Aviatrix Multi-Cloud Networking platform version 6.3 brought a lot of exciting and important features for enterprise customers. It is an action-packed release with great enhancements in Cloud Networking, Security, and Operations areas. This post will focus on GCP enhancements and new features.
Cloud Security - Service Insertion and Chaining
Automated and Policy-based service insertion and chaining have always been a real pain point for enterprise GCP customers. Native solutions are not adequate and 3rd party vendors' solutions leave it up to the enterprise architect to figure out the end-to-end solution architecture.
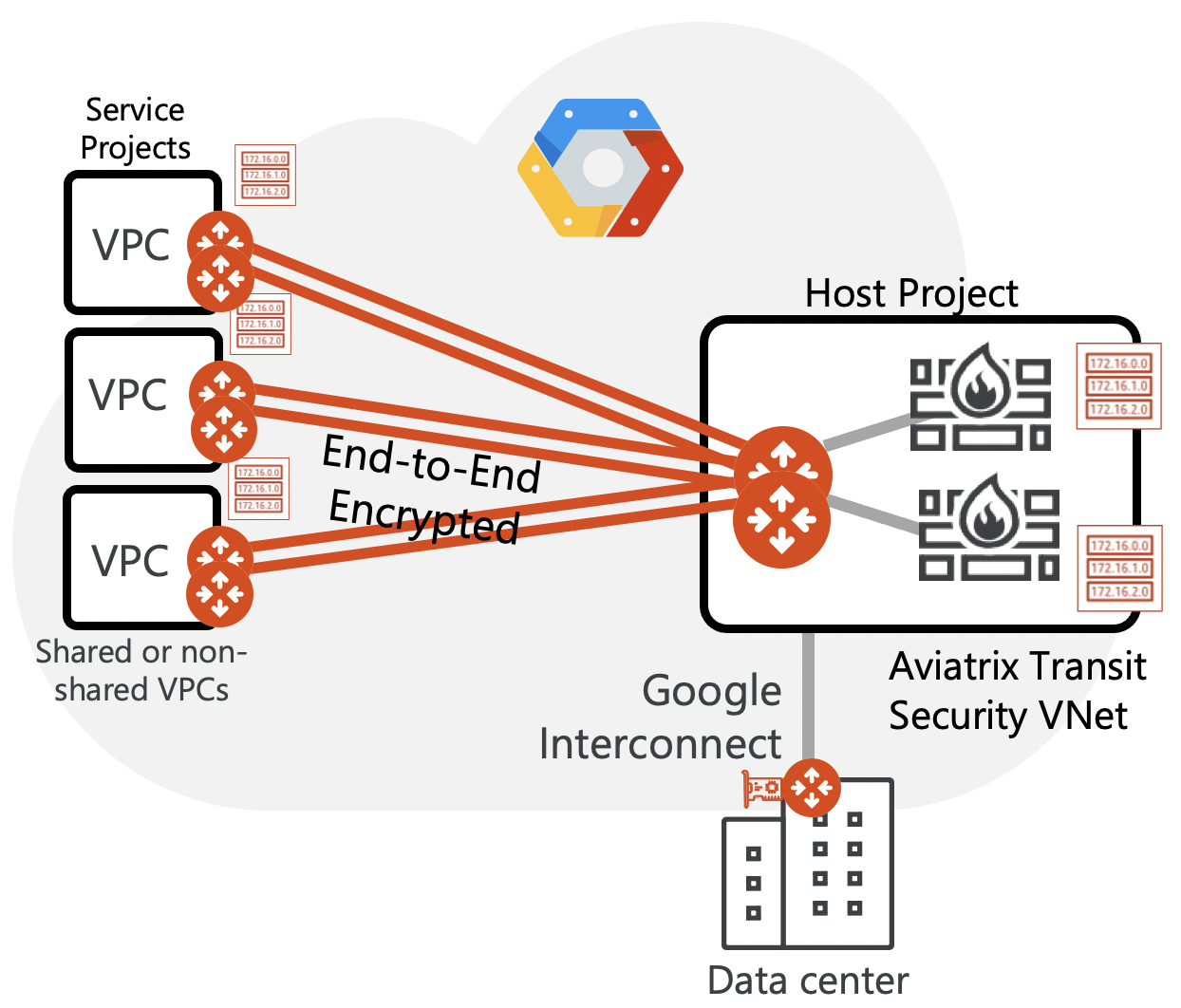
Aviatrix GCP FireNet GCP solves all those challenges and limitations and provides a best practice way to Service Chain NGFW and other services into a cohesive architecture.
Aviatrix Solution Advantages
- Policy-Based Inspection – decide what traffic is being inspected
- Traffic Engineering – customize traffic flow
- NGFW Life Cycle management – deployment of VMs
- Automated Route Propagation – the controller manages the firewall’s route table
- HA with Automated Failover
- Flexible Design Options
- Single Centralized Security VPC
- Dual Centralized Security VPCs with Dedicated E/W + N/S VPC and Dedicated Egress VPC
- Full visibility on E-W/on-prem to cloud traffic flows
- No BGP/ECMP
- No SNAT required when Symmetric Hashing is enabled
More design and deployment details here
We want to highlight two large enterprises utilizing Aviatrix FireNet to solve NGFW service insertion pain points.
