Many customers learned about Aviatrix when they wanted an easy solution to Egress filtering. This article shows how Aviatrix makes it easy to perform Egress filtering on your public instances.
Introducing Aviatrix Public Subnet Filtering with Fully Qualified Domain Name (FQDN) Gateway, which can be used for Egress filtering as well.
In this article, a “virtual cloud” refers to VPCs/VCNs/VNets.
What does the Aviatrix FQDN feature do?
Aviatrix Fully Qualified Domain Name (FQDN) is a security service specifically designed for workloads or applications in the public cloud. It filters Internet bound egress traffic initiated from workloads in a virtual cloud.
Aviatrix FQDN filters any TCP and UDP traffic including HTTP, HTTPS and SFTP traffic. The filtering function allows the destination host names to be whitelisted or blacklisted.
For HTTP/HTTPS (TCP port 80/443), FQDN feature also supports wild cards, such as *. For example, you can specify *.salesforce.com to allow traffic to any domain names that ends in “salesforce.com”.
Each destination is specified as fully qualified domain name. For example, if you only allow Internet bound traffic to www.google.com, you can list the domain name www.google.com in the whitelist.
You can also allow/deny specific subdomains only. For example, you can say that *images.google.com is blocked while *google.com is allowed.
How does it work?
The function is transparent to individual instances and is carried out inline without requiring any certificate or keys to decrypt the traffic.
Non-HTTP/HTTPS traffic can also be filtered based on exact domain names. Use cases are secure file transfer (SFTP) to external sites, secure login in (SSH) to external sites.
What is a Public Subnet Filtering Gateway?
Public Subnet Filtering gateway (PSF/Egress FQDN gateway), provides Egress security to public subnets where instances have public IP addresses. This is applicable for all major cloud service providers (CSPs).
A PSF Gateway is deployed within the local virtual cloud (VPC/VNet/VCN). It is not deployed at the transit layer. For this reason, this filtering mechanism is also called Local Egress Filtering. (Note: In contrast, Centralized Egress Filtering is done at the transit layer, and that is for private subnets only.)
The following two diagrams show that PSF Gateways (Egress FQDN) are deployed locally. One architecture has the transit layer and the other does not have a transit layer, but the PSF Gateway is never part of the transit layer.
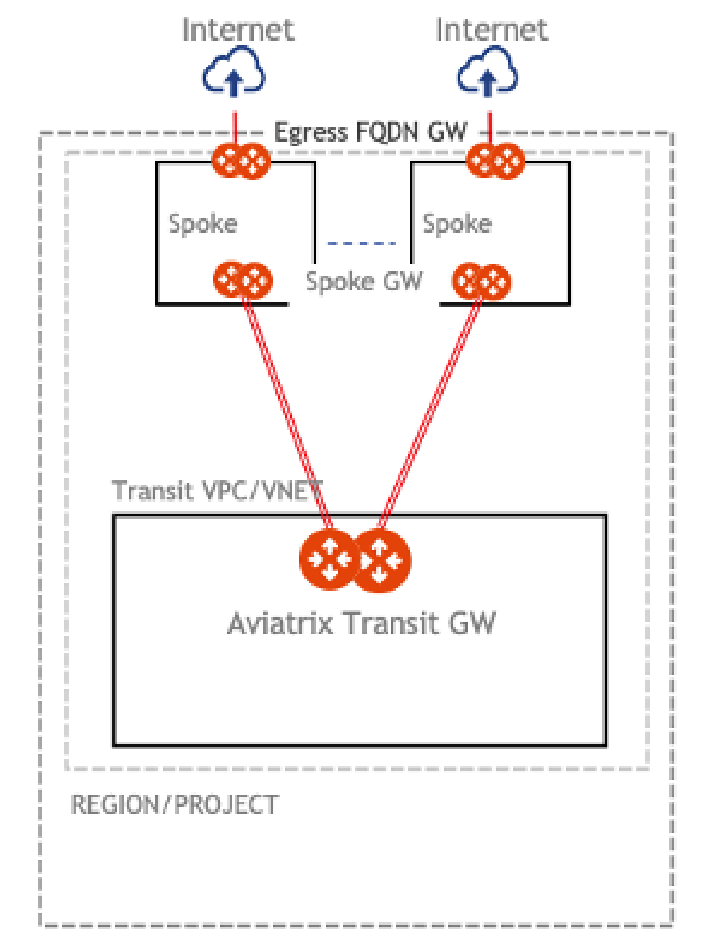
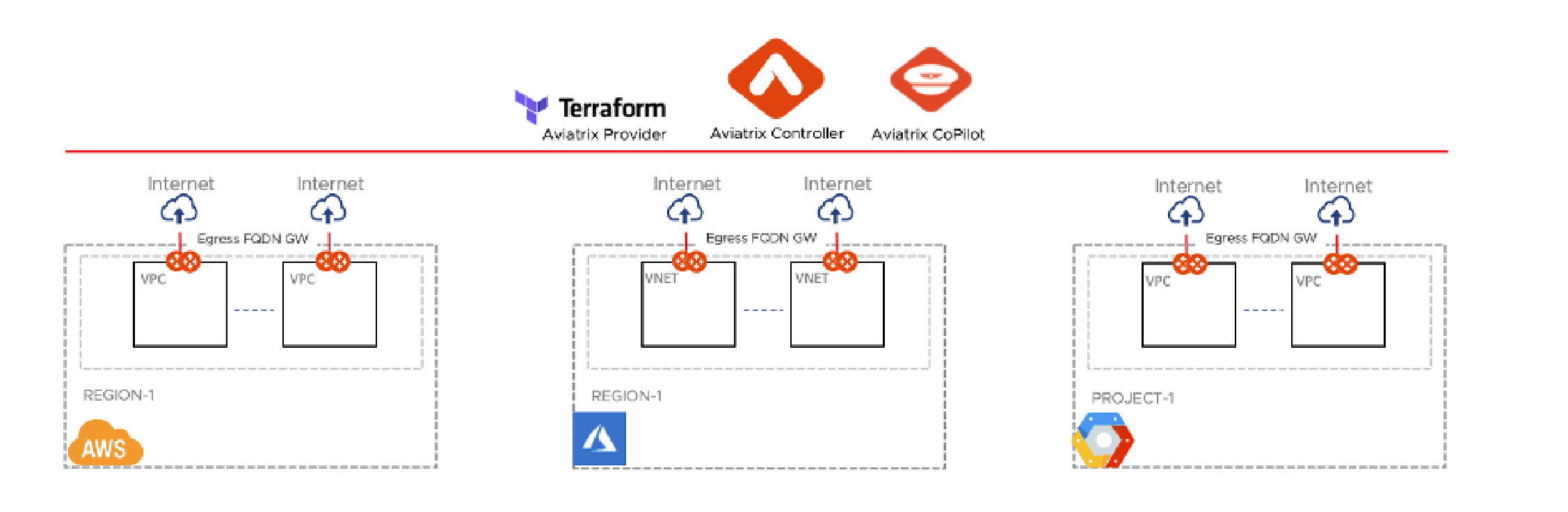
Deploying a PSF Gateway for Local Egress Filtering
In Aviatrix Controller, deploying a PSF Gateway is easy.
One simply heads to Security > Public Subnet and adds a new gateway by filling out the simple form. And done!
