For any additional questions you have about this concept, check out our FAQ page.
Firewall Network - FireNet
After onloading any meaningful workload on the cloud, the Security Policy mandates that the traffic going to and from the workload is inspected using a Firewall because the layer four security groups are not enough to pass the audit. The traffic needing inspection could be East-West or North-South.
Aviatrix provides a solution that allows enterprises to apply the firewall in any possible area or direction.
- In VPCs/VNets inside a cloud.
- If the traffic is going towards the Internet (Egress).
- If the traffic is coming from the Internet (Ingress).
- Traffic coming in from the Data Center.
- Any branch and partner site connected to the cloud.
- The traffic sent to another cloud.
This solution is unique because there are many problems that come with inserting firewalls in Cloud Networks:
- The Firewall Vendors typically provide the firewalls but the customer is responsible for managing and routing the traffic to the firewalls themselves and managing it through and through.
- The Cloud Providers often don’t have L7 Firewalls, and if they do, the features are limited in terms of those required for an enterprise. Similar to the solutions provided by the Firewall Vendors, the customer is responsible for routing the traffic to the firewalls themselves and managing it through and through.
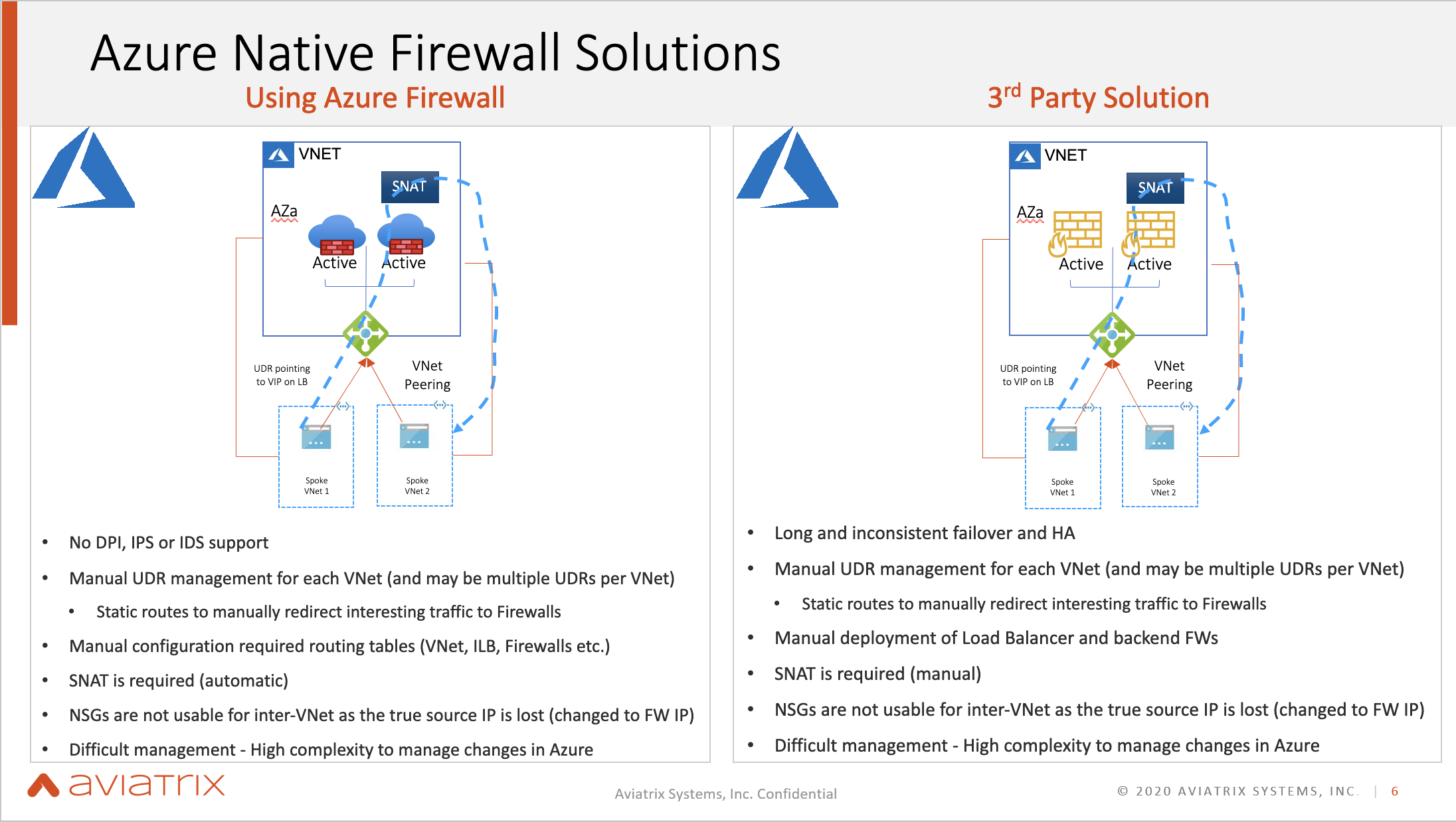
The Azure Native Solution
Azure has a native firewall, but the problem is that when users want to send the traffic from one spoke VNET to another, they must make sure the UDR’s are done properly so that it can point to the VIP of the load balancer correctly, go into the Firewall, and then to the destination. Furthermore, when running in Active Active mode, they must also deploy the SNAT so that the return traffic doesn’t hit the wrong firewall. Essentially, manual configuration is required and it takes high complexity to manage changes in Azure. The same challenges can be seen in a 3rd party firewall solution, with the additional challenge of having to configure the SNAT as well.
