Introduction
Aviatrix Sandbox Starter Tool (SST) is a community-based and community-supported tool that deploys following small test/lab cloud network environment in minutes.
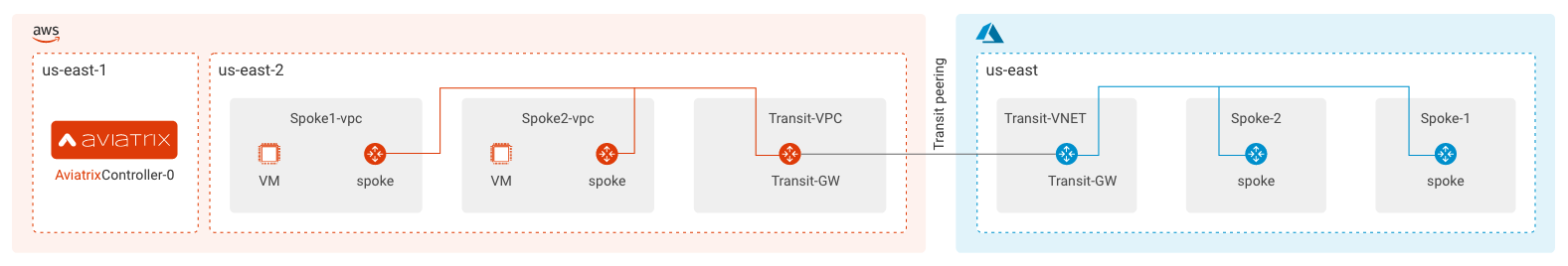
This SaaS like lightweight tool first deploys an Aviatrix Controller in AWS. Once the Controller is up, the tool uses Terraform to create Aviatrix transit (Hub and Spoke) topology in AWS.
Two EC2 test instances will be deployed and connected, that can be used to run test cases, POC or SRE work using the Aviatrix platform with simplicity, automation, visibility, and control.
The self-guided UI workflow can also deploy Azure Network and connect to AWS.
Additional use-cases can then be added directly from Controller UI or Terraform following step by step tool user guide.
SST itself can be deployed using three different options
- AWS EC2 Instance
- This method is documented in this article itself.
- Cloud AMI via Terraform Module
- Local Machine
This document uses the recommended Cloud AMI Option#1 to deploy the SST and Cloud Networks.
Cost
