Problem Statement:
Connecting to cloud from on-premises can be challenging when you have overlapping subnets. The overlapping subnets can be with your VPC/VNET in the cloud, or it could be with another branch, affiliate or partner site.
Solution:
Aviatrix offers multiple solutions to solve overlapping subnet scenario. In this document we are considering overlapping subnet between branch and Application VPC in AWS.
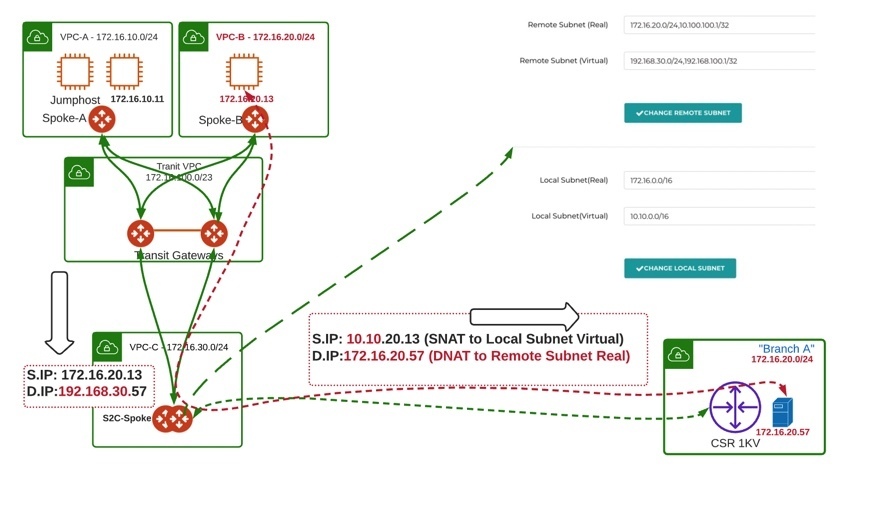
In this example, we have overlapping subnet with one of the branch subnet, the subnet 172.16.20.0/24 is overlapped with our application VPC (VPC-B) CIDR in AWS. We will be using Mapped-NAT feature on Aviatrix Spoke gateways, which will perform 1:1 NAT. Mapped Net Site2Cloud provides the advantage of not having to configure individual SNAT/DNAT rules.
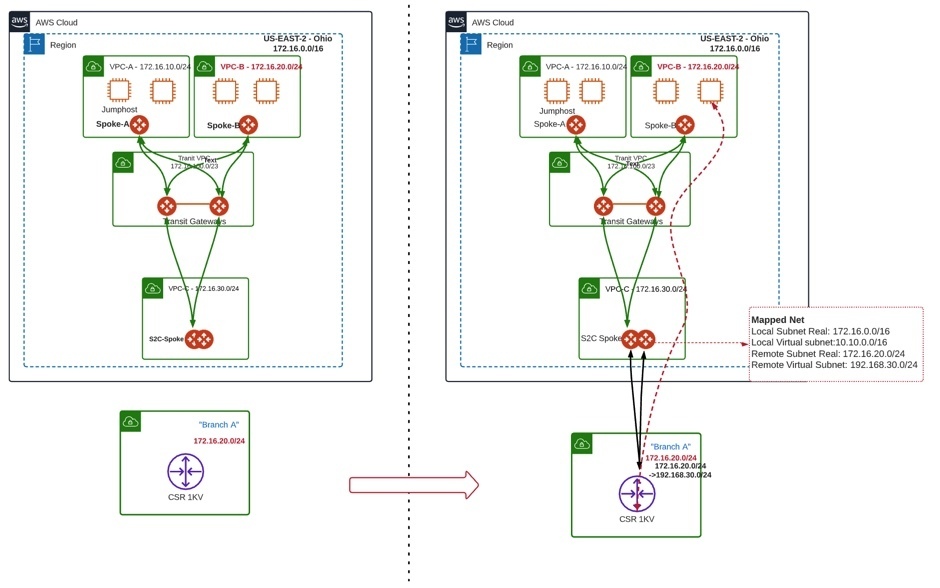
In reference topology below we have two Spoke VPCs where applications are hosted. Both Spoke VPCs have Aviatirx Spoke Gateways and attached with Aviatrix Transit Gateways in HA. A dedicated VPC (S2C) has been created for all on-premises branch offices connectivity. To simulate the Branch, a Cisco CSR router has been provision in a separate VPC.