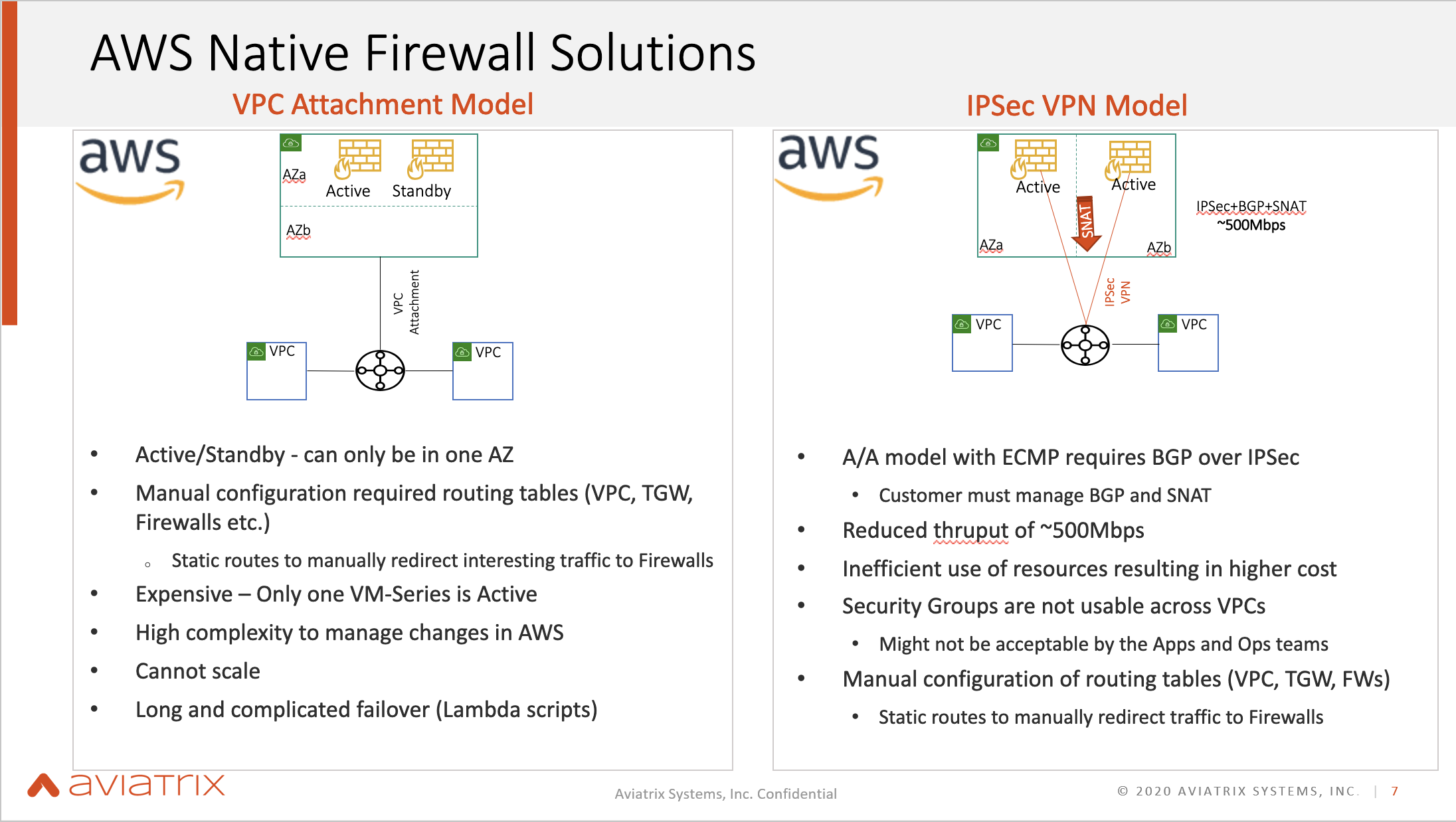
The AWS Native Solutions
The VPC Attachment Model
One of the problems with AWS’s Native Solution is that the Active Standby can only be deployed in one AZ, even though the solution is quite expensive with only one VM-Series being active.
Because AWS has a TGW, it is possible to attach to the VPC to get more throughput. However, all of these routing tables also have to be manually configured so that the traffic can go where it needs to be.
The IPSec VPN Model
In this model, the IPSec Tunnel is built towards the Firewall, giving users 1.25Gbps throughput, which effectively gives users about 600MBps because it has to go back on the same VPN link. The throughput will reduce as more advanced features are used. Source NAT is another challenge.
Aviatrix Transit FireNet Solutions
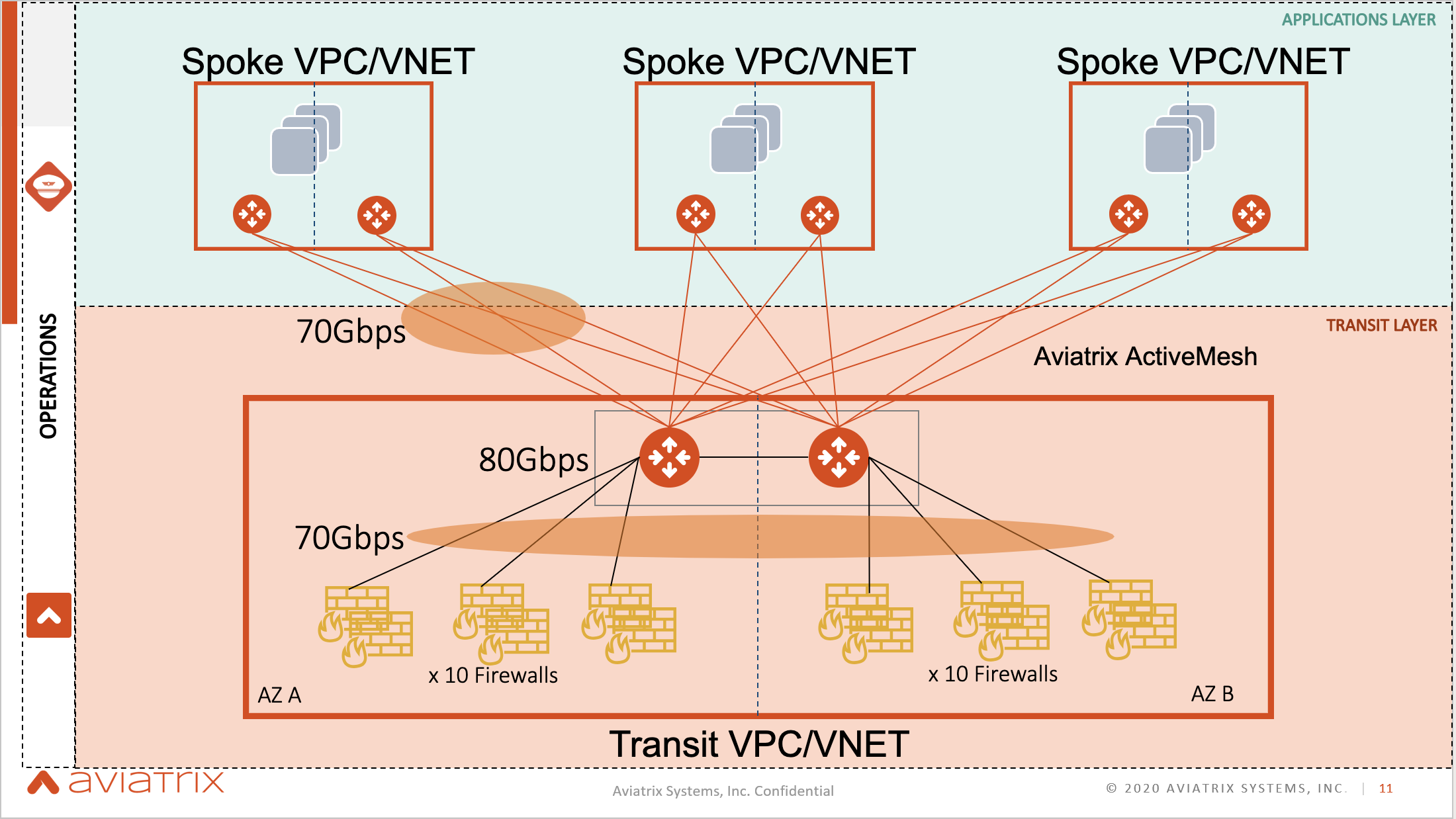
Aviatrix solves for the shortcomings of the native solutions provided by the CSPs by deploying the firewalls into the Transit VPC. This helps to utilize the full performance of the firewalls, simplifies the management of all the networking elements because Aviatrix takes care of it, and allows enterprises to scale with ease and no compromise in visibility.
This architecture consists of Active Active Gateways in an active mesh, and also provides a scale up option. This solution has a throughput of 70 Gbps, compared to the AWS TGW throughput of 1.25Gbps.
Aviatrix AWS TGW FireNet
When deploying the Aviatrix solution with the AWS TGW, all users have to do is attach the Transit VPC to the AWS TGW.
This automatically sends the traffic to the Fire Wall without any additional components, such as an IPSec tunnel, or a SNAT. This also doesn’t require a BGP.
Some benefits of this approach compared to the native one include the maintenance of the session stickiness, load balancing provided by Aviatrix, and integration with Panorama.
