Introduction
For Aviatrix controller login, we can use SAML authentication methods to various available IdPs, in addition to using simple username & password . IdP is basically any provider that supports SAML end point (AWS SSO, Azure AD, PingOne, Okta, OneLogin , Google etc). By leveraging these integrations we can use single sign on by one or many IdPs. Your aviatrix controller acts as the Identity service provider that redirects application traffic from client to IdP (example AWS SSO) for authentication.
In this blog we will focus on AWS SSO IdP integration for Aviatrix controller.
Pre-Requisites
- Already deployed Aviatrix Controller Controller Startup Guide
- AWS account with administration access (consolidated AWS account cannot set up SSO unless all child accounts enable full feature permissions)
Configuration
Step 1
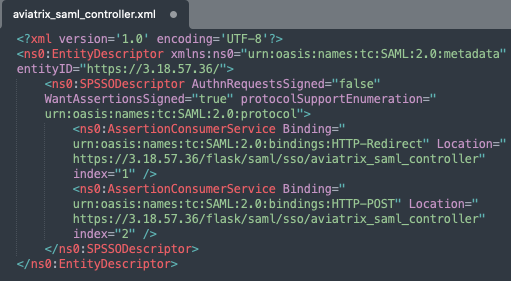
Login to your Aviatrix controller and Create a temporary Aviatrix SP Endpoint.
Check below screenshot from controller endpoint and SP METADATA file for reference. Retrieve your SP METADATA file on your local machine.
NOTE:- For this example we used Controller Login SAML Config integration with AWS SSO.

Step 2
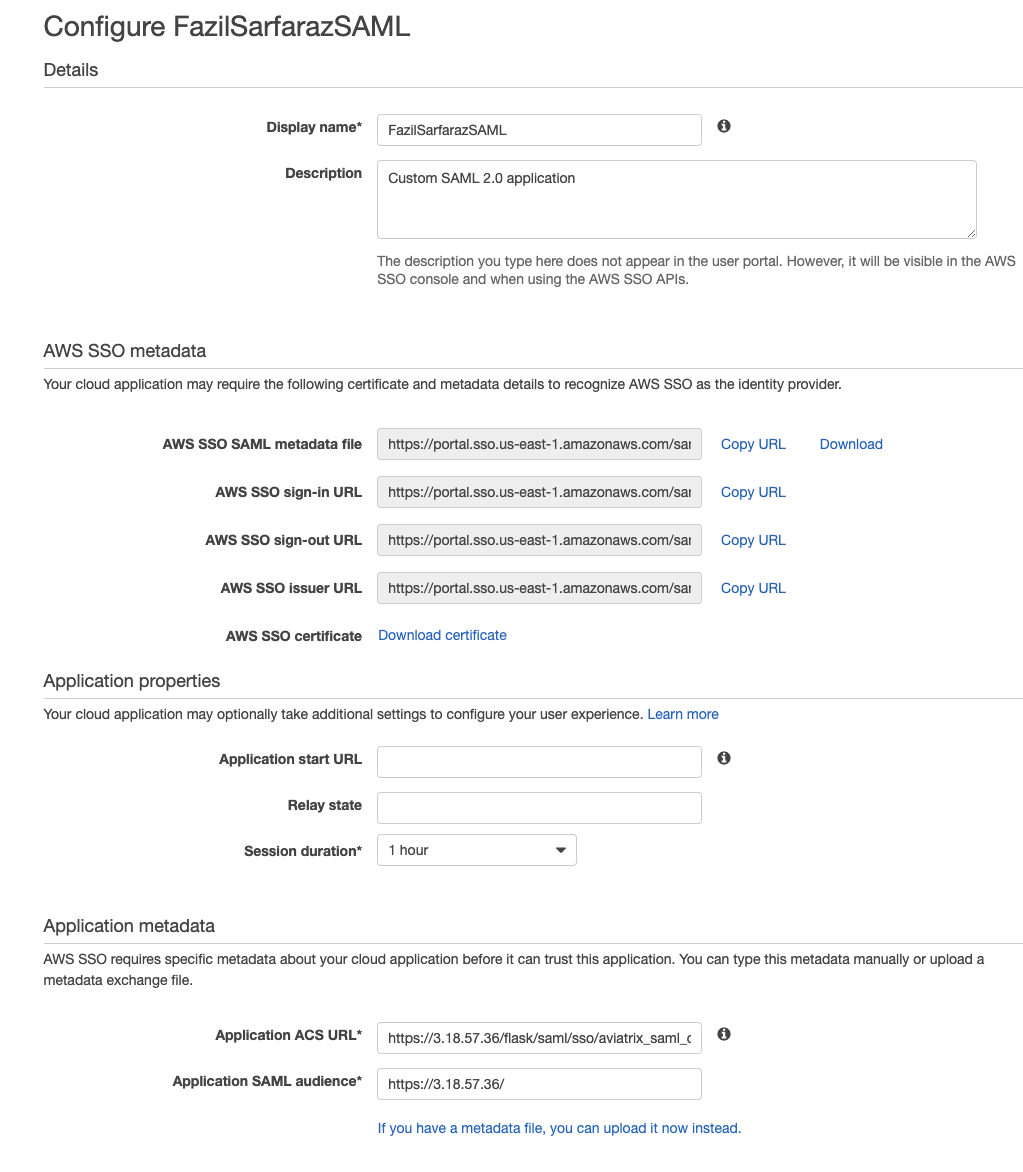
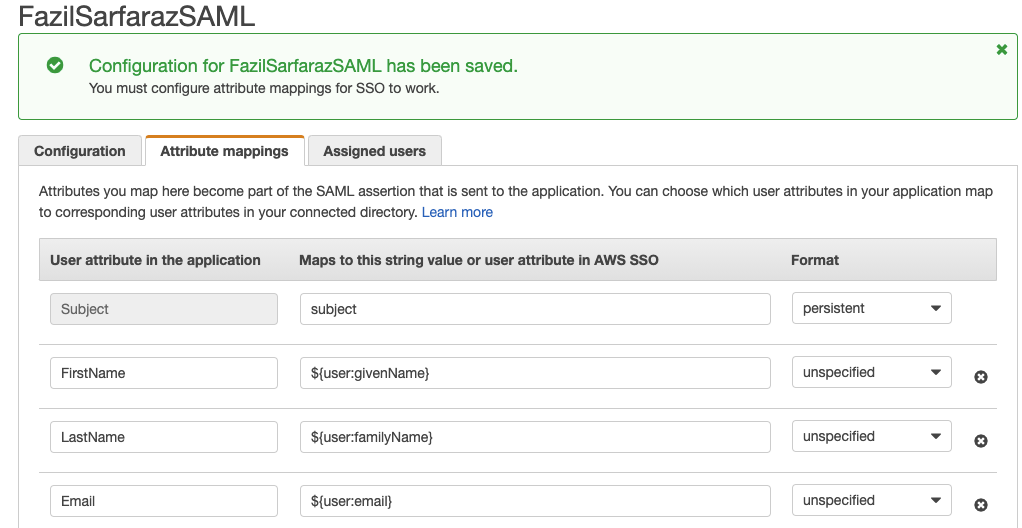
Now enable AWS SSO SAML Application via AWS console as discussed here.
Please note that you need admin access and cannot use consolidated AWS account. Below are screenshots from AWS console as reference.
Step 3
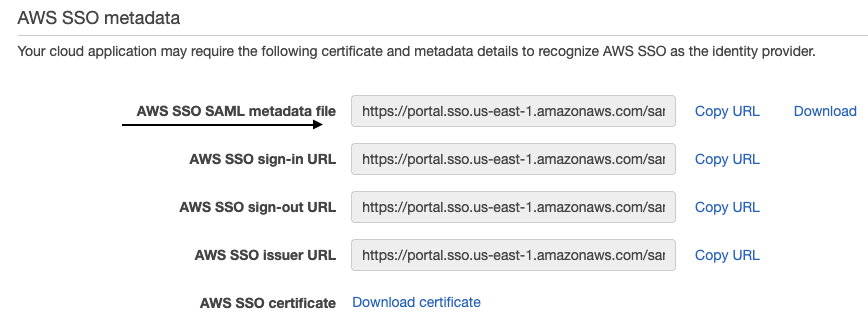
Retrieve AWS SSO IdP metadata as discussed here.
Below is screenshot from AWS console as a reference. The metadata URL shown by an arrow will be used to recognize AWS SSO as IdP.
Step 4
Upgrade the temporary Aviatrix SP Endpoint created in Step 1 with AWS SSO SAML metadata details as discussed here.