The Sandbox Starter Tool itself is free but there is a cost of running the lab. Please refer to this link for a detailed cost breakdown.
Before You Begin
- You must have AWS Access Key ID and Secret Access Key
- Create EC2 Key Pair name for AWS Ohio and N. Virginia regions
- Subscribe to the Aviatrix Secure Networking Platform Metered 2208-Universal 24x7 Support product from the AWS Marketplace.
- Subscribe to Aviatrix Controller Image
- Subscribe to the Aviatrix CoPilot product from the AWS Marketplace.
Notes:
When subscribing to the platform, you must set up your account after clicking subscribe to generate your controller license key (which will be emailed to the address used in the set up process). This will be used as input to the sandbox starter and subsequently configured during your controller launch.
This tool works the best for a brand new Aviatrix Controller deployment. If you previously deployed Aviatrix Controller, make sure you delete the following first
- Aviatrix EC2 roles
- Aviatrix EC2 policies are deleted
- Delete Aviatrix default key-pair
Launch Sandbox Starter Using AWS EC2 Instance
You can deploy this tool in any AWS region. Make sure you have a proper EIP and VPC quota for your region. In our example, we will be deploying the Sandbox Starter tool in the N. Virginia region (us-east-1).
- Click here for the N. Virginia region EC2 setting
- Click here to search for the Sandbox Starter Public AMI under the Images section and select the latest Sandbox Starter AMI
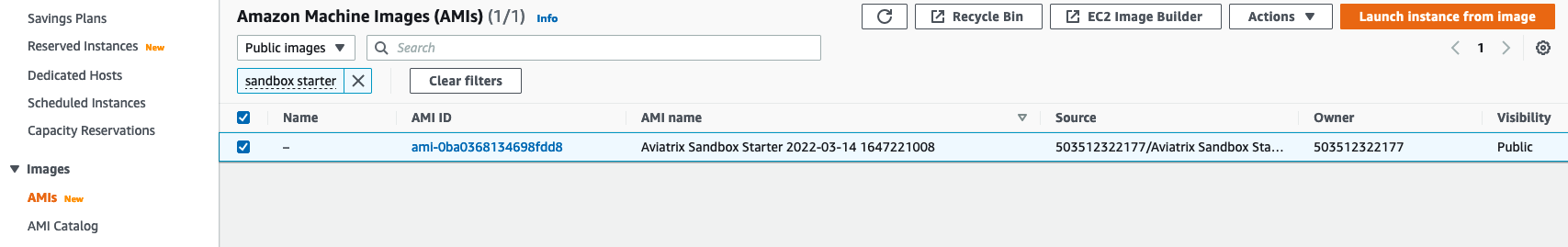
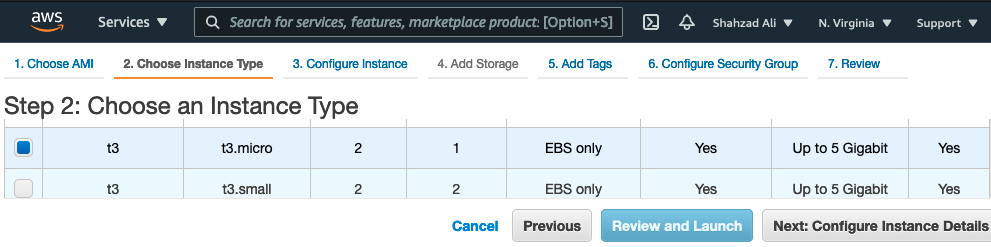
- Click the "Launch Instance from Image" button and select t3.micro or t2.micro instance size
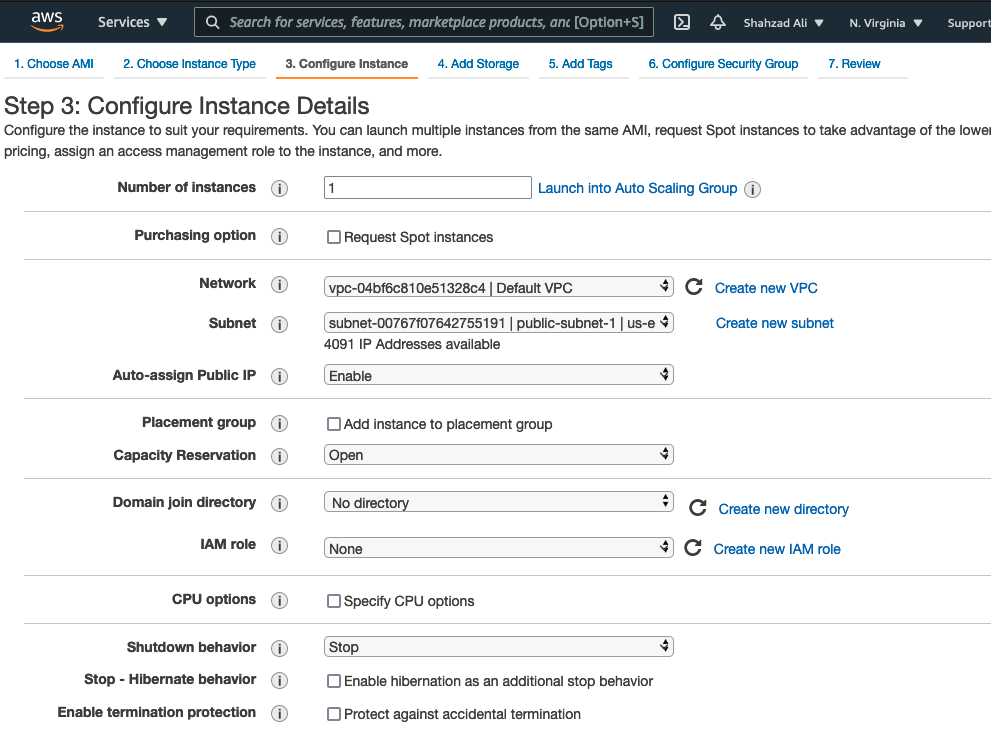
- Click Configure Instance Details and provide the following information. Leave everything else as default
- Network: Select the default VPC.
- Subnet: Select the public subnet
- Auto-assign Public IP: Enable
- Click Add Storage button. Do not change anything here
- Click Add Tags. Do not change anything here
- Click Configure Security Group and block inbound access to SST EC2
- Create a new security group with the following information
- Security Group Name: Aviatrix_Sandbox_Starter_SG
