Preamble
In today’s multi-cloud world, companies struggle to manage data exfiltration and malicious traffic across cloud service providers (CSPs).
Enterprises have limited control, visibility, and network security across multi-cloud deployments. Bad actors across the globe are using new methods to evade traditional network security measures. Data exfiltration and botnet operations may not be countered effectively due to traffic funnelled through security choke points or third-party appliances serving as choke points. Furthermore, a coordinated strategy to protect against malicious activity is difficult to execute since organizations might have separate cloud teams managing each CSP. Separate cloud teams create organizational redundancies and high mean-time-to-resolution (MTTR).
What does “Data Exfiltration” mean?
Data exfiltration has multiple meanings. We will focus on unauthorized access to data that is re-reouted to unapproved third-party destinations. This can cause reputational and financial damage to an organization.
How Does Data Exfiltration Occur?
Data exfiltration can occur by:
-
Corporate data falls into the hands of adversaries through phishing.
-
Malware spreads across an organization’s network and infiltrates other devices. Some types of malware lay dormant on a network to avoid detection by an organization’s security systems until data is exfiltrated subversively or information is gradually collected over a period of time.
-
An insider intentionally contacts a malicious host to exfiltrate information and export sensitive data.
-
An employee uses a Tor relay node to anonymize themselves.
-
An employee uses the organization’s cloud resources to mine cryptocurrency and sending information to the Bitcoin blockchain.
Other types of malware lay dormant on a network to avoid detection by organizations’ security systems until data is exfiltrated subversively or information is gradually collected over a period of time.
What is a botnet and why should you care?
A botnet is a network of hacked machines across the world that is controlled by an attacker using Command & Control (C&C) software running on a server used as the command center. C&C software is used to send commands to systems compromised by malware in order to perform Distributed Denial-of-Service (DDoS) attacks on other organizations or critical infrastructure, steal data, send spam, and allow the attacker unrestricted access to the device and its connection.
Security in Multi-cloud Architectures
Cybercriminals use different techniques to remain undetected for months or years, while data exfiltration or botnet operations are detected only after the damage is done. To add to the complexity, organizations operating in a multi-cloud environment may have an even harder time detecting data exfiltration or botnet operations if each cloud is managed by a different team within the enterprise, requiring more coordination between teams to implement the necessary security.
One security approach is an Intrusion Detection System (IDS), which monitors a network, searches for known threats and suspicious or malicious traffic, and sends alerts upon detection of issues. An IDS relies on searching for available attack signatures and anomalies from normal network activity.
Another method is to use third-party SaaS services. To support this method, traffic must be directed towards the service to perform inspection, which means shipping traffic out of the network for analysis. Many third-party SaaS services also depend on a default route or agents installed on workloads.
Finally, organizations can also use third-party appliances. Traffic must be directed towards these appliances for inspection. We cannot forget that shadow IT may also spin up new environments or make changes redirecting egress traffic.
How Distributed Threat Enforcement Improves Security Posture
Internet access is pervasive in the cloud. This creates business risk, because if the infrastructure has been compromised, data exfiltration, crypto-mining, Tor, and other activities may go unnoticed. You can improve your security posture with distributed threat inspection, a service that complements existing security solutions to provide an added layer of protection.
This solution is un-surprisingly simple: when you first own the network through a repeatable network architecture with a common data plane, distributed threat enforcement will be a natural consequence. Through threat visibility across all “gateways”, threats are identified more quickly, and remediation can be done automatically. This also makes it easier for an enterprise to simplify their processes, workflows, and security investments, allowing them to reduce risk and accelerate the resolution of security events with actionable context.
Introducing ThreatIQ with ThreatGuard
ThreatIQ with ThreatGuard is a new method for cloud network security within the Aviatrix platform that offers distributed threat inspection. It is multi-cloud native network security to identify and block traffic to known malicious destinations.
Imagine distributed threat visibility and control built into the network data plane by default, providing a complementary security solution with full multi-cloud support.
ThreatIQ is like a watchman at the watchtower. It analyzes Netflow data that is sent to CoPilot in real-time. Threat inspection is on by default and is built into the network transit at every hop. CoPilot analyzes all traffic and compares it with a database of known malicious hosts. This is a great example of when an intelligent data plane becomes security-aware.