This document does not cover the configuration details of VPC, Spoke gateways and Transit Gateway creation and attachment. The focus here is provide configurations details on Site2Cloud connectivity with overlapping branch subnet.
Reference Topology
Configuration Steps:
Following are the configuration steps, as it pertains to Site2Cloud connectivity and overlapping subnet.
· Before configuring S2C connection to Branch router, validate the connectivity and routing between Spoke VPCs and transit VPC on Aviatrix controller.
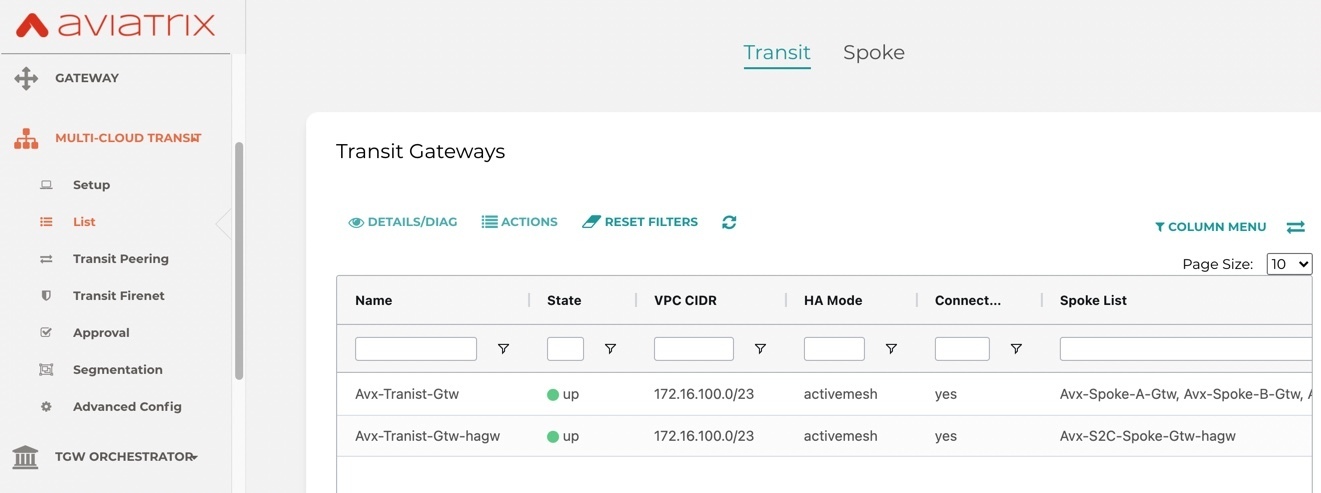
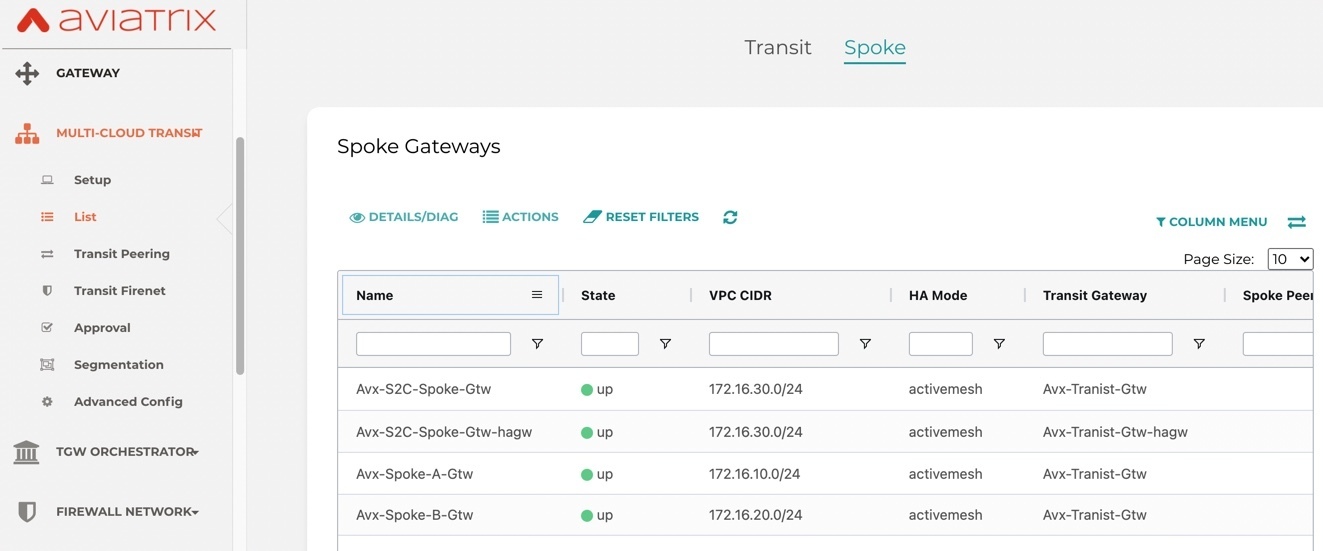
· Create a Site2Cloud connection to On-prem Branch Router