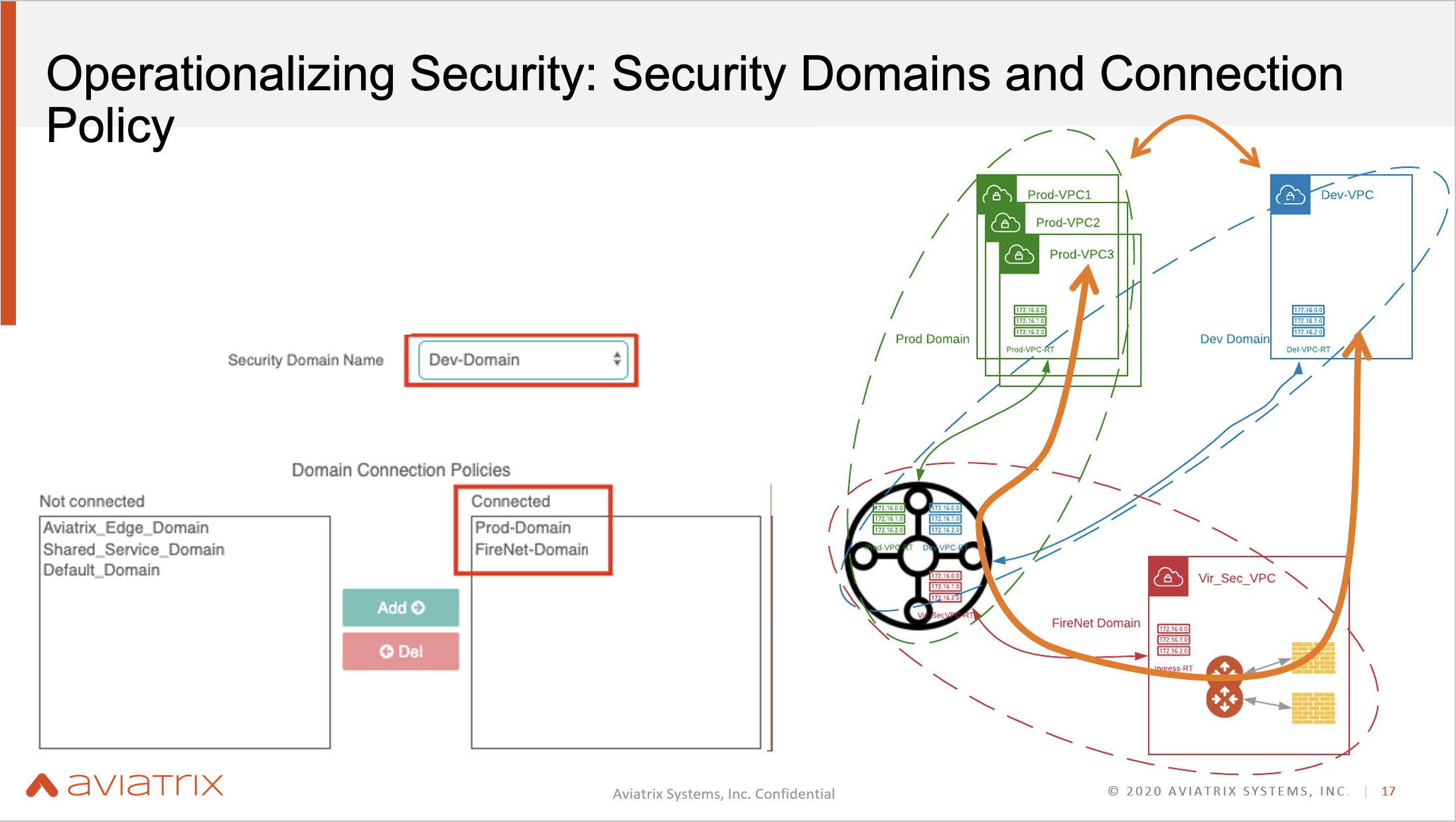
Aviatrix Security Domain
This allows enterprises to create policies and then implement network segmentation. For example, users can put all their production workloads in one production domain and all their developer workloads in another developer domain. This will allow the enterprise to disable traffic between the two domains, or set security policies to manage the communication.