- Delete the SSH TCP 22 rule and add a new HTTPS TCP 443 rule. You must make sure that only your IP address has access to Sandbox Tool
- Ignore the warning
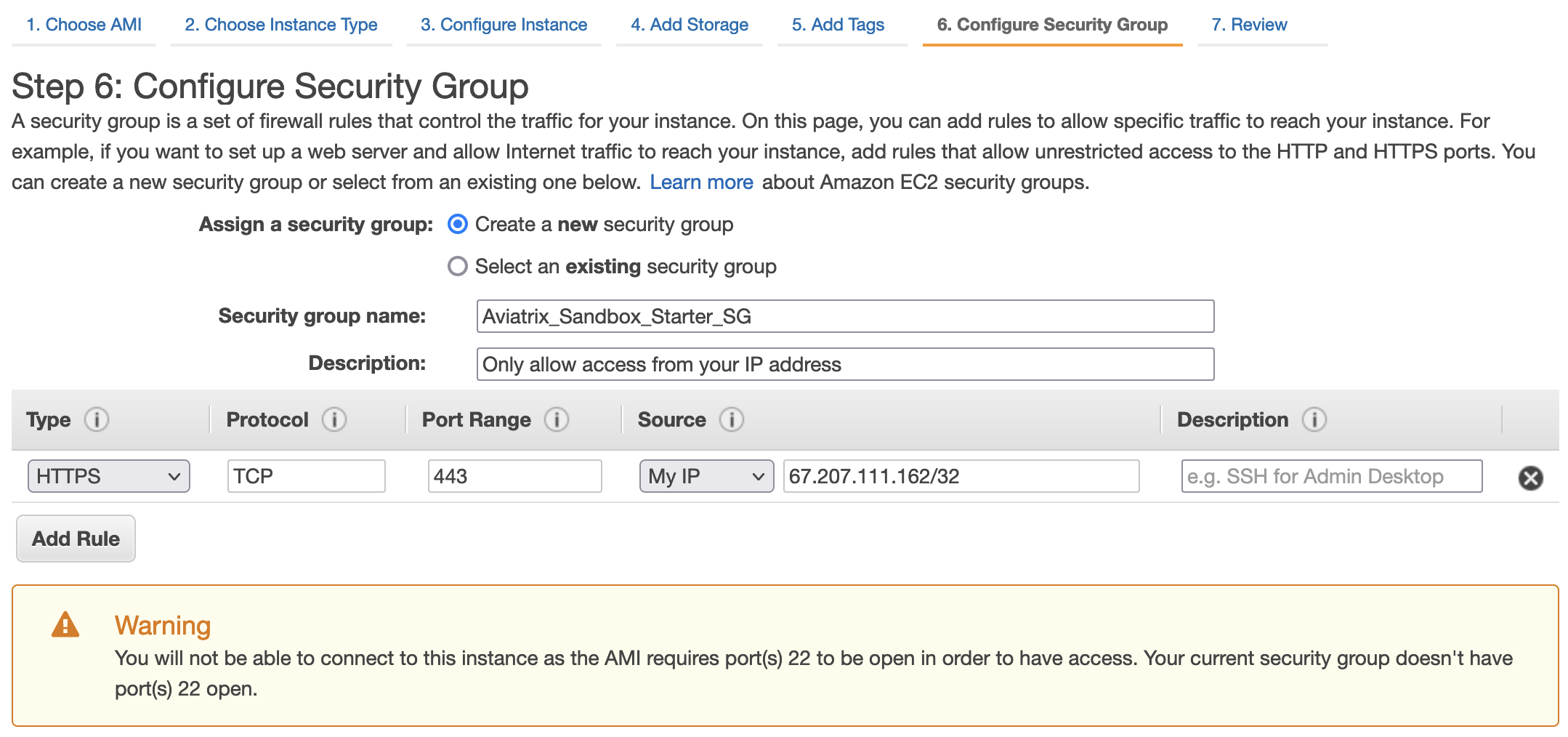
Reference: Authorize inbound traffic for your Linux instances
- Review and launch now
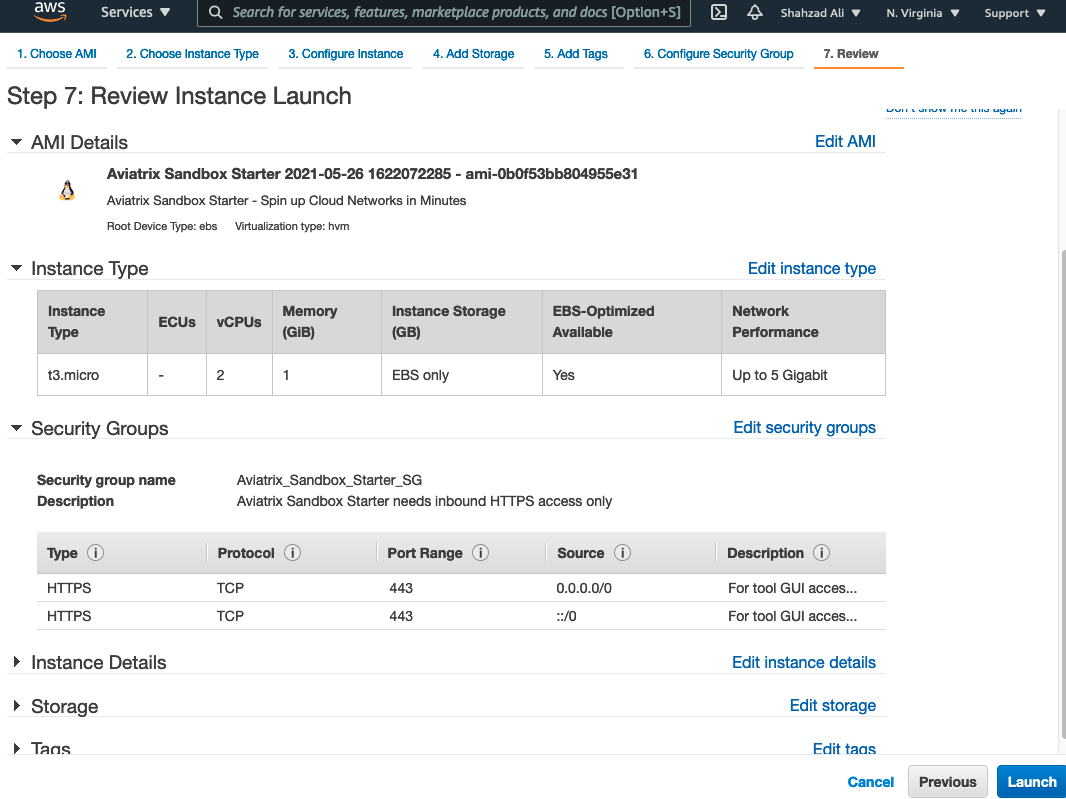
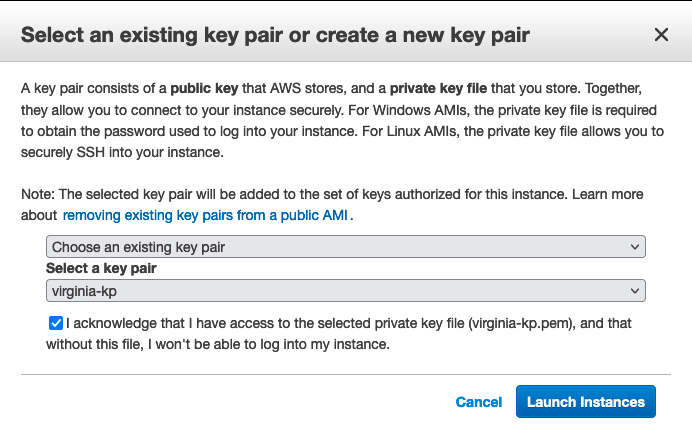
- Select the Key Pair and Launch
- Click on the instance ID to show the details and copy the Public IPv4 address
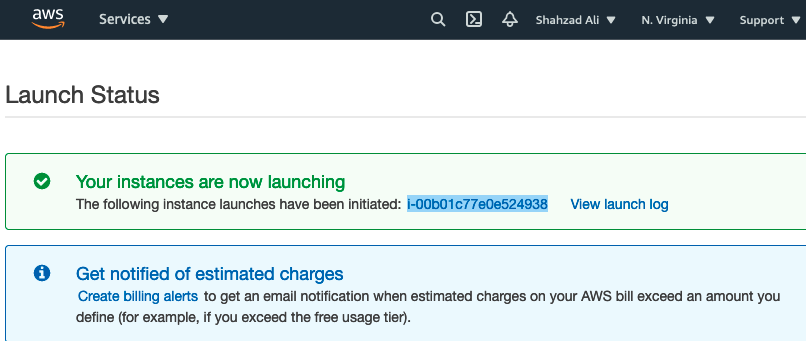
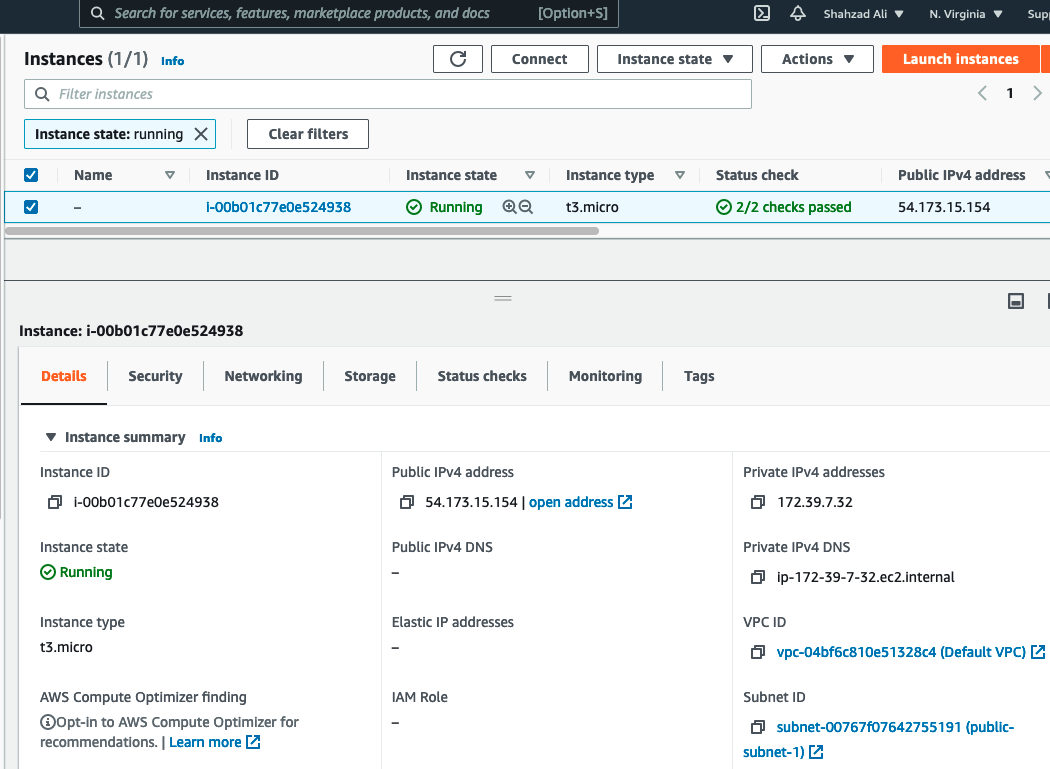
- Once the instance "Running", browse to https://<Public IPv4 address>
- In our example it is https://54.173.15.154/
- The tool uses a self-signed certificate
- Accept the warning and proceed
- If using Chrome and you get a connection error message, you can bypass that by clicking anywhere and typing thisisunsafe
You should see the "Aviatrix Sandbox Starter" user interface (UI) now.
Standard Mode Wizard with AWS
Standard is the recommended workflow. This will deploy the controller and topology in the regions specified in the diagram.
