Problem Statment
More and more Enterprises, Vendors, and SaaS providers are hosting applications in AWS using its Private Link service. Private Link allows connecting to those applications using the private RFC1928 IP ranges instead of accessing them over the public Internet. This has created a sprawl of Private Link services across the Cloud deployment. There is a need to provide centralized access to those Private Link services with the troubleshooting, next-generation firewalling, and have the visibility required for traffic going towards these applications sitting behind the Private Link.
This article discusses a scenario where the on-prem data center and branches are accessing the centralized Private Link services.
Topology
The diagram shows a simplified connectivity model, where the on-prem device (subnet 192.168.40.0/24) is connecting to the consumer spoke VPC via the Aviatrix Transit. The consumer spoke VPC is configured with subnet 10.0.0.0/16.
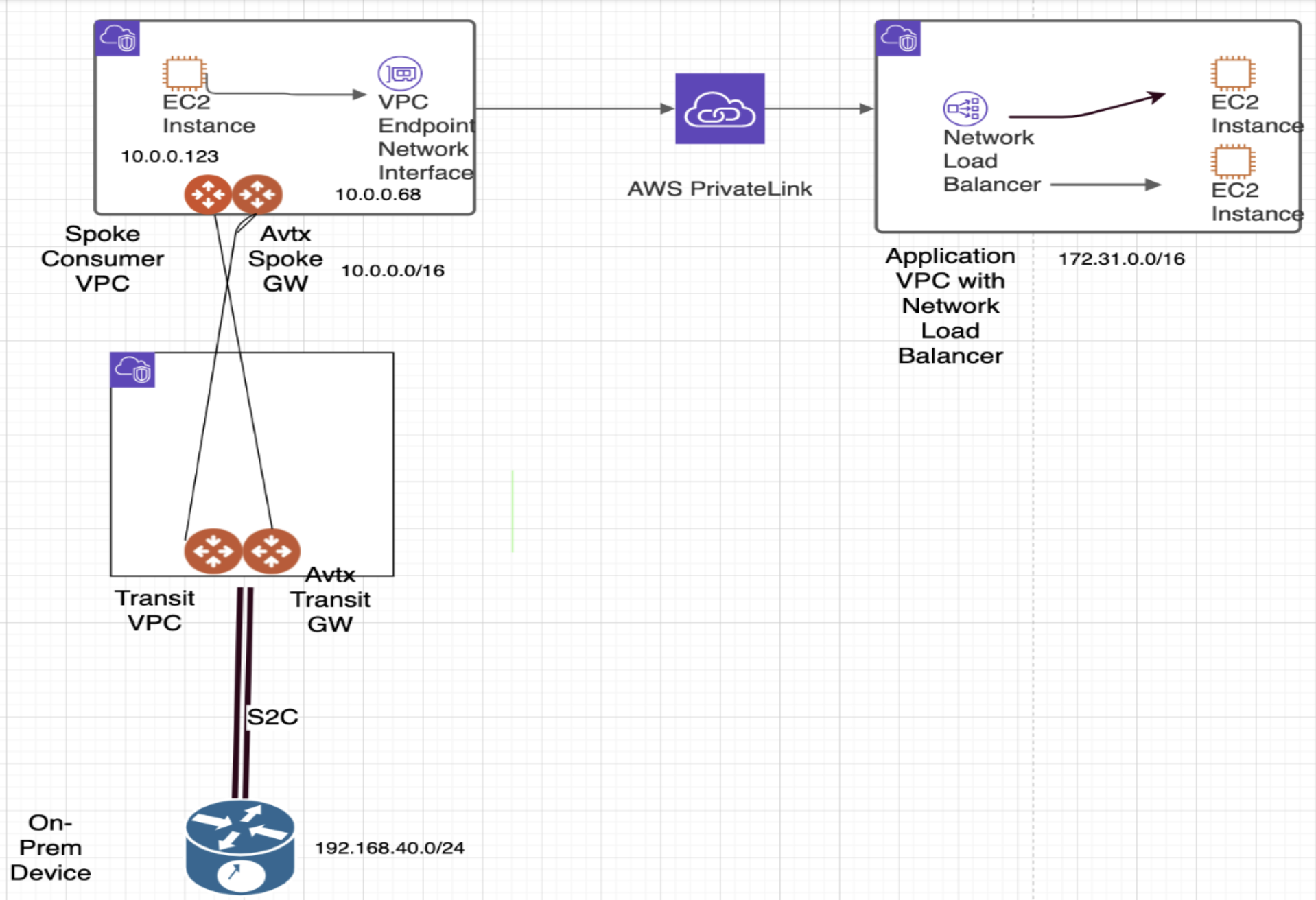
The private interface endpoint has an IP address 10.0.0.68 which will be connecting to the application VPC via the AWS PrivateLink.