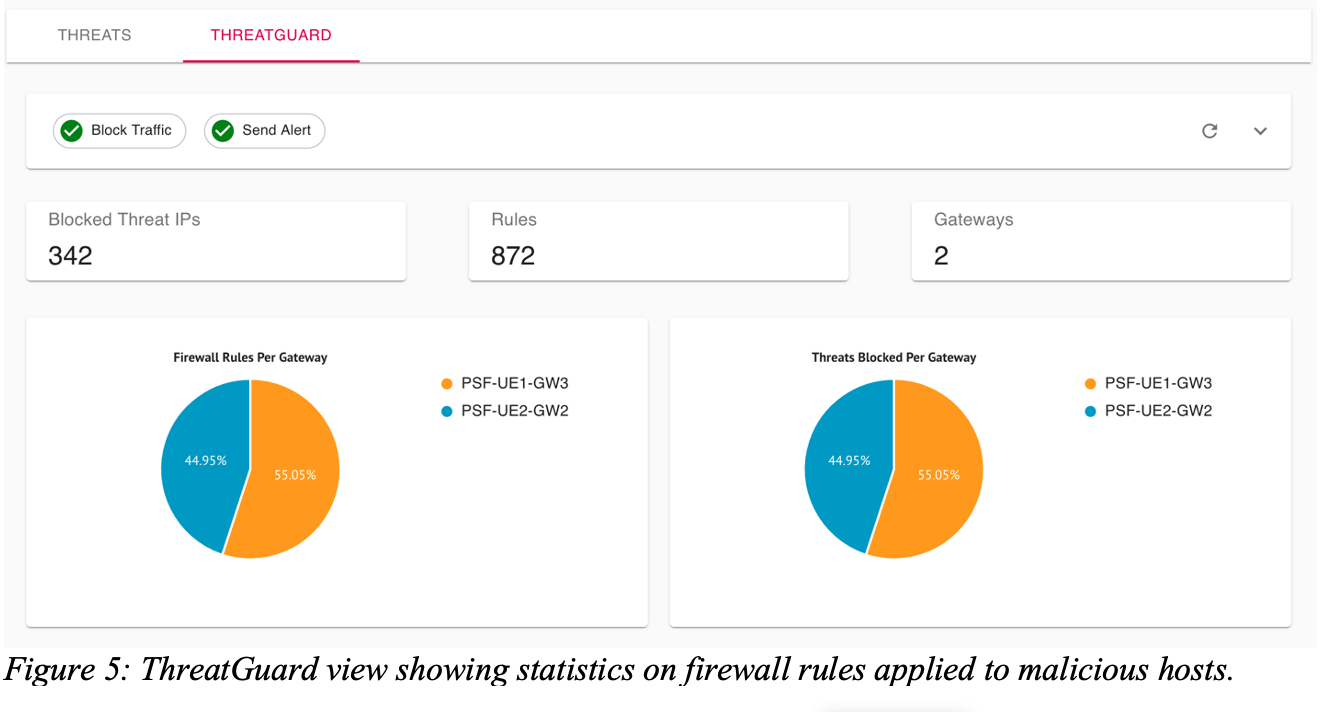
ThreatGuard is like the security guard doing the actual enforcement work. It acts as the remediation mechanism based on CoPilot analysis. If blocking is enabled, these findings are sent to the Aviatrix Controller which then pushes firewall policies to all Aviatrix gateways in the data path blocking the traffic in real-time. Notifications can also be sent to specific users or distribution lists.
What makes ThreatIQ and ThreatGuard Unique
Almost all CSPs have a native solution that provides a means of passing traffic from point A to point B using their network. From a security perspective, customers routinely bolt-on third-party devices to this data path to inspect traffic leaving the network. Aviatrix already provides a novel transit-based network architecture that is repeatable across all CSPs for passing network traffic. ThreatIQ with ThreatGuard also layers in security inspection and enforcement, which adds a layer of protection to complement third-party security devices and provides end-to-end visibility of traffic leaving the cloud network.
How does it work?