1- Hospitality Chain: Ingress traffic inspection for GKE Workload
For this customer inspecting ingress traffic for GKE ingress controller traffic was a challenge for GKE workload based on their compliance policies. Following explains their ingress web traffic requirement
- Route ingress traffic to a dedicated Ingress Spoke VPC first
- Ingress VPC has an Nginx LB that would receive the traffic.
- Then application LB policies were looked into and then based on the ingress service, the traffic must be routed to a centralized VPC where NGFW were deployed
Without Aviatrix, they were forced to terminate the ingress traffic directly to the NGFW which was not abiding by their Ingress traffic requirement. Also without Aviatrix, they were forced to figure out the routing and manually adjust the route based on a new service they would spin up.
Aviatrix FireNet policy-based and flexible model allows them to achieve the requirement with the traffic engineering demanded by the GKE workload
2- HealthCare Provider: Highly Available and Policy-Based Egress Traffic Inspection
This provider processes a large number of image and vidoe scane for their clients. The egress traffic sent to the clients after image/video processing was done must be secure and inspected by NGFW due to HIPPA compliance needs. They were forced to use Active/Standby NGFW due to various limitations.
Aviatrix FireNet solution allowed them to deploy the NGFW in an Active/Active fashion without involving any manual route updates or GCP network tag management. In case of failure Aviatrix FireNet automatically redirected traffic to the available NGFW. This reduced deployment complexity and manual intervention.
Cloud Security - High-Performance Encryption (HPE)
Aviatrix builds high-performance encrypted networks by default. The solution is called Aviatrix HPE or Aviatrix Insane mode.
GCP HPE across Google Cloud Interconnect
The Google Cloud Interconnect (GCI) is a great service to provide hybrid connectivity back to the on-premises DCs. For example, Enterprise can get 10Gbps GCI connections for their on-prem to GCP migration needs. The challenge is that GCI is not encrypted and the native IPSec encryption only provides 1.25Gbps
Aviatrix provides 20 times more IPSec throughput than standard cloud encryption.
GCP HPE inside Google Cloud (GCP)
HPE is also available for a Multi-cloud Transit solution. For performance benchmarks, refer to GCP Insane Mode performance test results. Insane Mode is enabled when launching a new Aviatrix Transit Gateway or Spoke gateway in GCP.
- Support N2 and C2 instance types on GCP gateways improve Insane Mode (HPE) performance on GCP cloud. For new network throughput with these new instance types, refer to GCP Insane Mode Performance.
Misc. Enhancements
Following are some of the recent enhancements in 6.3, besides many that were done in prior releases. Some are very specific to GCP and some are available across multiple clouds (AWS, Azure, OCI) including GCP.
Cloud Operations
- GCP Shared VPC (Host Project) and Service Project enhancements for FlightPath
Cloud Security - Hardened and Locked Down Platform
Among so many other features and enhancements, taking care of the Aviatrix Platform and its software components is equally important.
- ssh access is blocked by default blocked to Aviatrix Gateways
- The access is only opened during the troubleshooting session
- ssh can only be done by the Aviatrix support team
- ssh port remains open only during the troubleshooting session
- ssh is only allowed from the Aviatrix Controller
- Once the support session is over, the firewall rule is removed
- Access to Controller is blocked by default
- One has to open it by going into Troubleshooting --> Diagnostic --> Remote Support
- A random ssh port will be generated only for that session
- The aviatrix support team will log in to Controller
- ssh to gateways is only allowed from the Controller and only for the duration of troubleshooting session
- It should be disabled as soon as the troubleshooting session is done with the Aviatrix support team
Cloud Security - GCP Restricted Access with Custom Roles
- With 6.3 we are reducing the scope for cloud API call from the gateway
- We are also taking out the default service account credentials while launching the Aviatrix gateway
Prior to 6.3
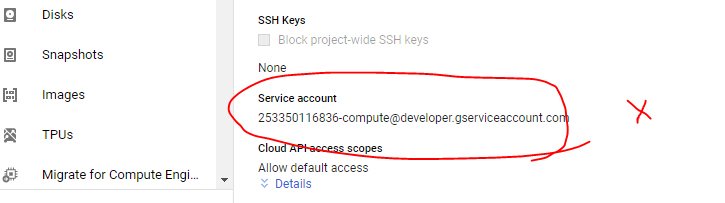
With the 6.3 release, you should not see any default service account and API scope should be none for increased security.
Cloud Core (Transit Network)
- Granular control to block SNATed traffic based on GCP Network Tag and native route priority
- Enhanced GCP Shared VPC and routing control using native and advanced capabilities using Aviatrix Transit
GCP Outbound Rules
Enhancements are added to GCP gateway instance that explicitly opens the default route CIDR (0.0.0.0/0) to all destinations. This helps security and compliance team for audit purposes.
Stateful Firewall Rules
Stateful Firewall Rules Enhancement simplifies editing and viewing IP address based stateful firewall rules, allowing large set of rules to be managed easily. To configure, go to Security -> Stateful Firewall -> Policy to edit policies.
Route based IPSEC with IKEv2
Provides an option to run route-based VPN with IKEv2. For more information, refer to Create Site2Cloud Connection.
DPD Parameters for S2C Tunnels
This can now be modified through the Controller User Interface in additional to API and Terraform. One use case of modifying DPD parameters is to reduce tunnel failure detection time. To configure, refer to DPD Configuration.
Event Trigger for S2C
This is a new mechanism to reduce failure detection time. This is an alternative to the default setting where tunnel status change is detected by a periodic monitoring process running on the gateways. To configure, refer to Event Triggered HA.