Assumption
It is assumed that the customers understand AWS PrivateLink. Please refer to this link https://d1.awsstatic.com/whitepapers/aws-privatelink.pdf for more details.
Configuration
- First, create VPC "Endpoint Service" inside the "Application VPC". This "End-Point Service" will point to the Network Load Balancer (NLB). The NLB itself is created in the "Application VPC". This NLB has the target to the application as shown in the diagram above
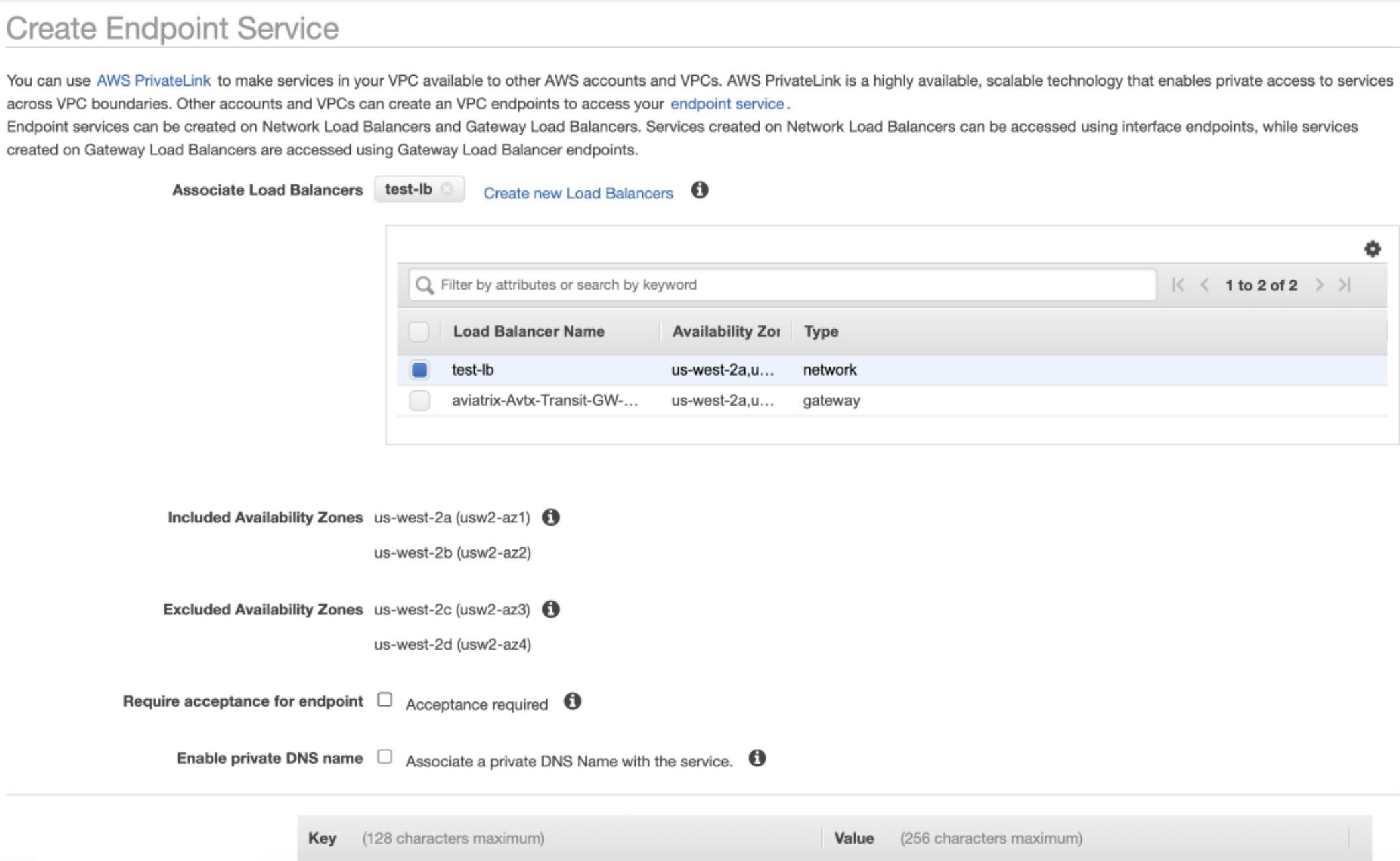
-
The second step is to create the "Interface Endpoint" inside the "Consumer VPC". This interface endpoint will point towards the "Endpoint Service" which is sitting in the application VPC and exposed via the NLB we created in the first step.