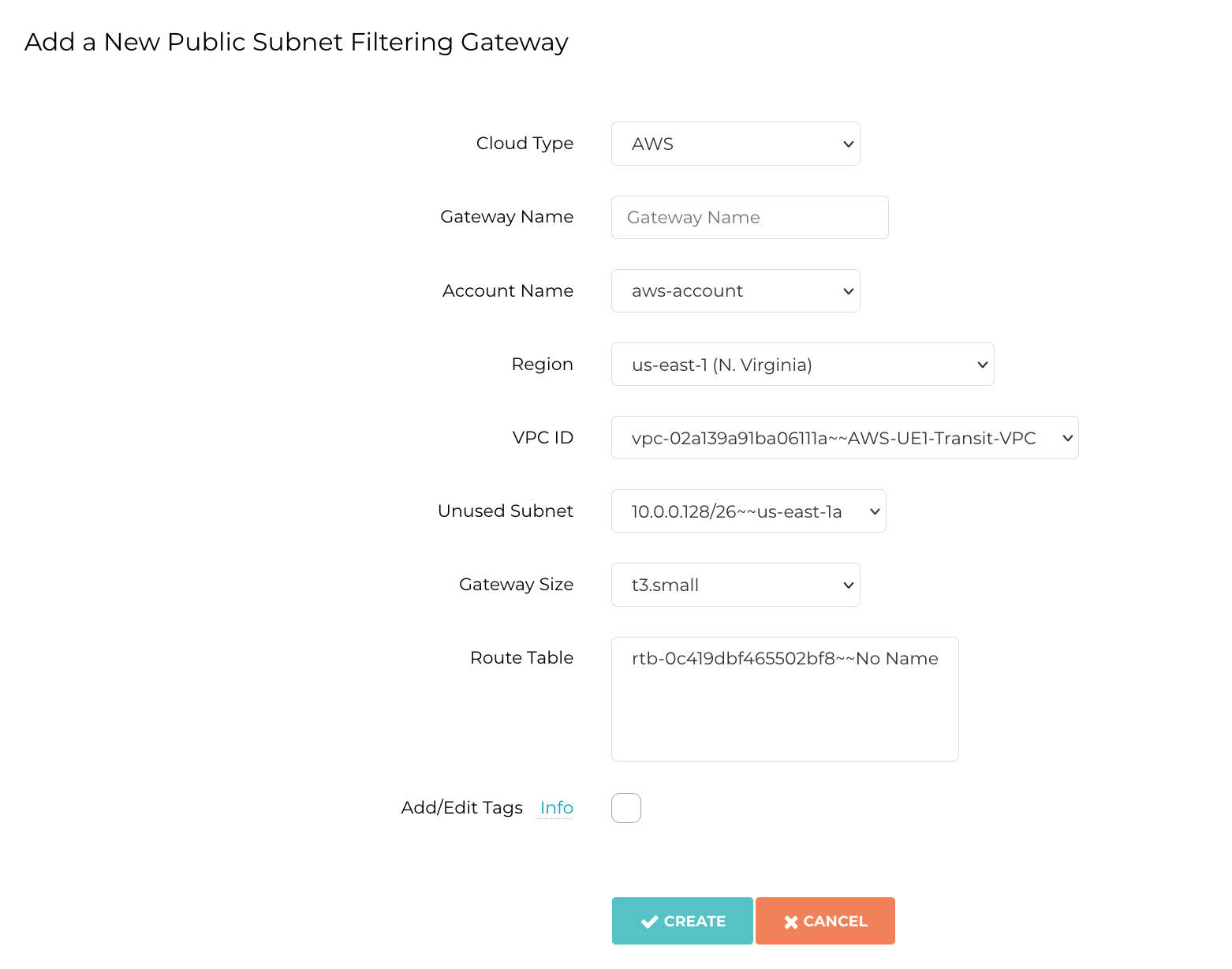
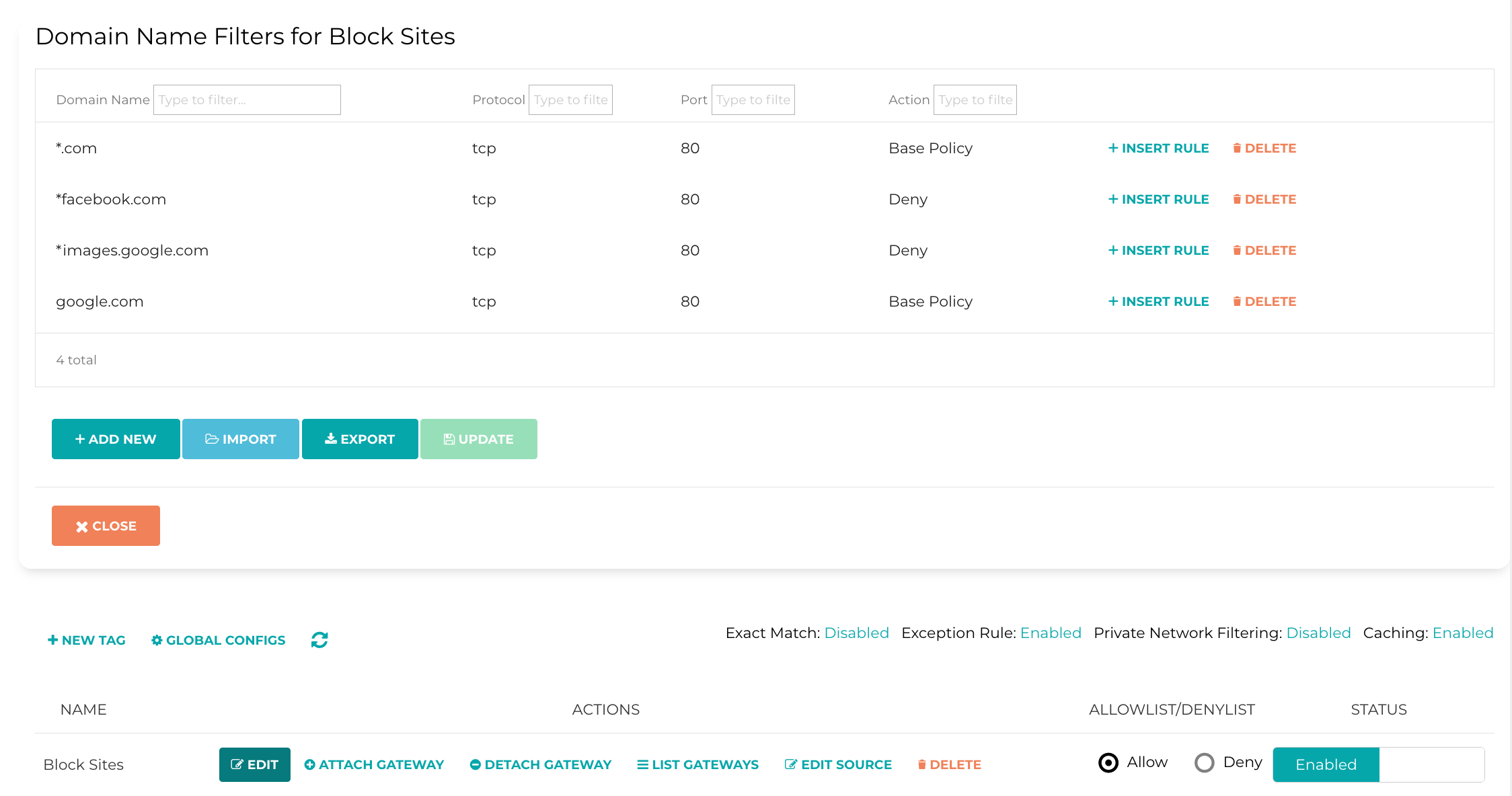
Egress Filtering
Aviatrix makes it so easy to apply Egress filtering rules on your FQDN gateways.
- You can do this by going to Security > Egress Control > Step 3: Egress FQDN Filter.
- Click "New Tag" and provide a name of your filter.
- Click "Edit" and then add your domain names by clicking "Add New" with the action. The ordering of rules is important. Then hit "Update" and then "Close" to close the pop-up.
- Click “Attach Gateway" to the tag filter where you will select your PSF Gateway (see Deploying a PSF Gateway for Local Egress Filtering above).
- Select the appropriate option in AllowList/DenyList column. This will be the Base Policy.
- Toggle to "Enabled" in Status column to enable the filter.
Looking Forward
If you are flabbergasted how this can be so easy, believe me it is very easy! If you have a more advanced use case with NGFW or AWS TGW and require Egress filtering, then contact us to find out how we can integrate Aviatrix to your needs.
Schedule with us a demo: http://www.aviatrix.com/schedule-demo