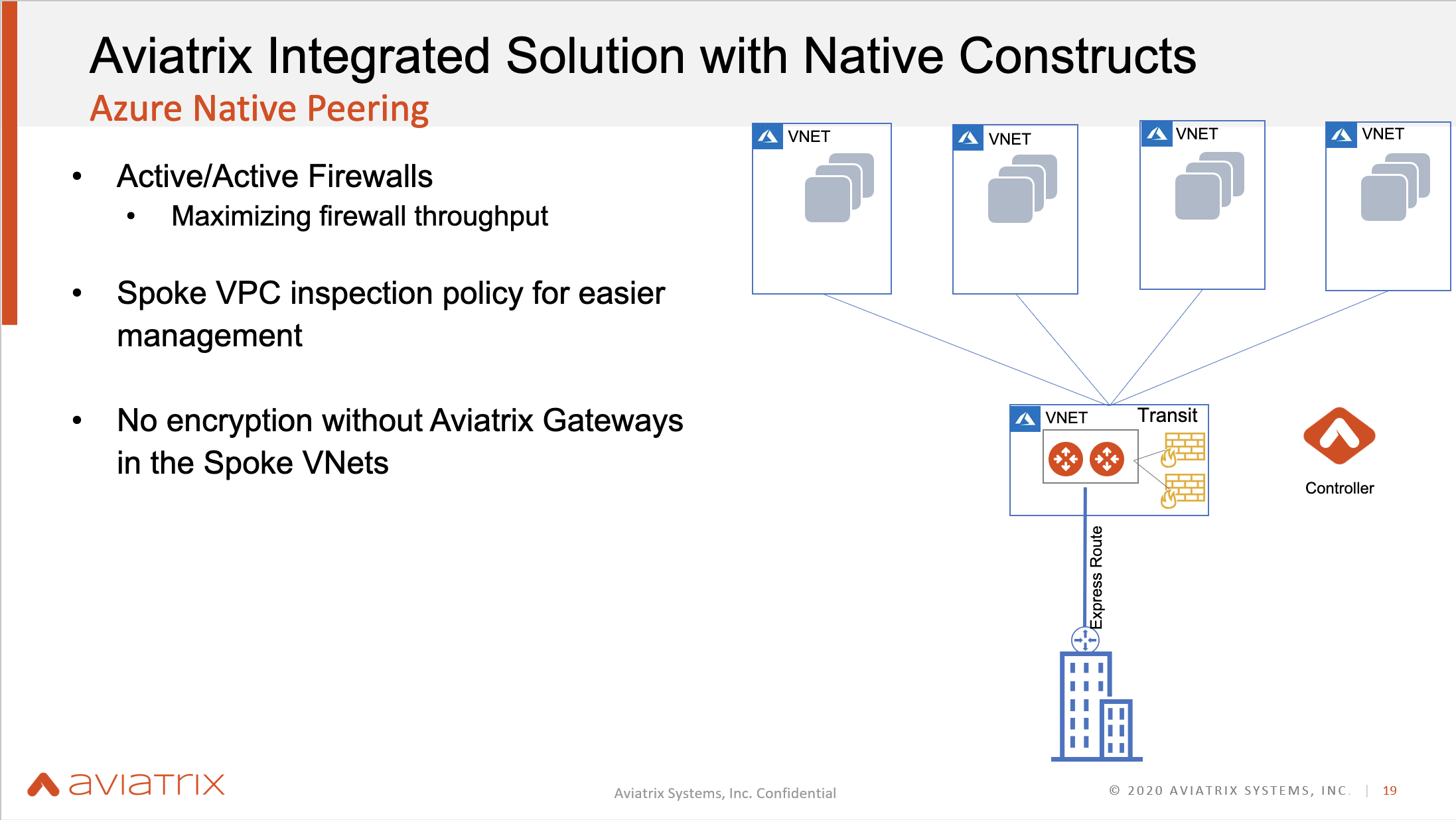
Aviatrix Azure Native Peering FireNet
The Aviatrix FireNet Solution works in Azure almost exactly how it works in AWS, with the only difference being that there will be no encryption without the Aviatrix Gateways in the Spoke VNets.
