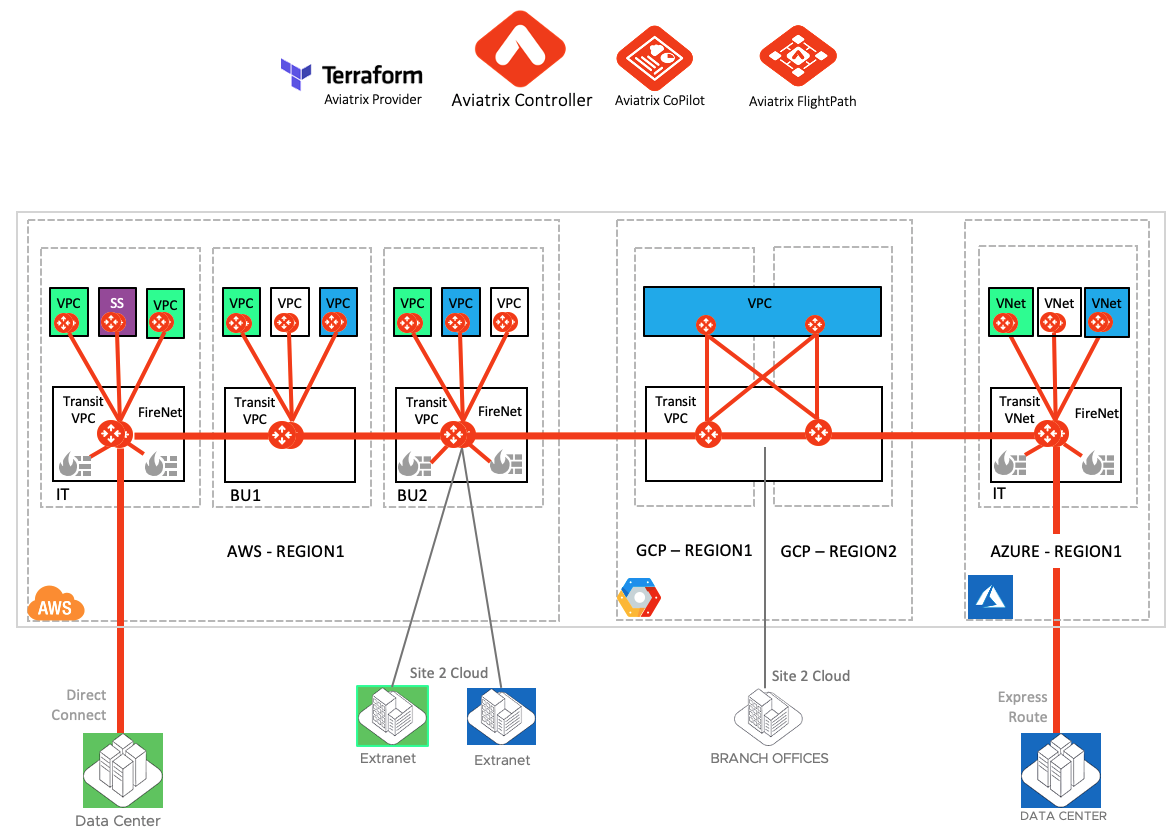
- These colors were then mapped to their respective VPCs, VNets and the on-prem site to cloud connections coming in from direct connect and different partners (extranet).
- The dotted Green and Blue lines show the workload and traffic that is part of Green and Blue segments respectively.
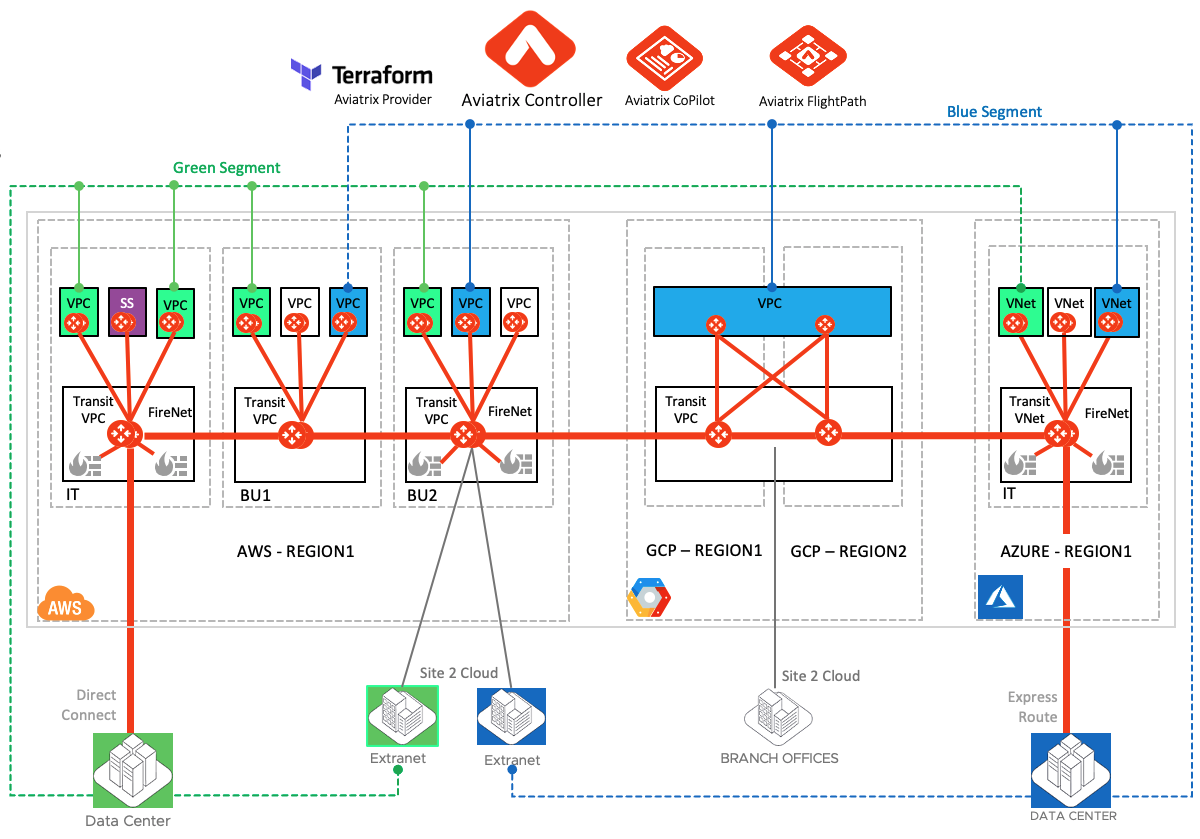
- At this stage the network segmentation planning phase is done.