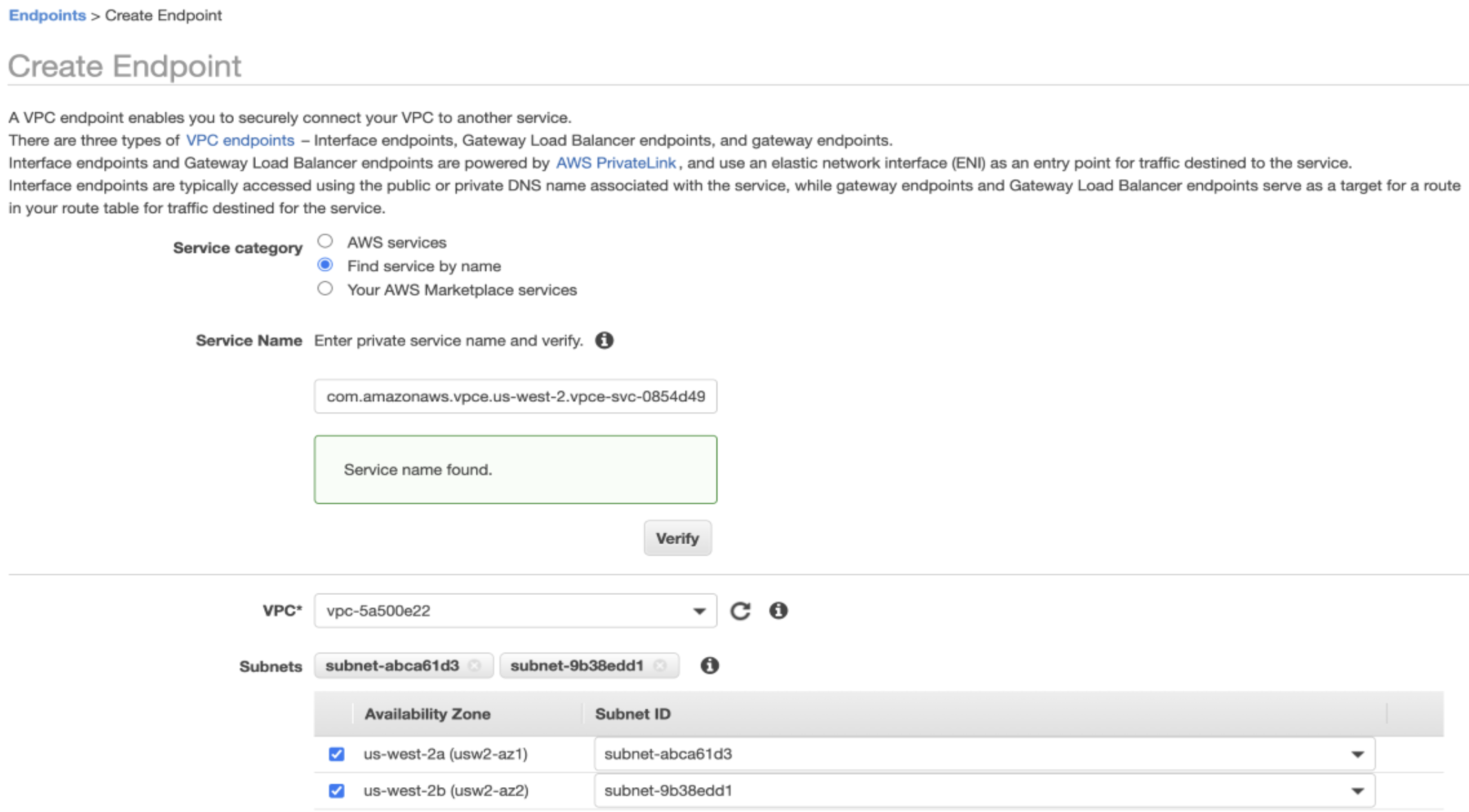
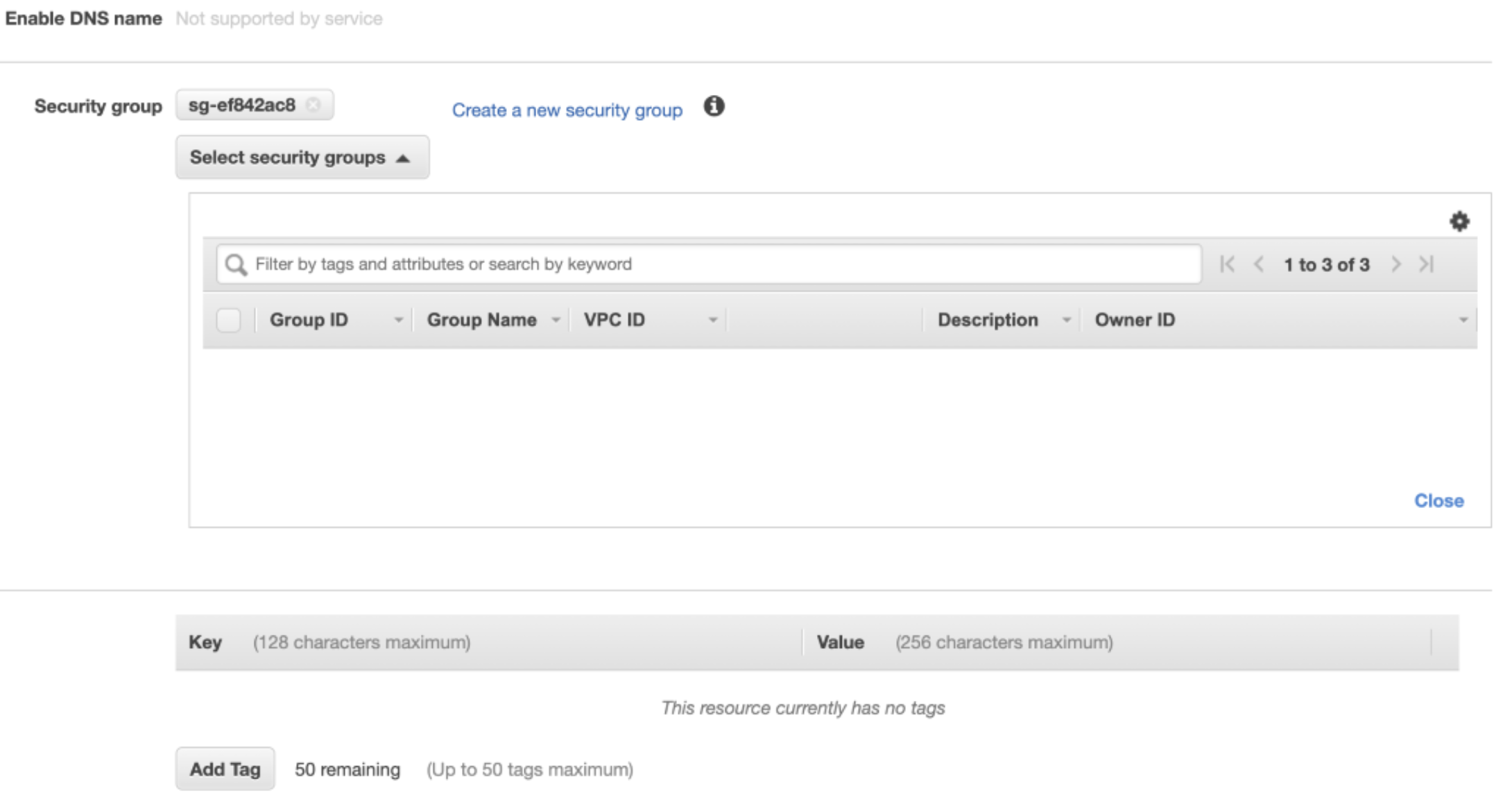
Make sure correct security groups with correct rules are present
-
Connectivity from on-premises is done via Aviatrix S2C which could be over direct connect or public internet. The workflow for this connectivity is simple using the Aviatrix Controller. You can follow the instructions as mentioned on the link below. https://docs.aviatrix.com/HowTos/site2cloud.html
Private Link Visibility and Monitoring
Private Link by default does not provide detailed visibility and monitoring. Aviatrix CoPilot is the one that provides visibility and monitoring at a deeper level. Admins can search with source IP, destination IP, hostname etc.