Create a Site2Cloud connection to Branch-A with Mapped Option on S2C Spoke Gateway
Key parameters on site2cloud IPSEC configuration:
Connection Type: Mapped
Tunnel Type: Route-based
Enable HA: Selected (in case of HA Spoke gateways)
Remote Gateway IP address: Branch_Public_IP
Remote Gateway IP (backup): same as above (in case of single branch router)
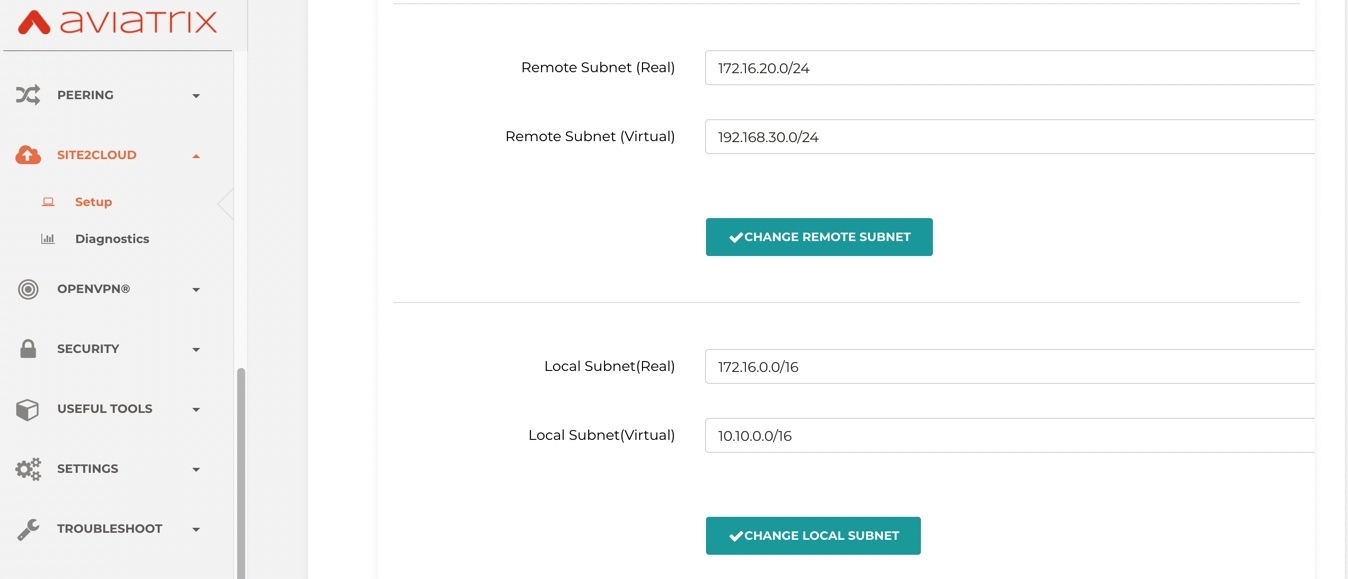
Local Subnet (real): 172.16.0.0/16
local Subnet (virtual): 10.10.0.0/16
Remote Subnet (real): 172.16.20.0/24
Remote Subnet (virtual): 192.168.30.0/24
· Select the newly created S2C connection then Edit
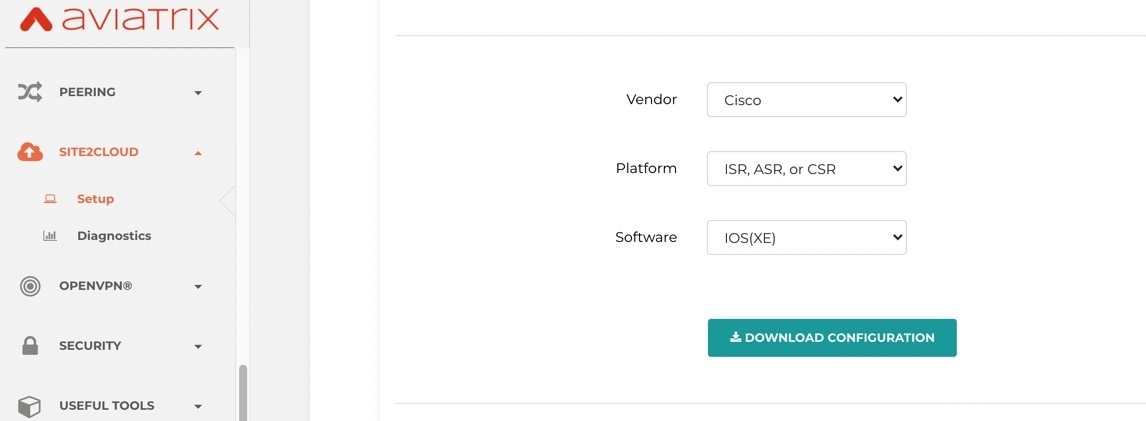
Download the configurations by selecting below parameters.