ThreatIQ is a detection mechanism that complements existing security solutions by monitoring traffic in realtime as it crosses the network, providing an added layer of protection beyond NGFWs. 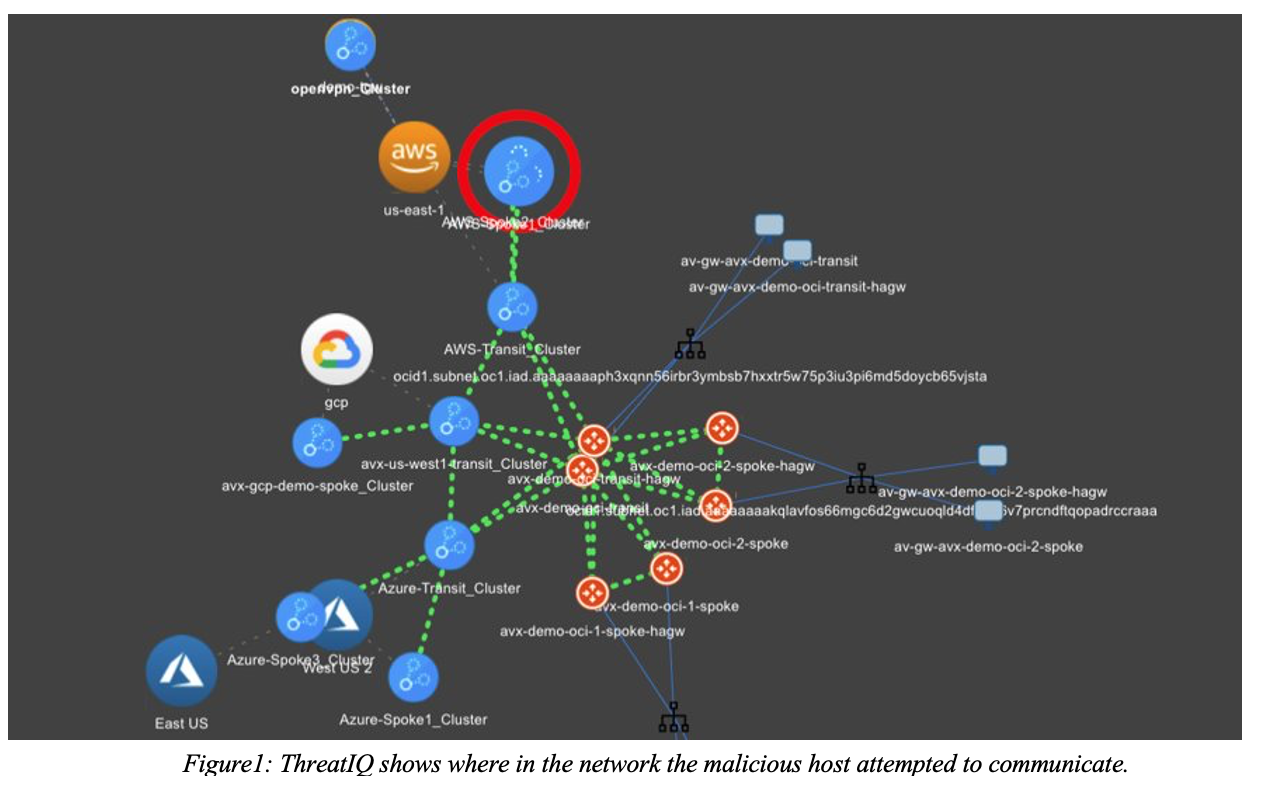
ThreatIQ also offers geographical visualization and threat analytics to show where the malicious hosts are located, time series analysis, and threat classifications/severity. You can also export a tabular representation of the threat intelligence for further analysis.