Provide AWS Credentials
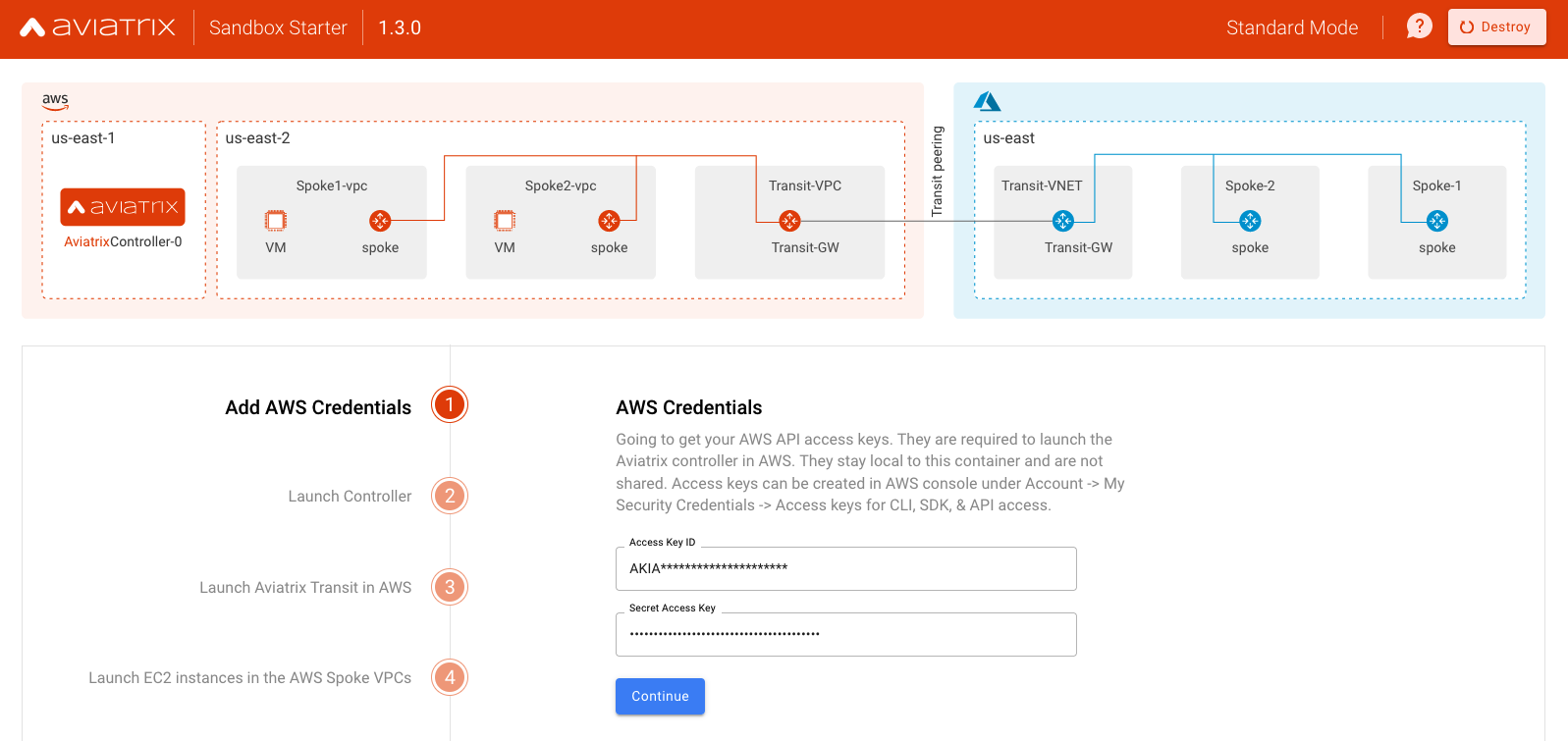
You can get the Access Key under the "Security Credential" area in AWS console. If you don't have one, you should create one.
Launch the Controller in AWS
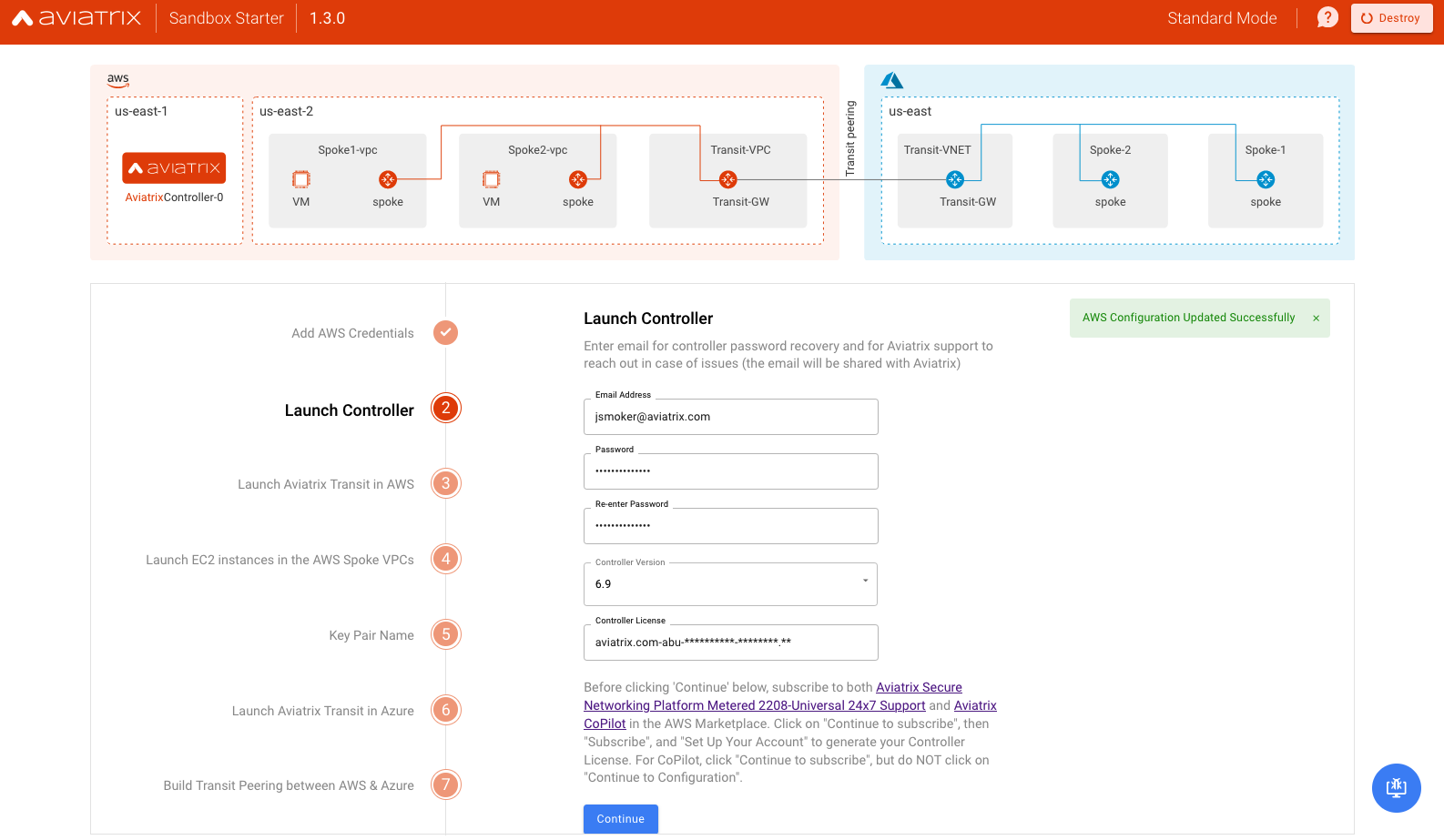
Notes
- The controller version will default to that which is needed for ACE courses. You can choose other available versions with the understanding that they may not be compatible those courses.