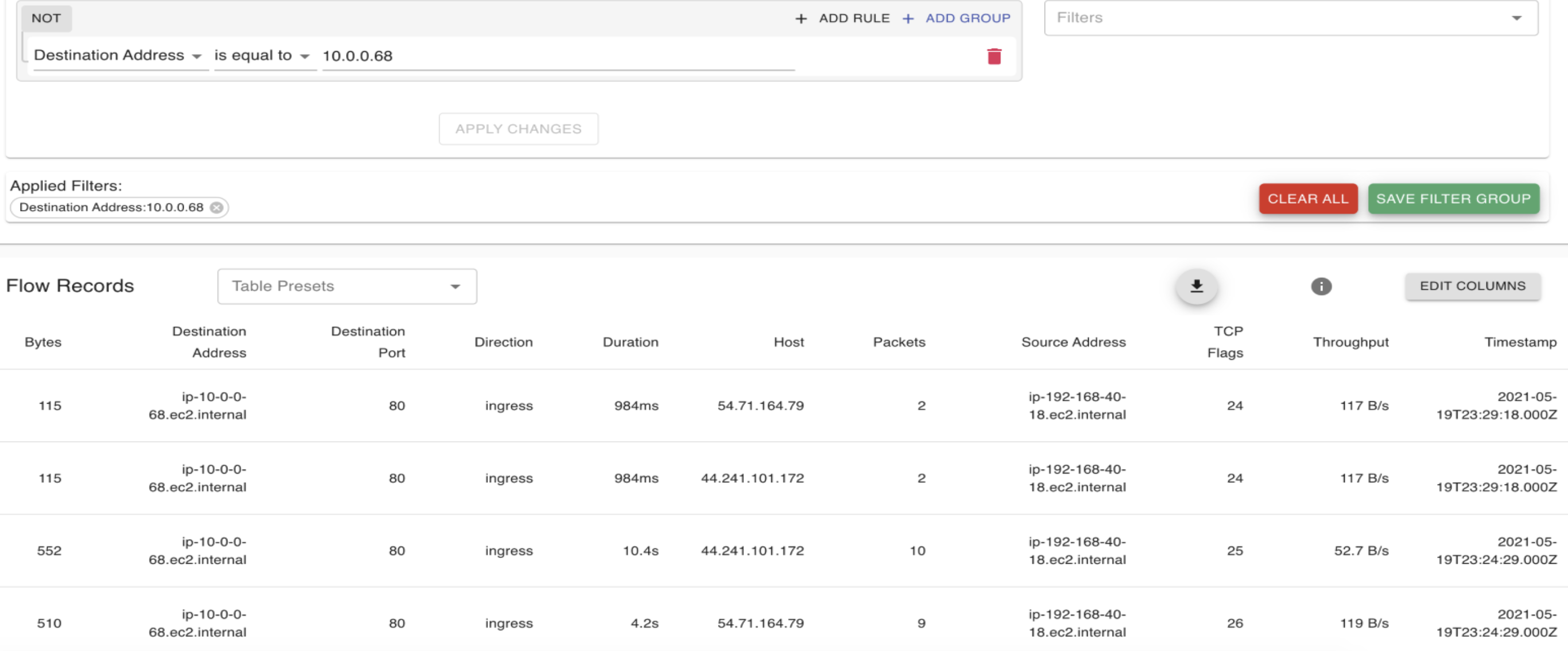
Here the filter is applied on the Source IP (192.168.40.18) which is the IP on the on-prem side as mentioned in the diagram above towards the service