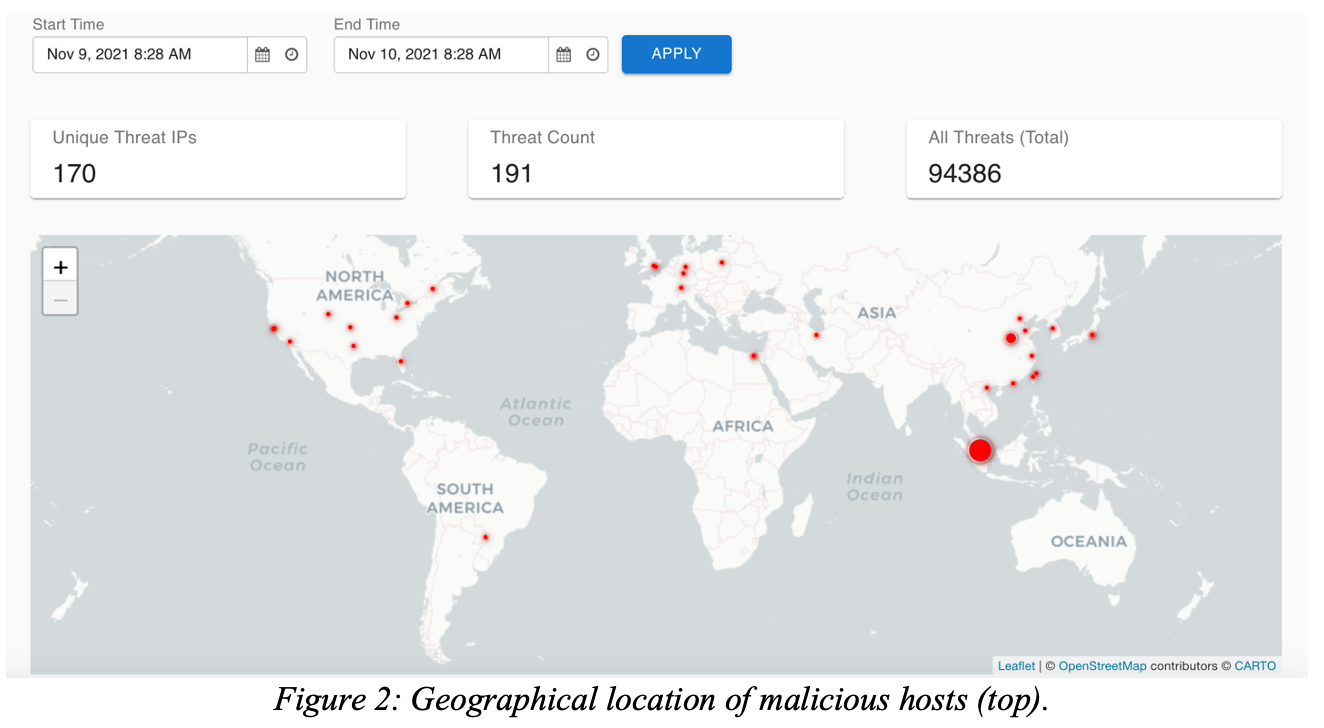
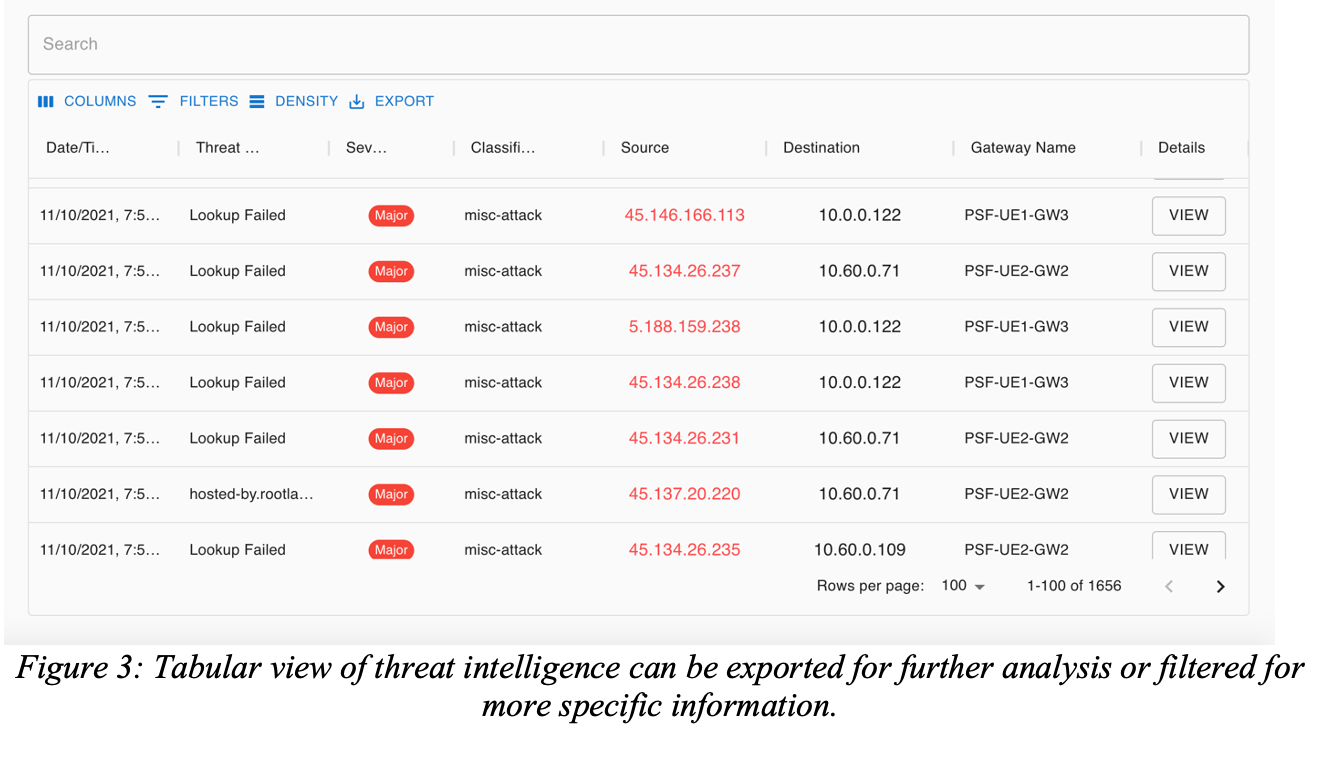
ThreatGuard is an optional mechanism that can be turned on by the customer to act upon findings by ThreatIQ. ThreatGuard can offer to send alerts to specified individuals or distribution lists and can provide automated remediation of identified threats by blocking future traffic to the threat IPs on every gateway. This eliminates the delay