- Be sure to subscribe to the AWS marketplace offerings mentioned in the Before You Begin section above and set up your account to generate the Controller License required as input.
- In the future, we might add the option to launch Controller in other Clouds
Launch Global Transit (Hub) and two Spokes in AWS
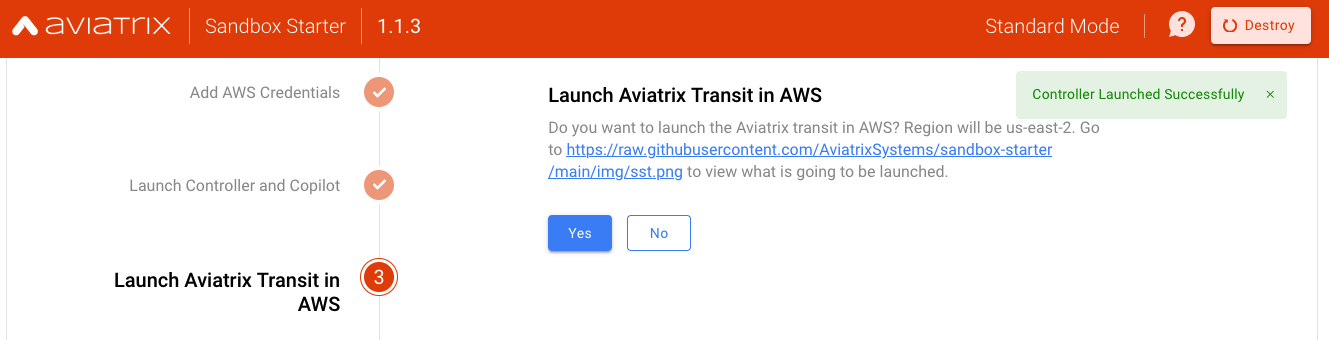
Launch Test EC2 instances
Test EC2 (Amazon Linux VMs) will be launched in their respective Spoke VPCs
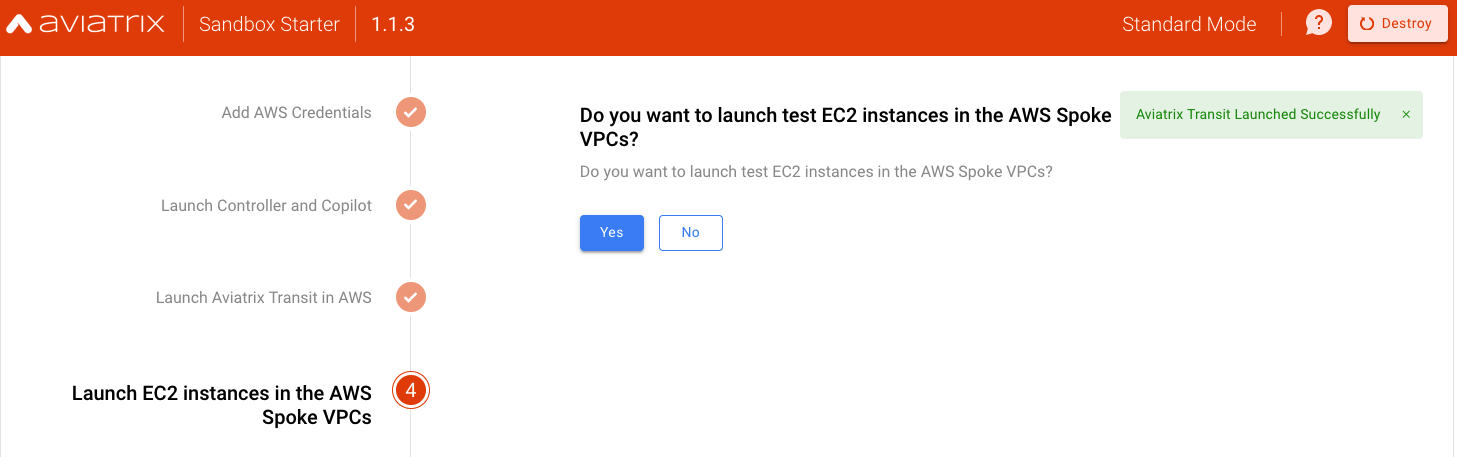