Vendor: Cisco
Platform: ISR,ASR, or CSR
Software: IOS(XE)
Update/Change downloaded configurations file as instructed, then apply the configurations on Branch CSR router
· On Aviatrix Controller, Site2Cloud –> Setup wait for connection status to come up
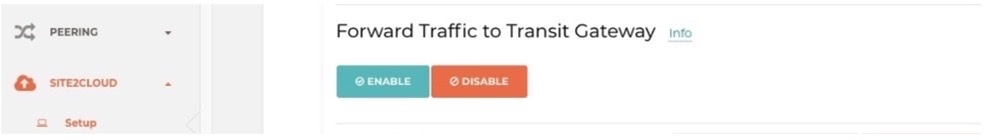
· Select the newly created S2C connection then Edit -> enable “Forward Traffic to Transit Gateway”
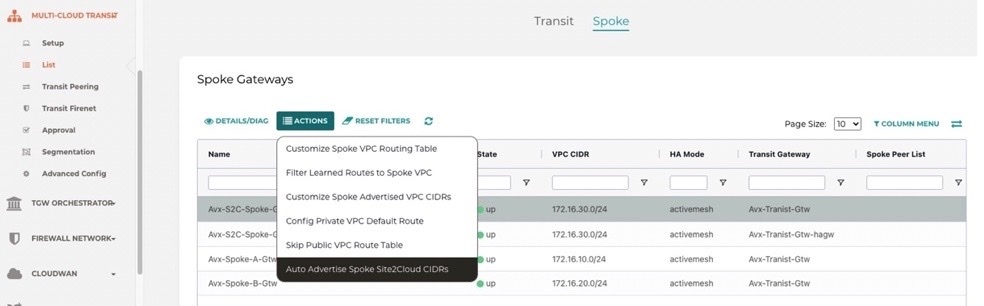
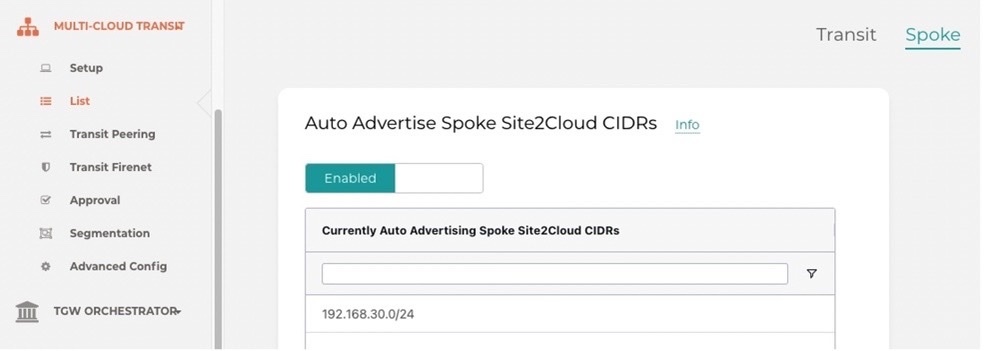
· Multi-Cloud-Transit -> List -> Spoke -> S2C-Gateway then Actions -> select Auto Advertise Spoke Site2Cloud CIDRs
https://docs.aviatrix.com/HowTos/transit_list.html#auto-advertise-spoke-site2cloud-cidrs