involved in manual administrative action and review. It embeds security across the Aviatrix multi-cloud data plane enabling every network node to provide security inspection and enforcement.
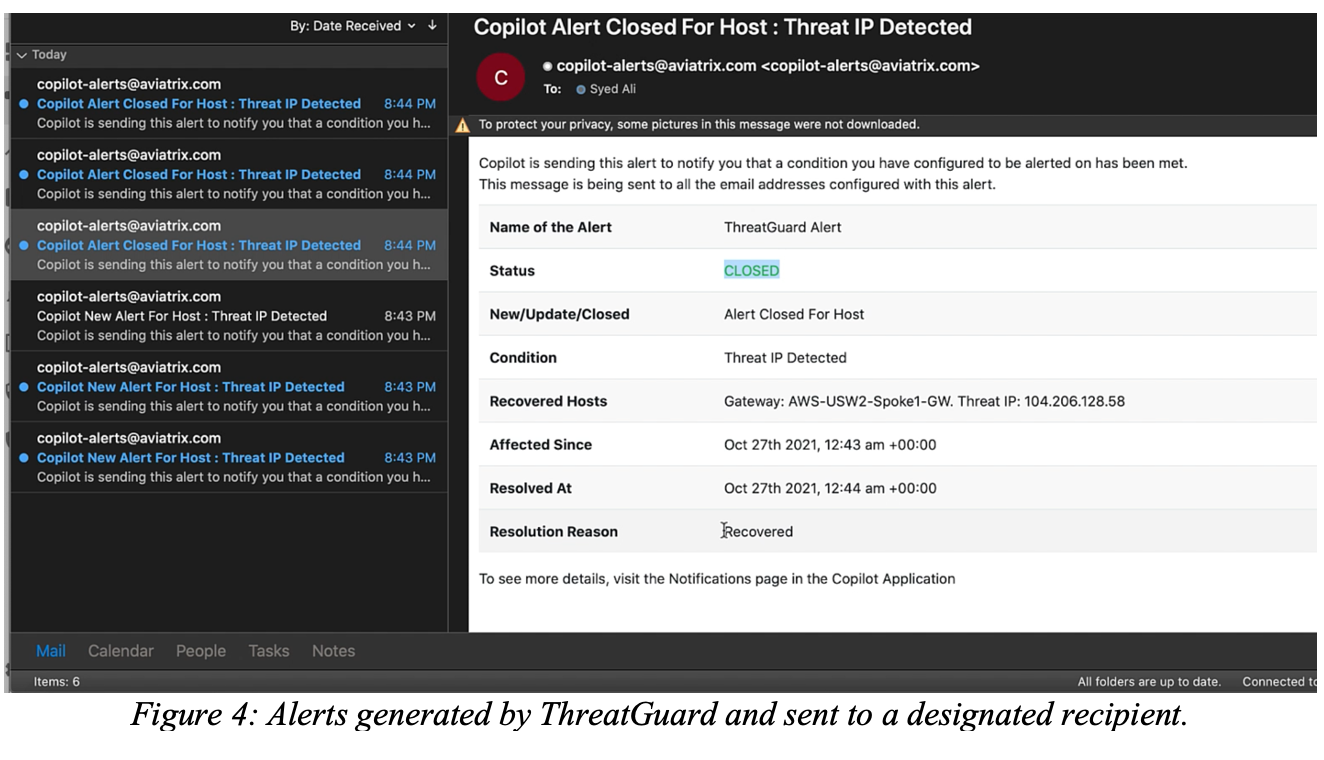
Furthermore, ThreatGuard provides the option to block all traffic to the malicious host. Firewall policies against malicious hosts are automatically applied at every gateway within the cloud network.