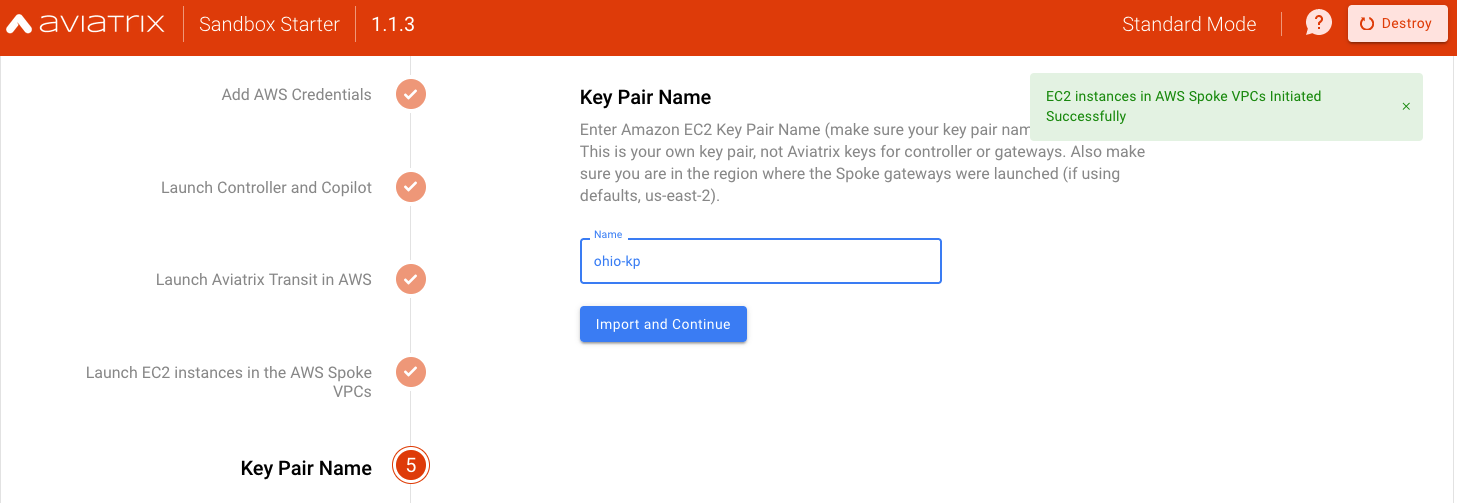
Provide an Existing Key Pair Name
This must be configured in your AWS account in us-east-2 (Ohio) region as per-requisite. You will need this Key Pair to login to test EC2 instances to verify the end-to-end connectivity.
Select No for "Launch Aviatrix Transit in Azure"
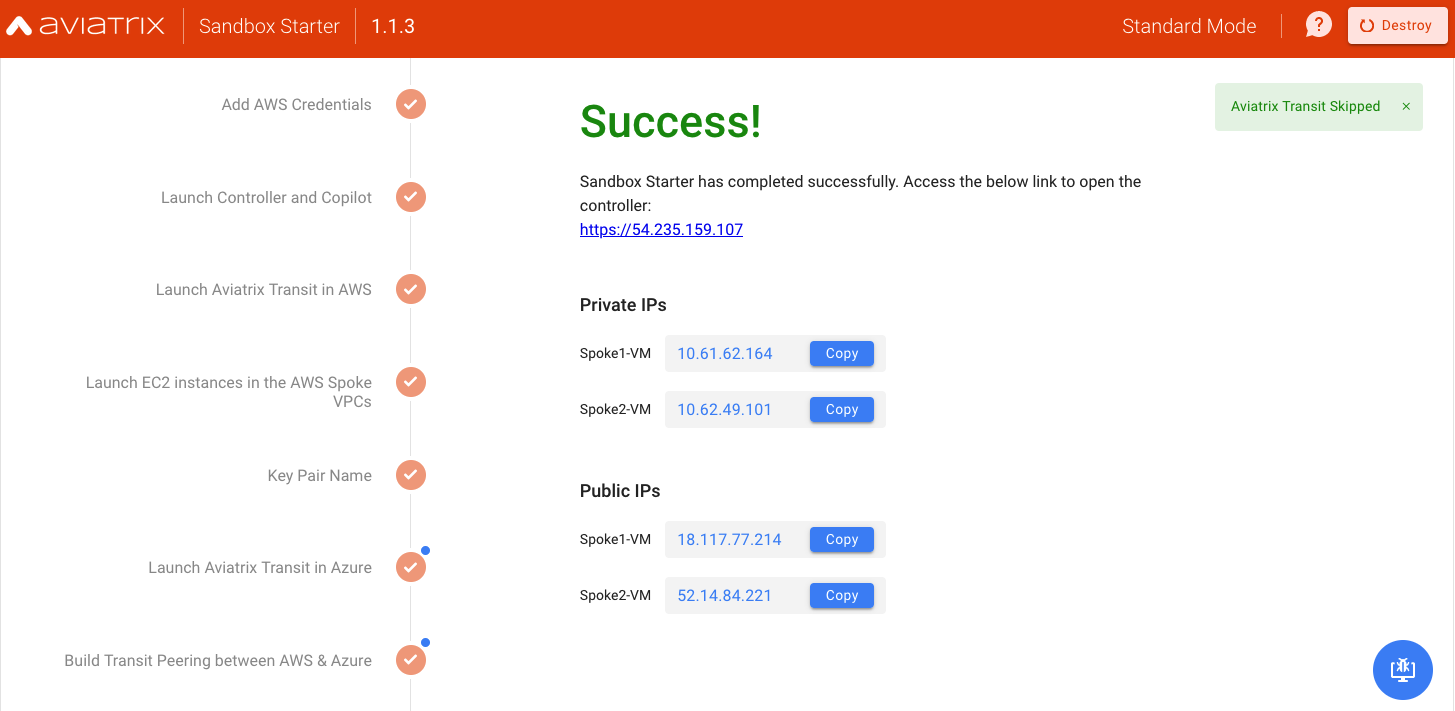
Success Message
Upon success, you will receive the necessary public and private IP addresses. The entire process should take somewhere between 22-30 minutes.