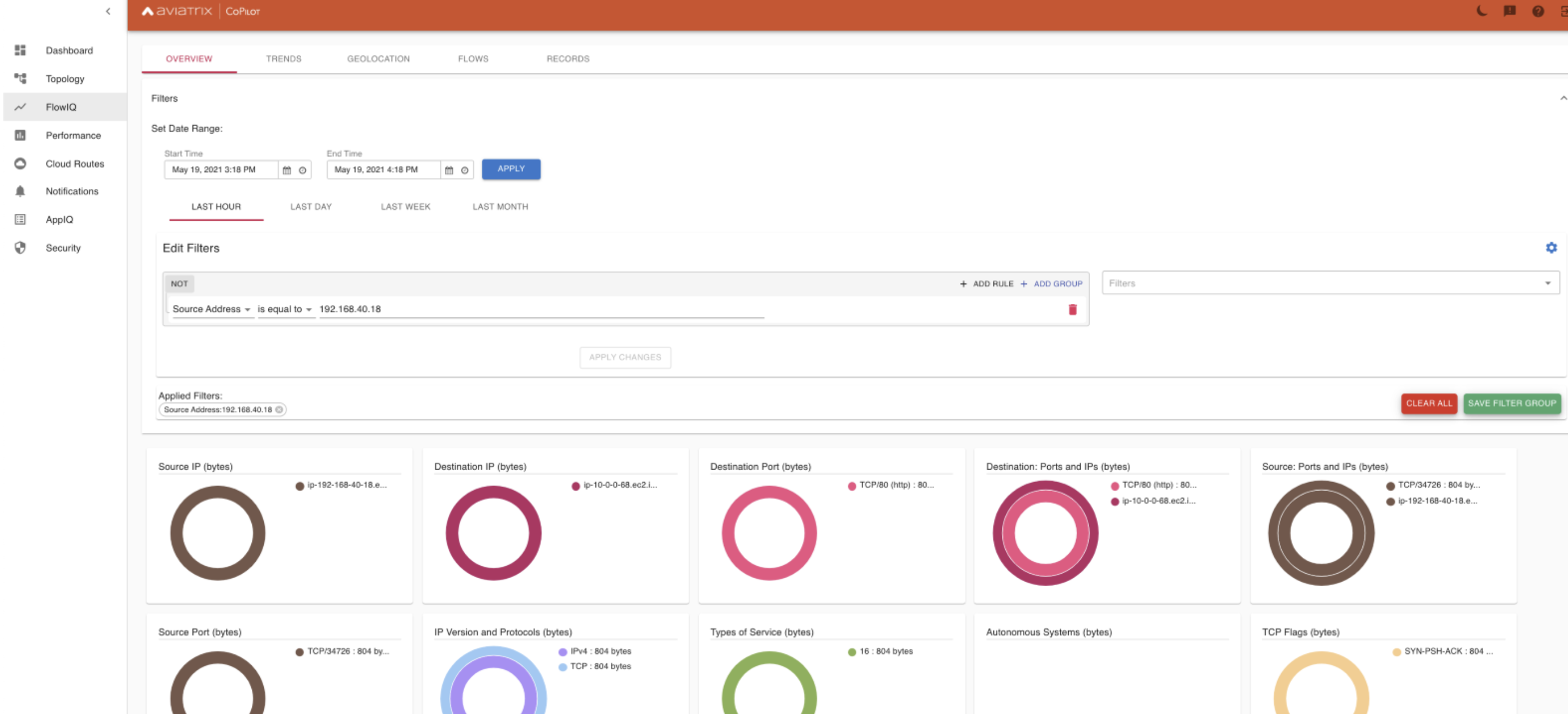
Filter applied on the Interface endpoint IP shows the details around traffic received and session times.