Screenshot from controller as reference.
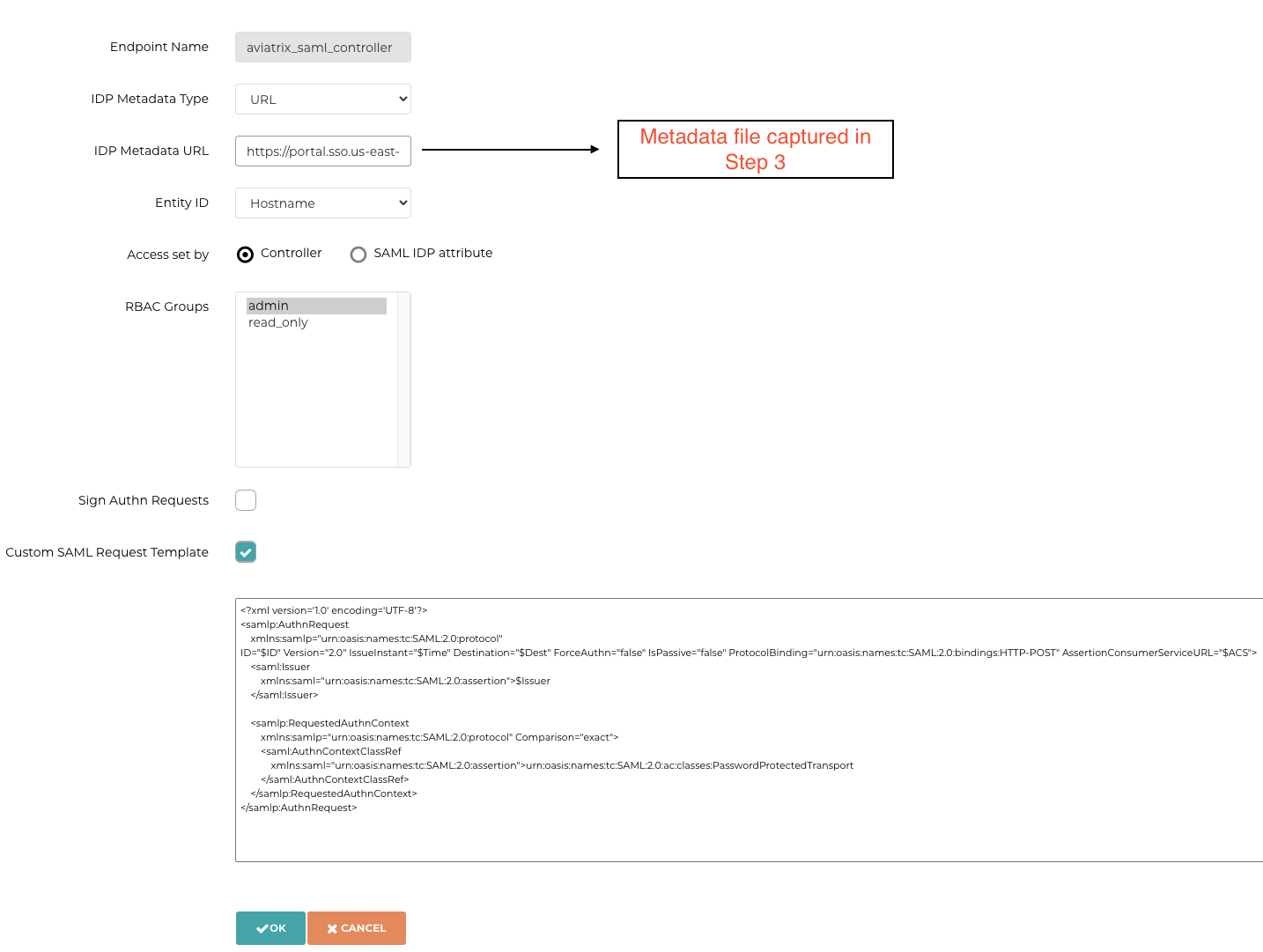
Step 5
Test the integration from controller SAML endpoint test button as discussed here.
It should redirect you to AWS sign in page and subsequently login to the controller automatically.

Validation
Finally you should now get 2 options to login to controller (Sign in OR SAML login) as shown below.

If you now click SAML login you will automatically login to controller as a AWS SSO user