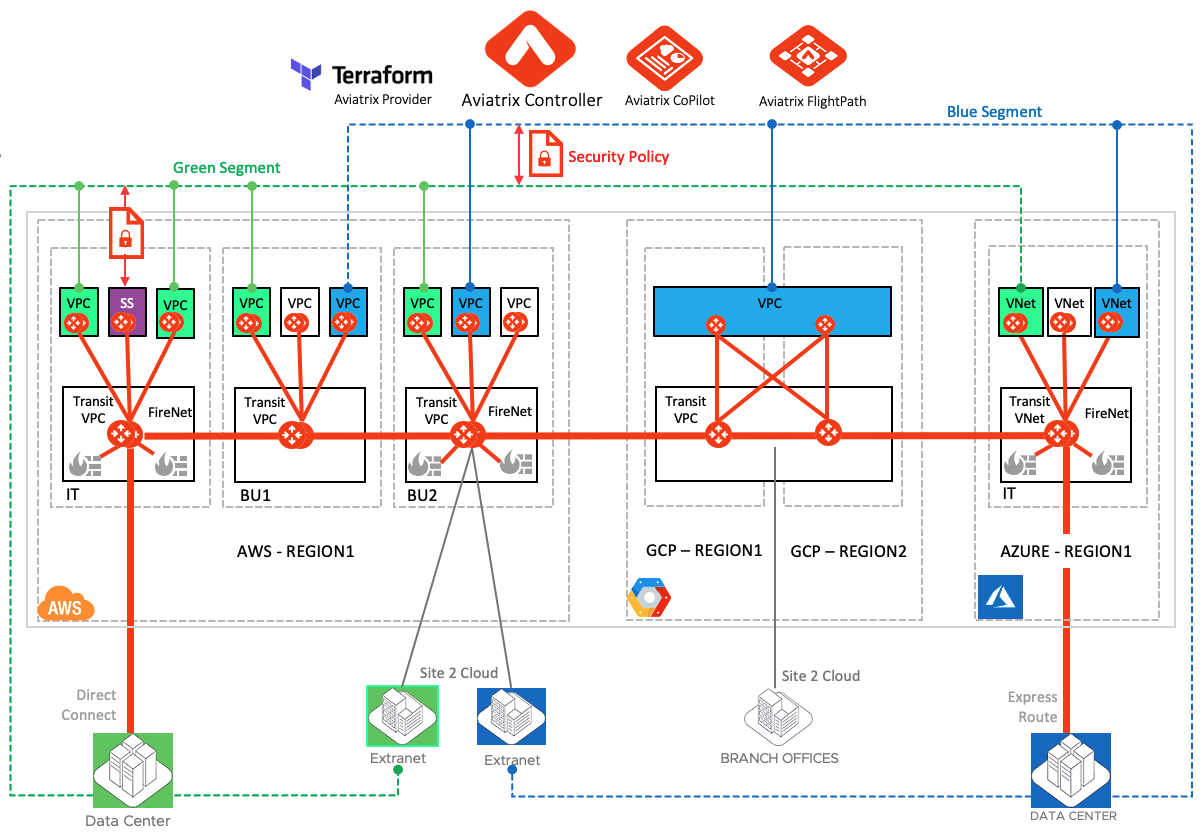
- Following diagram shows the global security policy that is allowed between different color workloads
- In the following example only Green and Blue segments are allowed to communicate with each others
- Green segment is also able to communicate with shared services which is purple colored VPC in our example
- The Green and Blue connections from on-prem are also participating in this segmentation and only allowed to communicate based on the enforced policy
Business Advantages and Conclusion
- Aviatrix Multi-Cloud Network segmentation allows enterprises to plan and protect the traffic within minutes.
- The Aviatrix control plane realizes the intent across clouds while overcoming the limitations and shortcoming of cloud native constructs
- It also allows more secure application posture by letting enterprises begin with a zero-trust model and then allow the necessary traffic segments to communicate
- The implementation and design is flexible and can cater various scenarios based on enterprise needs
- Entire interaction, configuration and deployment is automated (API/Terraform supported, read to be plugged into your CI/CD pipeline), backed by powerful centralized control and distributed data plane
Call to Action
For a 30 min demo, or if you have further technical questions, email info@aviatrix.com