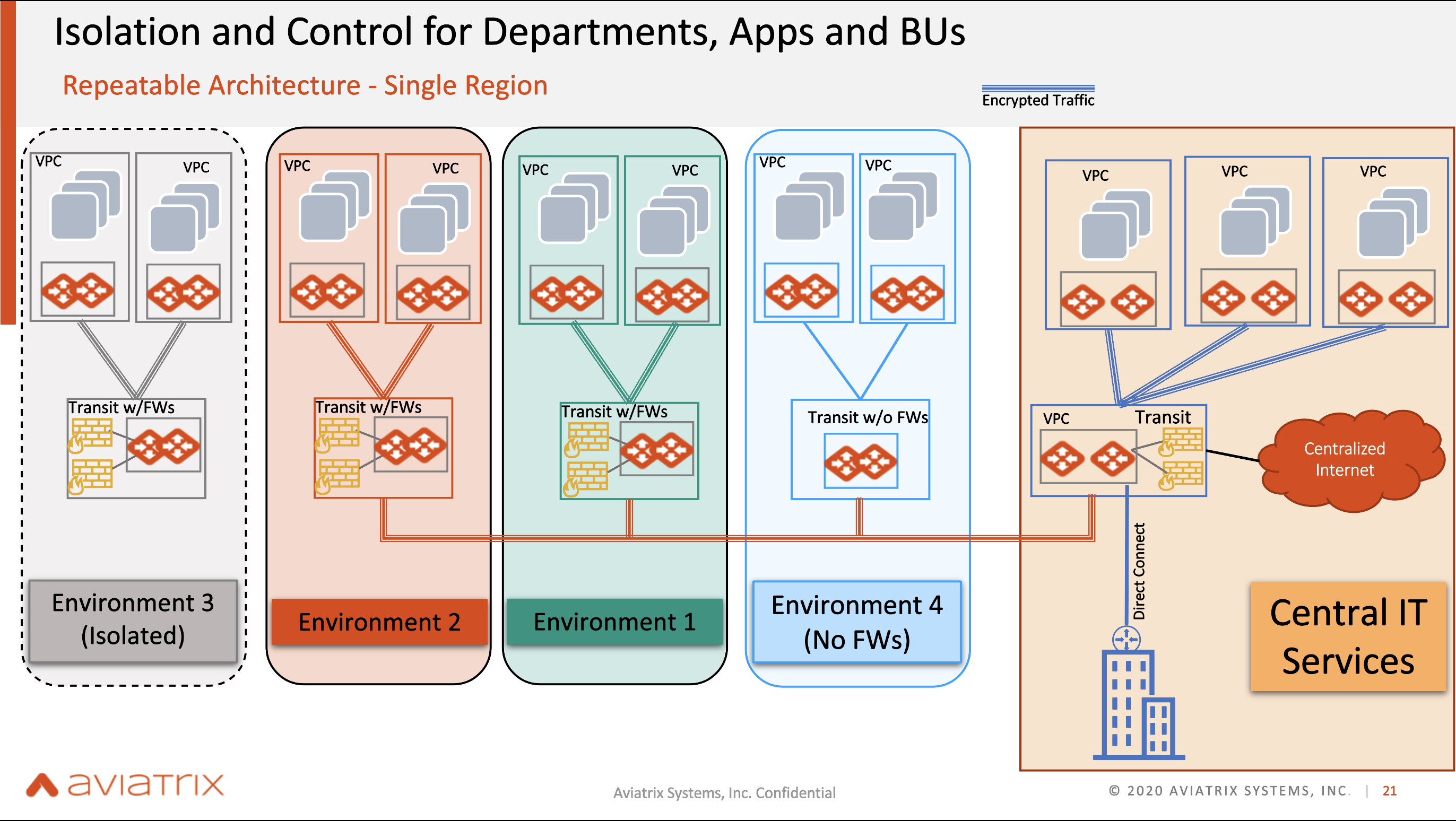
Single/Multi-Region Multi-Cloud Aviatrix Transit FireNet
It is very easy to connect different business units with varying requirements within a single region. For example, if an environment doesn’t require a FireWall while the others need one, that is possible. Similarly, it is possible to have an environment that is isolated within the business unit. In a multi-region, this is still possible.
For more information, watch the video above.