Testing & Validation
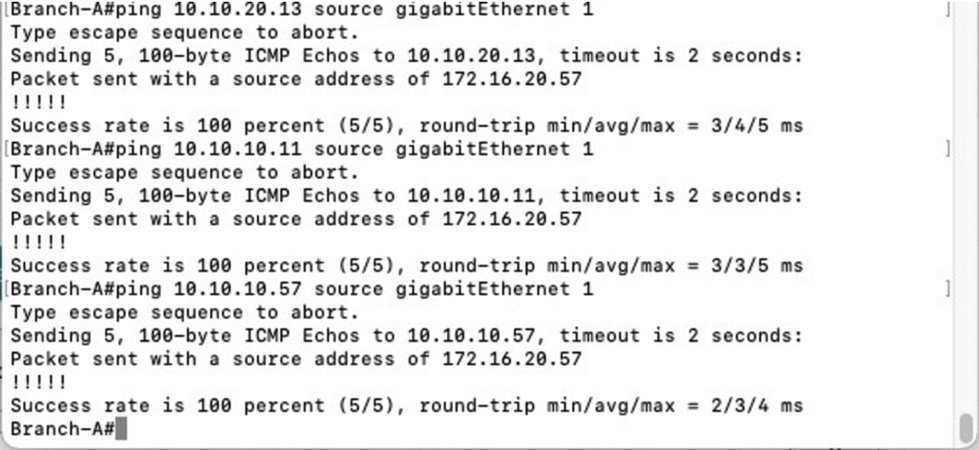
· Test connectivity, from Branch-A CSR ping VPC-B instance using virtual network CIDR with the real host portion of its IP address. In our example our host in VPC-B has real IP address of 172.16.20.13, then we should ping 10.10.20.13 from Branch CSR. Similarly, we can also ping VPC-A instance 172.16.10.11 using its virtual IP of 10.10.10.11.
· Review and verify the NAT translation state table of S2C gateway
From controller, Troubleshooting -> Diagnostics -> Gateway -> Session View -> Select S2C-Spoke-Gtw
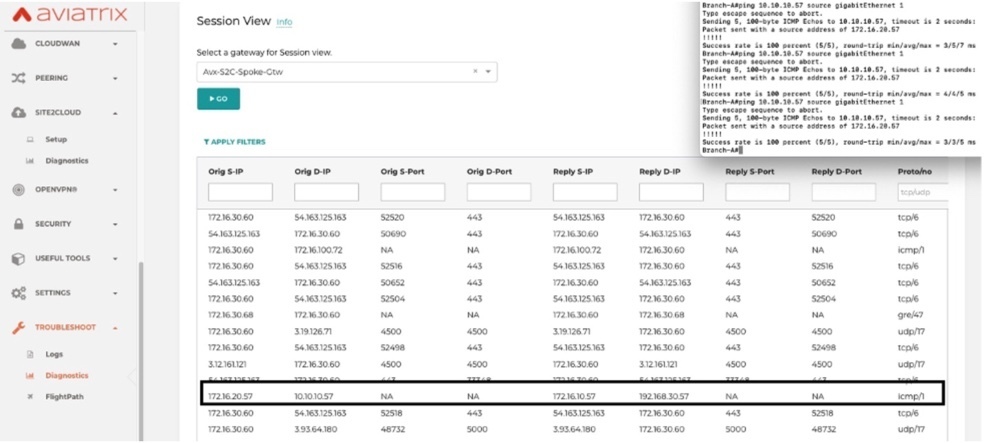
· Packet Walk from VPC-B instance (172.16.20.13) to Branch IP (172.16.20.57)