Now you can log in to Aviatrix Controller UI by clicking the controller URL.
Note: The user name is admin and the password is the one you selected earlier in the process.
Lock Inbound Access to Controller
After the Controller is deployed, you must do the following to lock the inbound access so that no one has access to it.
1- Enable the security group management feature so all of the gateways' IP addresses are allowed to reach the controller on HTTPS/port 443
2- Lock all inbound access to Controller except your own IP address
Reference: https://docs.aws.amazon.com/AWSEC2/latest/UserGuide/authorizing-access-to-an-instance.html
Experience the Platform and Deploy Use Cases
Follow the instructions in the Test Plan to experience the Aviatrix Multi-Cloud platform and deploy recommended use case.
- Aviatrix CoPilot - Advance visibility, monitoring, and Observability
- Multi-Account / Multi-Region Capabilities for AWS, Azure, GCP, and OCI
- FlightPath - Transit (Hub-Spoke) architecture advance verification
- Packet Capture - Troubleshooting
- Network Validation - Application Availability
- Create Multi-Region VPC
- Track Rogue VPC using VPC Tracker - Compliance
- Egress FQDN Filtering - Secure Egress Traffic
- User / Client VPN - Policy-Based Access for Employees, Developers, and Partners
Besides that, users are highly encouraged to deploy more use-cases based on their needs and requirement by following the official documentation at https://docs.aviatrix.com
Standard Mode Deployment with AWS and Azure
Azure deployment is optional. You must have an Azure subscription and related information if you are planning on extending the network in Azure.
For Sandbox deployment both in AWS and Azure, follow the video here
Destroy / Delete the entire LAB
Once you are done testing and validating Cloud Networks, you may destroy or delete the entire lab. First, turn off AWS access security on the controller by logging into the controller and clicking on "Settings" in the left-hand nav. Click on "Controller," then "Access Security" in the top tabs. Under "Controller Security Group Management," click "Disable".
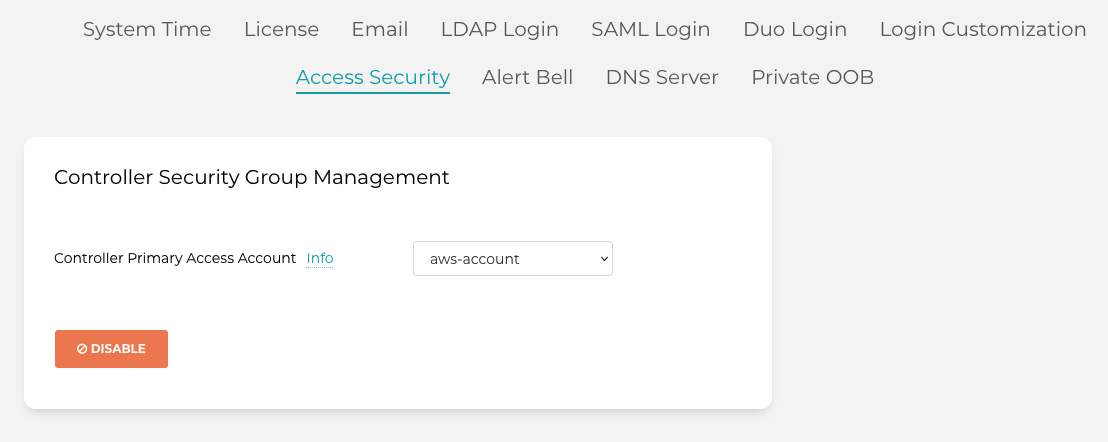
Back in the sandbox starter, use the "Destroy" option on the top right of the browser UI.
If you destroyed SST before getting a chance to destroy your environment, you will need to manually delete these resources in order (always check you are in the appropriate region first):
- Terminate the Spoke and Transit gateways in AWS (if applicable)
- Remove the Resource Groups in Azure (if applicable)
- Disable Termination Protection on the EC2 instance for the Controller
- Terminate the Controller EC2 instance
- Remove the SSH keypair
- Delete the Security Groups
- Delete the VPC where the Gateways and Controller was deployed
- Delete the IAM Roles and Policies starting with ‘aviatrix’
Note that if you deployed CoPilot, it must be deleted manually by logging into AWS/Azure Console.
Support Model
This community-based and open-source tool is NOT supported by the Aviatrix Enterprise support team. For any questions or issues related to this tool, please use the Aviatrix Community platform.
Open Source
- Code for this open-source tool is available at https://github.com/AviatrixSystems/sandbox-starter
- Terraform module for Sandbox Starter launch is available here at https://github.com/terraform-aviatrix-modules/terraform-aviatrix-aws-sandbox-starter
- The container code is available here