Customer Anecdotes and Impact
One of our customers with whom we piloted ThreatIQ immediately became startled upon looking at the geographical view of known malicious destinations communicating with their network. The client’s security team immediately got to work and found out that workloads were communicating back and forth with Tor servers, which are used to anonymize web activity. The security team manually implemented the necessary security groups to block such traffic since, at the time, Aviatrix had not yet built the ThreatGuard feature. Now that ThreatGuard is built, the client’s security team will no longer have to apply manual intervention to block known malicious hosts.
What was also interesting to note was that the client was using Aviatrix only for a portion of their cloud infrastructure. It is quite possible that if Aviatrix was used for their entire cloud infrastructure, more compromised instances would have been found.
Other clients either found bitcoin mining activity or bad actors that were known to create malicious bot activity. Bitcoin mining activity means that enterprise cloud resources (which are expensive and which the enterprise pays for) were being used to make money for bitcoin miners. Malicious bot activity means that a hacker (i.e., the botmaster) has hacked cloud instances to perform data exfiltration or illegal activities.
Aviatrix gives the control, visibility, and security that enterprises always wanted in the cloud. With the official launch of ThreatIQ with ThreatGuard, we expect to hear similar stories from more customers.
Conclusion
In the cloud, Internet access has been extremely easy for workloads. For security personnel, safeguarding connectivity, gaining visibility, and remediating threats have never been more challenging. Even with NGFWs, third-party toolsets, and automation, the risk is but a shadow IT click away. Organizations must look for new ways to ensure critical business workloads are protected without slowing business agility and be able to remediate identified threats quickly and pervasively across the multi-cloud footprint.
ThreatIQ with ThreatGuard is a novel method of network security that truly takes advantage of the data plane in the cloud and improves the security posture. Furthermore, it:
- Complements existing security services by providing visibility at the network layer
- Eliminates dependencies on traffic being identified at the edge or in security pockets
- Survives local changes which may allow Internet egress traffic to utilize alternative paths
- Supports business agility and growth keeping consistent security guardrails through expansion
- Enables a consistent multi-cloud traffic inspection method independent of local NGFW presence
- Provides a multi-cloud native approach to automated remediation
See ThreatIQ with ThreatGuard in Action
Let us show you how you can take control of your multi-cloud environment with industry-leading security, visibility, and advanced networking features.
Schedule a demo to learn why hundreds of customers already use Aviatrix to solve these other cloud networking challenges as well. For example:
- Enterprise-class cloud networking visibility and troubleshooting
- Overcoming overlapping IP issues
- High-performance encryption in the cloud
- Next-Generation Firewall insertion, performance, and visibility in the cloud
- Cloud Networking in AWS, Azure, GCP and OCI
- FQDN Egress Filtering
We'll arrange a Zoom call with you and your team to show how easy it is to get started with a multi-cloud networking approach.
Visit: https://aviatrix.com/schedule-demo/
Related Resources
3-minute Conceptual (Lightboard) overview on ThreatIQ with ThreatGuard: click here
Explainer Video of ThreatIQ/ThreatGuard: click here
3-minute Demo of ThreatIQ/ThreatGuard UI: click here
About Author
Syed Ali is part of the Technical Marketing team at Aviatrix and is an Aviatrix Certified Professional. He is an experienced IT/SI consultant with experience at a Big 4 management consultancy, where he provided systems implementation and strategic advisory services to clients in the public sector, transportation, and consumer packaged goods verticals. He holds MSc Computer Science, BMath, and BBA degrees.
Aside from his interest in cloud networking, Syed is also passionate about community involvement and supporting the growth and development of the emerging workforce and younger generations. He resides in the Toronto, Canada area.
